Researchers at CYFIRMA have discovered an ongoing malware campaign that uses GitHub, one of the most reliable code repositories on the internet, as a distribution platform in a recent cyber threat study.
The attackers are masking their malicious payload under seemingly benign downloads titled “Free VPN for PC” and “Minecraft Skin Changer,” targeting unsuspecting users searching for free software.
The campaign centers around a dropper executable, Launch.exe, which after execution, covertly deploys the notorious Lumma Stealer malware onto victim machines.
DLL Side-Loading Unveiled
The technical analysis reveals that the main payload, Launch.exe, is a 1.52MB Windows executable with fake assembly metadata likely autogenerated to hinder attributions and bypass heuristic defenses.
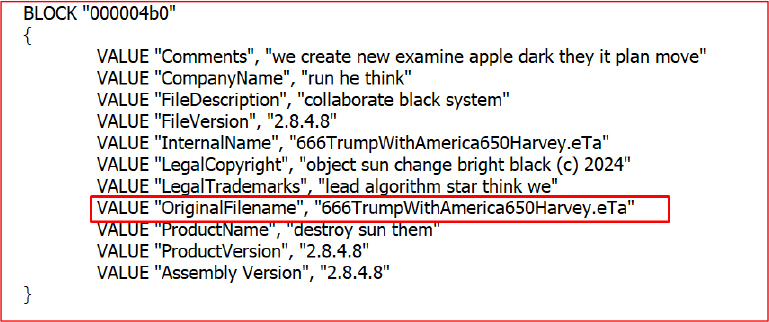
It abuses .NET P/Invoke to import low-level Windows APIs such as LoadLibrary, GetProcAddress, and VirtualAlloc enabling dynamic DLL loading and process memory manipulation.
The dropper uses layered obfuscation: the embedded payload is Base64-encoded and deliberately hidden behind lengthy French text, then decrypted via a custom function that applies bitwise NOT operations and arithmetic obfuscation.

Upon execution, the malware drops a disguised and obfuscated dynamic link library (DLL), msvcp110.dll, into the user’s AppData directory.
The DLL is immediately hidden and then loaded dynamically, executing its exported function GetGameData.
Technical inspection indicates the DLL’s high entropy and anti-debugging measures, such as IsDebuggerPresent checks and convoluted control flow to thwart reverse engineering.
The malware injects itself into legitimate system processes such as MSBuild.exe and aspnet_regiis.exe, evading endpoint defenses through process injection and DLL side-loading.
Network analysis further identified outbound attempts to connect with several suspicious domains, most notably explorationmsn[.]store.
This domain, along with others uncovered in the campaign, matches patterns linked to the broader Lumma Stealer infrastructure known for stealing browser credentials, system information, and cryptocurrency wallets.
Threat Landscape
The threat actors behind the campaign, operating via the GitHub account github[.]com/SAMAIOEC, have uploaded multiple instances of the malware under different filenames to maximize lure potential.
Detailed instructions and password-protected ZIP files accompany these malicious files, which serves to bypass browser-based security scanning and increase the likelihood of successful compromise.
Attribution remains elusive, as the operators have left no identifiable information beyond their GitHub presence.
The attack chain closely aligns with several MITRE ATT&CK tactics and techniques: initial access via drive-by compromise, execution through command and scripting interpreters, privilege escalation and persistence through DLL side-loading, and evasion through obfuscation and masquerading.
Notably, the malware establishes command-and-control (C2) via both application and non-application layer protocols, with encrypted channels to exfiltrate pilfered data.
CYFIRMA’s recommendations for mitigation include proactive blocking of known C2 domains at network boundaries, restricting the download and execution of suspicious executables from open-source repositories, monitoring user directories for unauthorized DLL deployments, and applying YARA rules to endpoints and email gateways.
Enhanced detection of behavioral signs such as side-loaded DLLs, suspicious API invocations, and execution from user space folders combined with robust user awareness campaigns, are urged to diminish attack success rates.
The rise of such sophisticated social engineering campaigns, hosted on reputable platforms like GitHub, underscores the criticality of vigilant threat monitoring and robust external landscape management across organizations.
Indicators of Compromise (IOC)
| No. | Indicator | Type | Context |
|---|---|---|---|
| 1 | acbaa6041286f9e3c815cd1712771a490530f52c90ce64da20f28cfa0955a5ca | EXE | Launch.exe |
| 2 | 15b644b42edce646e8ba69a677edcb09ec752e6e7920fd982979c714aece3925 | DLL | msvcp110.dll |
| 3 | explorationmsn[.]store | Domain | C2 |
| 4 | snailyeductyi[.]sbs | Domain | C2 |
| 5 | ferrycheatyk[.]sbs | Domain | C2 |
| 6 | deepymouthi[.]sbs | Domain | C2 |
| 7 | wrigglesight[.]sbs | Domain | C2 |
| 8 | captaitwik[.]sbs | Domain | C2 |
| 9 | sidercotay[.]sbs | Domain | C2 |
| 10 | heroicmint[.]sbs | Domain | C2 |
| 11 | monstourtu[.]sbs | Domain | C2 |
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates