Security researchers have uncovered a sophisticated phishing campaign that leverages fake Microsoft OneNote login pages to harvest Office365 and Outlook credentials from targeted users.
The operation, which has been active since January 2022, primarily targets Italian organizations and employs Telegram bots for data exfiltration, demonstrating a concerning evolution in credential theft techniques.
The attack begins with victims receiving phishing pages hosted on legitimate platforms like Notion workspaces, designed to appear as document-sharing invitations.
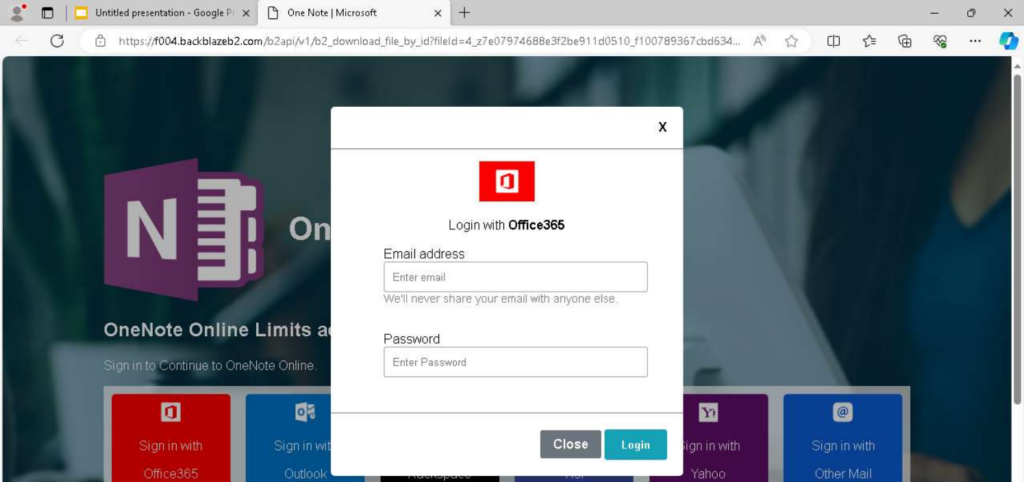
When users attempt to access the alleged shared document, they are redirected to fraudulent login pages hosted on services like Glitch.me that closely mimic Microsoft OneNote authentication prompts.
These malicious pages present multiple authentication options including Office365, Outlook, Rackspace, and Italy’s PEC (Posta Elettronica Certificata) system.
Once credentials are entered, the phishing infrastructure executes several malicious actions simultaneously.
The system captures the victim’s IP address using the ipify.org service and immediately exfiltrates both the stolen credentials and location data through hardcoded Telegram bot APIs.
The technical analysis revealed that attackers embed bot tokens and chat IDs directly into the phishing scripts, with researchers identifying multiple bots including “Sultanna” (@Sultannanewbot) and “remaxx24” (@remaxx24bot) used for data collection.
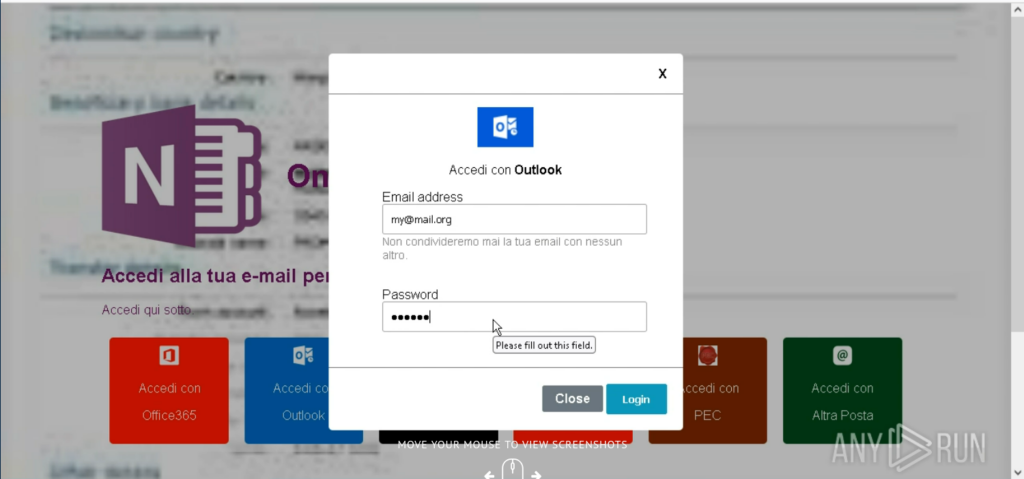
After credential theft, victims are redirected to legitimate Microsoft login pages to maintain the illusion of authenticity and avoid immediate detection.
Italian Organizations Primary Target
The campaign demonstrates a clear focus on Italian-speaking users and organizations, with phishing content specifically crafted in Italian and subdomain names incorporating Italian terminology.
Security researchers analyzing intercepted Telegram communications identified numerous affected domains including aedsrl.it (warehouse logistics), legalmail.it (certification authority), steelsystembuilding.it (logistics services), and gruppoamag.it (public utilities).
The operation’s timeline spans over three years, with the oldest identified sample dating back to January 29, 2022.
Throughout this period, the campaign has evolved its techniques, initially using web form submissions for data exfiltration before transitioning to Telegram-based methods in February 2022.
The attackers have experimented with various obfuscation techniques, including nested URL encoding and Base64 obfuscation, though they maintain relatively simple evasion mechanisms.
Researchers noted the campaign’s low operational tempo and reliance on free platforms for hosting malicious content, including Notion, Glitch, Google Docs, and RenderForest.
This approach suggests either limited technical sophistication or a deliberate strategy focusing resources on access brokering rather than advanced phishing infrastructure.
Security Researchers Provide Detection Guidelines
Based on their analysis, security experts recommend implementing several detection measures to identify this ongoing threat.
Organizations should monitor for suspicious domain chains following the pattern “Notion → Glitch → Telegram API” and establish signature-based detection rules for identifying Telegram bot activity within corporate network traffic.
The research team successfully intercepted attacker communications by exploiting the Telegram bot infrastructure, revealing active credential theft operations affecting both Italian and American organizations.
This technique allowed researchers to quantify the campaign’s scope and confirm its continued operation as of April 2025.
The campaign’s primary objective appears to be credential harvesting for potential access brokering within cybercriminal ecosystems, targeting Microsoft 365 services and Italy’s certified email infrastructure.
Security professionals emphasize the importance of monitoring for the specific tactics, techniques, and procedures associated with this threat actor to prevent further credential compromise.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.