The rise of online casino spam has become one of the most dominant trends in website compromises over the past few years. Cybercriminals are exploiting WordPress websites to inject hidden backlinks that manipulate search results and drive traffic to illegal or unregulated gambling platforms.
This blackhat SEO tactic, once dominated by pharma and essay-writing scams, has now mainly shifted to online casinos seeking rapid growth and visibility.
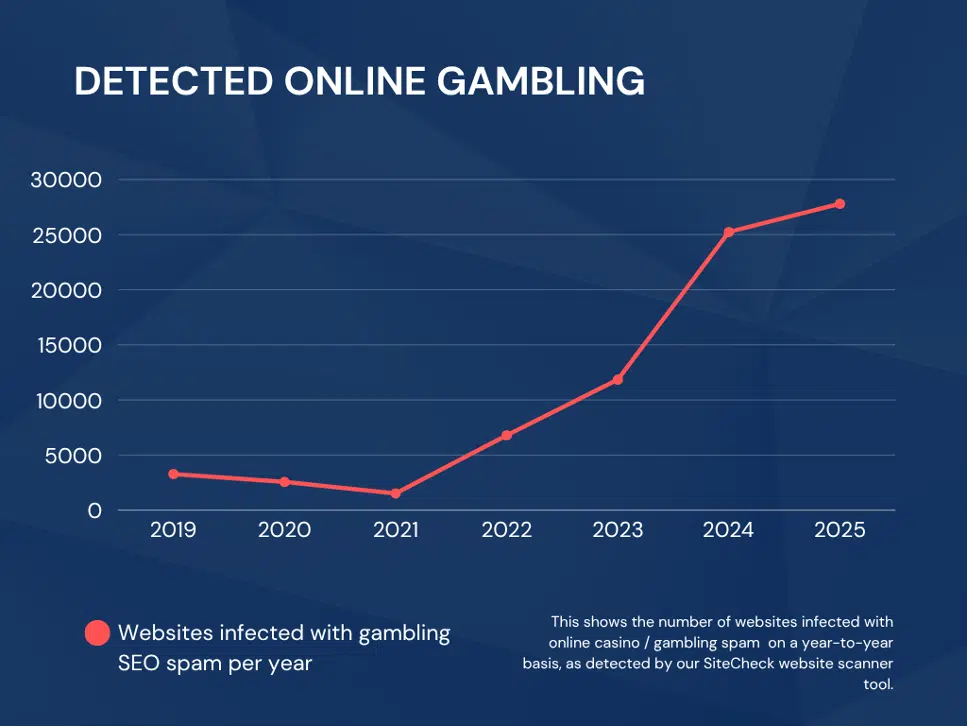
The Surge of Online Casino Spam
Online casino spam began gaining traction during the COVID-19 lockdowns of the early 2020s. As physical casinos closed, the online gambling industry exploded, providing a fertile ground for opportunistic threat actors.
Data from the Sucuri SiteCheck malware scanner reveals that detections of gambling-related SEO spam have increased steadily since 2021, surpassing even long‑standing threats such as Japanese SEO spam.
The motivation is clear: online casinos generate significant profits with minimal infrastructure costs. With a global audience and no physical limits on capacity, every infected website serves as a new promotional gateway.
Even a single backlink from a high‑authority domain can improve a website’s search rankings, making website hijacking an attractive vector for sustained SEO manipulation.
Technical Breakdown of the Infection
Recent analyses uncovered a sophisticated infection targeting WordPress websites. The malware inserts base64‑encoded payloads across multiple layers for persistence and redundancy.
Malicious code was typically implanted in both the active theme’s functions.php file and a legitimate plugin such as astra-addon.php. It also leveraged WordPress’s wp_options database entries and hidden cache files (style.dat) under wp-content/cache.
When a user visits certain pages, such as compromised directories like /programs or /about the injected script calls content from an attacker-controlled command‑and‑control domain (browsec[.]xyz) to dynamically load casino-related spam, primarily targeting Indonesian audiences.
If administrators remove any component, the infection can reinfect itself using a reinfection logic that appends malicious code back to deleted files.
The script checks for a marker _wp_deferred_style_commit to determine whether reinjection is necessary, demonstrating a deliberate and layered evasion approach.
Global Reach and Implications
Unlike traditional English‑language SEO spam, the latest campaigns are multilingual, with a noticeable focus on countries such as Indonesia, Thailand, and Turkey, regions with strict gambling bans but large online populations. This makes illegal online casinos particularly profitable targets for spam operators.
Defenders are urged to maintain regular malware scans, monitor unexpected base64 or eval() calls in WordPress themes and plugins, and ensure database integrity.
Removing infected directories alone is no longer sufficient; persistent reinfection techniques require a full‑stack remediation strategy that involves both file-system and database cleanup.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates