A new and sophisticated cyber threat actor, dubbed Hazy Hawk, has emerged as a major risk to organizations worldwide by hijacking abandoned cloud resources through DNS misconfiguration.
Since at least December 2023, Hazy Hawk has targeted high-profile domains—including those of the US Centers for Disease Control (CDC), Deloitte, PricewaterhouseCoopers, and major universities—by exploiting dangling DNS CNAME records that point to discontinued cloud services such as Amazon S3 buckets and Microsoft Azure endpoints.
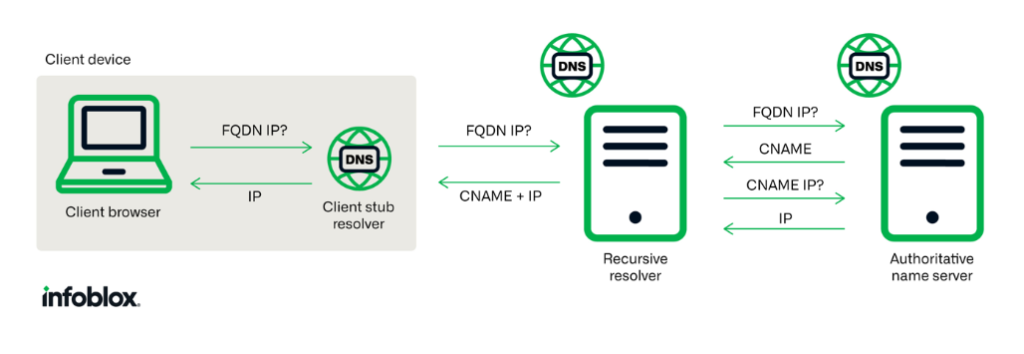
The technical core of these attacks lies in the misuse of the DNS CNAME record, which acts as an alias pointing one domain to another. When a CNAME record remains active after its associated cloud resource is decommissioned, it becomes “dangling.”
Attackers can then register a new resource with the same name in the relevant cloud provider, instantly gaining control over the subdomain.
For example, in the CDC incident, the subdomain ahbazuretestapp.cdc.gov was aliased to an abandoned Azure site.
Hazy Hawk registered a new Azure site with the same name, effectively hijacking the CDC’s subdomain for malicious purposes.
From Hijacked Domains to Malware: A Multi-Layered Scam Ecosystem
Once Hazy Hawk commandeers a reputable subdomain, it leverages the trust inherent in these domains to distribute scams, malware, and unwanted push notifications.
The initial hijacked URLs are often cloaked using traffic distribution systems (TDS), which dynamically redirect users through multiple layers, including link shorteners (Bitly, TinyURL), Blogspot pages, and additional compromised domains, before delivering the final payload.
A typical attack chain might look like this:
- The victim clicks a seemingly legitimate link (e.g., a CDC subdomain).
- The browser is redirected through several obfuscated URLs, often using services like Blogspot or link shorteners.
- The user lands on a scam site, which may prompt for browser notification permissions or attempt to deliver malware.
- If the user accepts push notifications, their device may be bombarded with scam alerts, tech support fraud, or fake survey requests, powered by affiliate adtech networks such as RollerAds.
Hazy Hawk further complicates detection by cloning legitimate website content or mimicking the look and feel of the original organization’s site, making it difficult for both users and security crawlers to distinguish between authentic and malicious pages.
In some cases, the group even obfuscates the names of hijacked AWS S3 buckets within URLs to evade security filters.
Economic and Security Impact: Defending Against Hazy Hawk
The financial and reputational damage caused by Hazy Hawk is substantial.
The U.S. Federal Trade Commission reported a 25% increase in scam-related losses in 2023, totaling $12.5 billion, with a significant proportion attributed to the types of fraud facilitated by such hijacks, particularly impacting the elderly.
By leveraging trusted domains, Hazy Hawk’s operations not only evade conventional security measures but also boost their scam sites’ credibility in search results.
Key technical terms and codes:
- CNAME Record: A type of DNS record that maps one domain to another.
- Dangling DNS Record: An active DNS record pointing to a non-existent or abandoned resource.
- Traffic Distribution System (TDS): Infrastructure used to redirect web traffic through multiple intermediary sites, often for obfuscation and monetization.
- Push Notification Scam: A method where malicious sites prompt users to enable browser notifications, later used to deliver scams or malware.
Prevention strategies include:
- Regularly auditing and promptly removing DNS records associated with discontinued cloud resources.
- Implementing protective DNS solutions that block access to known malicious domains, even as threat actors rotate domain names.
- Educating users to deny notification requests from unfamiliar websites and to recognize suspicious redirect chains.
As cloud adoption grows, organizations must prioritize DNS hygiene and cloud asset management to prevent falling victim to sophisticated threats like Hazy Hawk.
The rise of such attacks underscores the critical need for cross-team coordination and continuous monitoring in the evolving cyber threat landscape.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates