On August 21, GreyNoise Intelligence detected an unprecedented surge in Remote Desktop Protocol (RDP) reconnaissance activity, as 1,971 unique IP addresses—nearly 400 times the baseline—simultaneously probed both Microsoft RD Web Access and Microsoft RDP Web Client authentication portals.
The uniformity of the client signature and the timing-based enumeration techniques strongly indicate a coordinated campaign designed to discover valid usernames ahead of credential-based intrusions.
Within this spike, 1,851 of the 1,971 IPs shared the same client signature, pointing to a single toolkit or botnet module powering the activity.
Approximately 92 percent of those IPs were already tagged as malicious by GreyNoise, suggesting the infrastructure behind the scanning had been active in other threat operations.
Source analysis revealed that roughly 73 percent of the scanning originated from Brazil, with the United States as the sole target.
Table: Key Metrics of the August 21 Surge
| Metric | Value |
|---|---|
| Baseline daily IP count | 3–5 |
| IPs observed on August 21 | 1,971 |
| Overlap across both RDP tags | 100% |
| IPs sharing uniform client signature | 1,851 (94%) |
| Previously tagged malicious IPs | 1,698 (92% of uniform signature IPs) |
| Primary source country | Brazil (~73%) |
| Target country | United States |
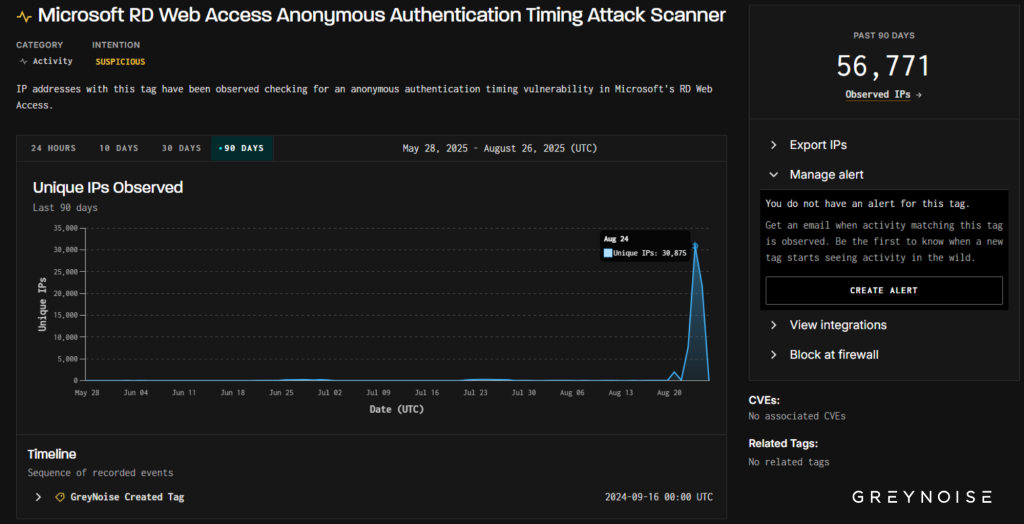
Late on August 24, GreyNoise identified a follow-on wave exceeding 30,000 unique IPs triggering the same RDP tags from the identical client signature, signaling a dramatic escalation in scope.
This broader wave underscores the attackers’ intent to map exposed RDP endpoints en masse and harvest valid account names through timing-based side channels.
The surge occurs amid the U.S. back-to-school window, when educational institutions bring hundreds of remote labs and RDP-backed environments online.
Predictable username schemes—student IDs and firstname. lastname formats—combined with under-resourced IT teams create a fertile landscape for enumeration attacks.
By confirming valid usernames, adversaries dramatically improve the efficiency of follow-on credential stuffing, password spraying, and brute-force efforts.
RDP enumeration precedes critical exploitation events. Historical examples include the BlueKeep (CVE-2019-0708) campaign, which moved from scanning to widespread exploitation within weeks, as well as documented RDP abuse by espionage actors and ransomware groups such as SamSam.
Research shows that 80 percent of new vulnerabilities are disclosed within six weeks of a spike in scanning activity, highlighting the urgency for defenders to act.
Organizations with exposed RD Web Access and RDP Web Client portals should immediately review and harden authentication workflows.
Mitigations include enforcing multi-factor authentication, limiting access to known IP ranges, enabling account lockout thresholds, and monitoring for unusual timing-based anomalies.
GreyNoise continues to track this activity and will update its dynamic IP blocklist service to help security teams respond faster to emerging threats.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates