Security researchers at Eclypsium have uncovered a critical vulnerability that transforms ordinary Linux-powered webcams into sophisticated attack tools, marking the first known case where USB peripherals already connected to computers can be remotely weaponized without physical manipulation.
The research, presented at DEF CON 2025 by Jesse Michael and Mickey Shkatov, demonstrates how attackers can exploit firmware validation flaws in select Lenovo webcam models to create persistent BadUSB attack vectors that survive complete system reinstallations.
Vulnerability Discovery and Impact
The vulnerability affects two specific Lenovo webcam models: the 510 FHD Webcam and the Performance FHD Webcam, both manufactured by SigmaStar using the SSC9351D system-on-chip.
These devices run Linux on a dual-core ARM Cortex-A7 processor with embedded DDR3 memory, creating an unexpected attack surface that traditional security tools cannot monitor.
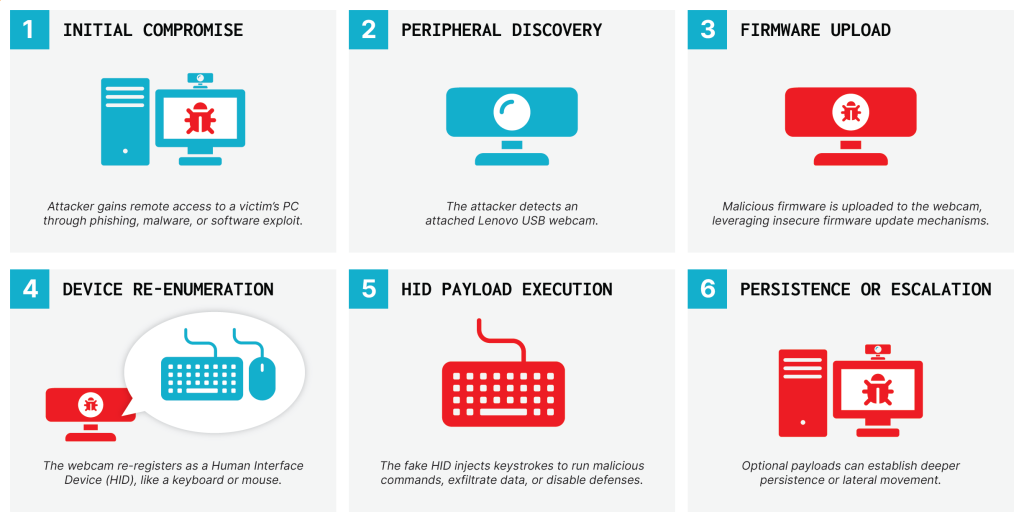
Unlike conventional BadUSB attacks that require physical device insertion, this firmware-based compromise enables two distinct attack vectors.
Attackers can either distribute pre-compromised webcams or remotely infect already-connected devices through system compromise.
Once weaponized, these cameras maintain their original functionality while secretly operating as Human Interface Devices (HID), capable of injecting keystrokes and executing malicious commands.
The vulnerability stems from the complete absence of firmware signature validation during update processes.
The Linux USB gadget framework, designed to allow devices to present themselves as various USB peripherals, becomes the primary enabler for this attack methodology.
Technical Details and Attack Methods
The attack exploits the webcam’s firmware update mechanism through a series of unvalidated USB commands.
The vulnerable update process involves direct manipulation of the device’s SPI flash memory:
bashsf probe 0
sf erase 0x50000 0x7B0000
tftp 0x21000000 lenovo_hd510_ota_v4.6.2.bin
sf write 0x21000000 0x50000 0x7B0000
This command sequence completely erases the 8MB onboard flash storage and writes attacker-controlled firmware directly to the device.
The compromised webcam runs Linux kernel version 4.9.84 with full USB gadget support, enabling it to masquerade as keyboards, network adapters, or storage devices while maintaining its camera functionality.
The persistence mechanism proves particularly concerning.
Even after a complete host system reinstallation, the weaponized webcam retains its malicious capabilities and can immediately re-infect clean systems.
This creates an unprecedented level of persistence that bypasses traditional endpoint protection and system recovery procedures.
Mitigation and Response
Lenovo has collaborated with SigmaStar to address the vulnerability through CVE-2025-4371, releasing updated firmware installation tools that implement proper signature validation.
The company now provides firmware version 4.8.0 for both affected webcam models through their support portal.
The broader implications extend beyond these specific devices.
Security researchers warn that numerous USB peripherals running Linux with similar architectures may harbor identical vulnerabilities.
The USB gadget framework implementation across embedded devices creates a potentially vast attack surface that organizations must now consider.
Organizations should immediately inventory Linux-powered USB peripherals, implement firmware validation policies, and consider hardware attestation mechanisms.
The discovery fundamentally challenges existing trust models between host systems and connected peripherals, demanding comprehensive reevaluation of endpoint security strategies in environments where USB devices can autonomously execute code and persist across system rebuilds.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates