In an era of escalating cyberattacks, security operations centers (SOCs) and managed security service providers (MSSPs) are turning to advanced threat hunting techniques to stay ahead of sophisticated adversaries.
ANY.RUN’s Threat Intelligence Lookup (TI Lookup) has emerged as a game-changer, empowering analysts with rapid access to indicators of compromise (IOCs), behavioral indicators (IOBs), and attack indicators (IOAs) sourced from a global sandbox environment.
By leveraging flexible query syntax and comprehensive data correlation, SOC teams can now detect, triage, and contain threats with unprecedented speed and precision.
Threat Intelligence Lookup Capabilities
TI Lookup delivers access to a vast repository of real-world malware samples and IOC feeds, contributed by more than half a million security professionals.
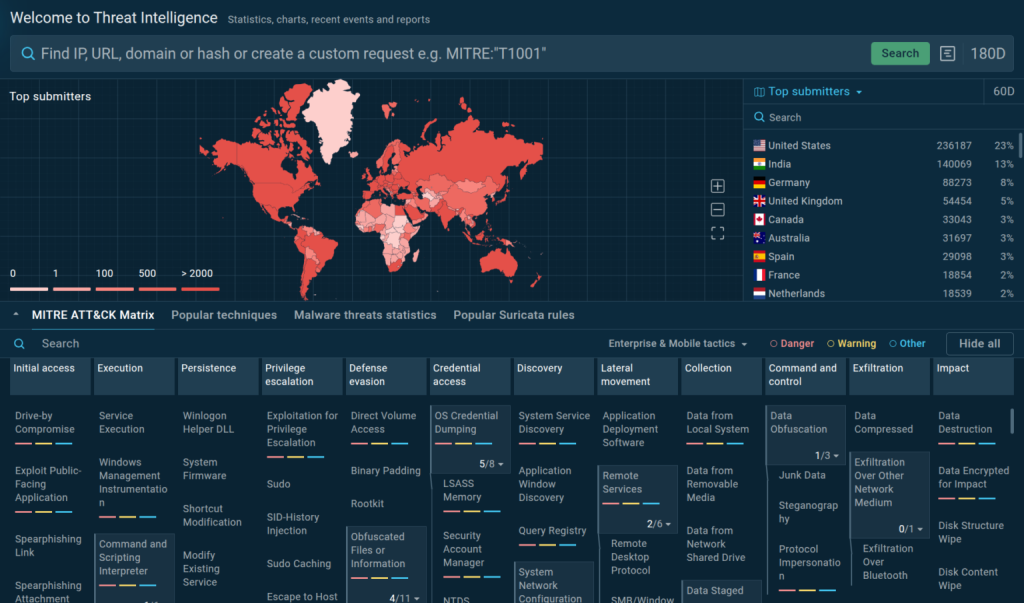
Analysts can perform IOC lookups—searching IP addresses, file hashes, URLs, and domain names—and behavioral lookups that surface registry modifications, process activities, network communications, and mutex creations.
Integration of the MITRE ATT&CK framework enables searches by tactic and technique (TTP), from command and script execution (T1059) to registry-based persistence (T1547).
Wildcards and logical operators (AND, OR, NOT) facilitate complex queries, while YARA-based hunting refines searches by file patterns and characteristics.
File/event correlation further contextualizes alerts, helping teams link disparate artifacts into coherent attack narratives.
Hands-on Use Cases for SOC Analysts
Analysts employ TI Lookup for targeted threat hunting through a series of specialized queries:
- Country-based detection: Filtering by
submissionCountryandthreatLevelpinpoints regional phishing campaigns or PowerShell-driven malware outbreaks. - MITRE technique queries: Combining
MITRE:"T1059"withcommandLine:"powershell"orimagePath:"mshta.exe"surfaces samples leveraging legitimate system tools for malicious execution. Correlating multiple techniques—such as process injection (T1055), system information discovery (T1082), and persistence (T1547)—uncovers sophisticated multi-stage attacks. - Obfuscated file behavior: By excluding standard paths (
NOT filePath:"Windows*") and targeting script extensions (fileExtension:"js"withcommandLine:"powershell"), analysts isolate executables and scripts employing obfuscation. - Domain Generation Algorithm (DGA) detection: Queries for unusual TLDs (e.g.,
.top,.xyz) over HTTP/HTTPS, or Cloudflare-hosted domains (domainName:".workers.dev"), reveal dynamic domains used in C2 communications. - Mutex and persistence analysis: Searching for
syncObjectName:"rmc"uncovers Remcos trojan samples using mutexes for single-instance control, while YARA rules spotlight persistence mechanisms in registry Run keys.
Strategic Impact for SOCs and MSSPs
By slashing mean time to respond (MTTR) and enriching alert triage with contextual insights, TI Lookup accelerates threat detection and containment.
Thematic query subscriptions keep analysts informed of emerging credential stealers—such as RedLine, Lumma, and Formbook targeting the SAM registry—and other high-risk campaigns.
This proactive posture enables security teams to prioritize high-impact threats, reduce false positives, and safeguard business operations.
As cyber adversaries continually evolve evasion tactics, the flexibility and depth of TI Lookup’s query engine ensure that SOC analysts and MSSPs remain on the front lines of defense, armed with the actionable intelligence needed to outpace modern threats.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates