A sophisticated HTTP request smuggling attack that exploits inconsistent parsing behaviors between front-end proxy servers and back-end application servers.
The vulnerability leverages malformed chunk extensions in HTTP/1.1 transfer encoding to bypass security controls and inject malicious secondary requests.
Following responsible disclosure, comprehensive security patches have been deployed across affected systems, protecting organizations that maintain current software versions against this attack vector.
The newly discovered technique targets the HTTP/1.1 chunked transfer encoding mechanism, specifically exploiting inconsistencies in how different servers parse chunk extensions.
According to RFC 9112 Section 7.1.1, chunk extensions should follow specific syntax rules, where semicolons must be followed by extension names and optional values.
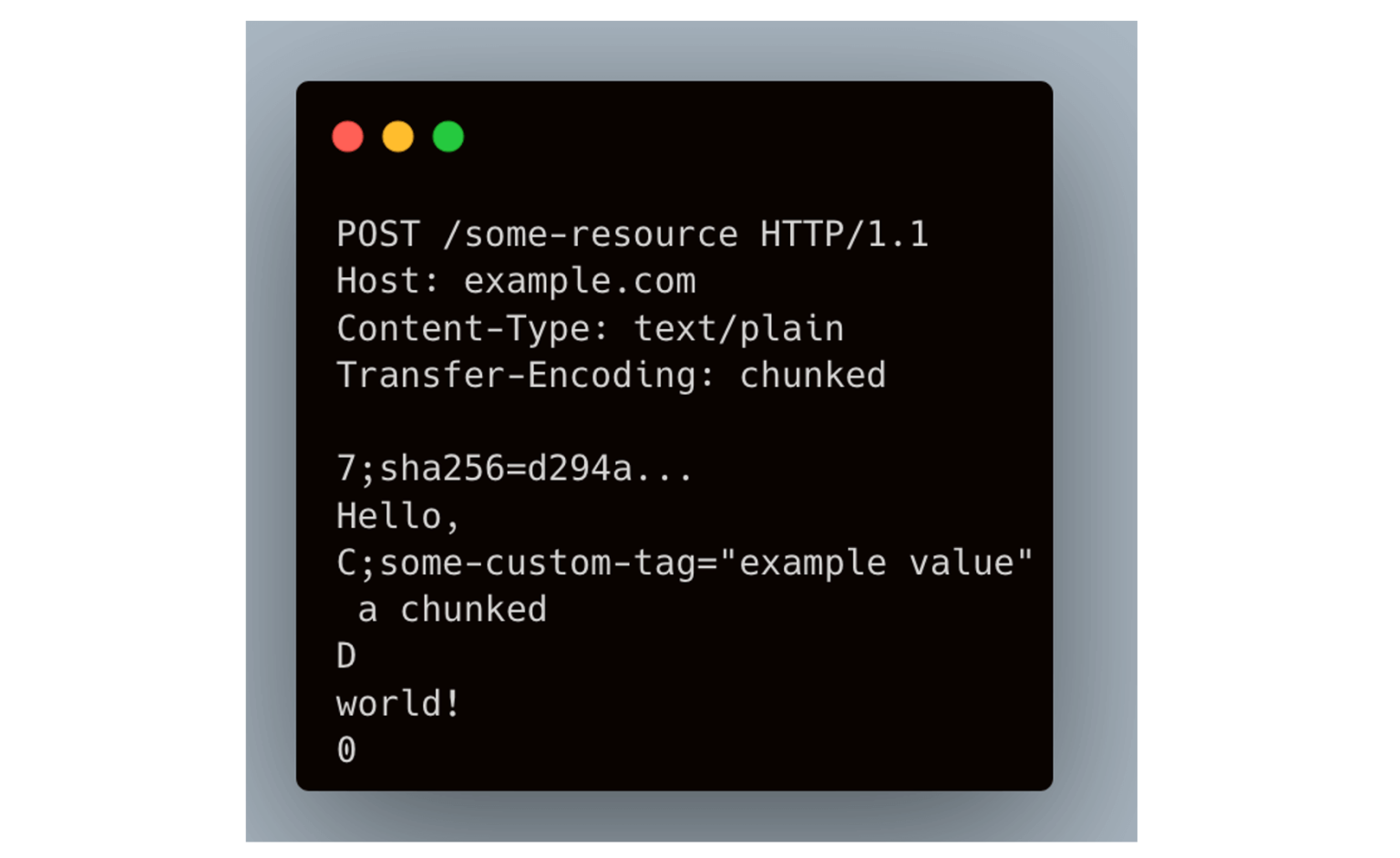
The attack operates through a carefully crafted sequence where attackers send malformed chunk extension headers containing bare semicolons without proper extension names.
This creates a parsing discrepancy between front-end and back-end systems. The front-end parser typically ignores the malformed extension and treats the entire sequence as a single request, while the back-end parser interprets the newline following the semicolon as the end of the chunk header.
By embedding a secondary HTTP request after a zero-length chunk, attackers can effectively smuggle requests past front-end security controls.
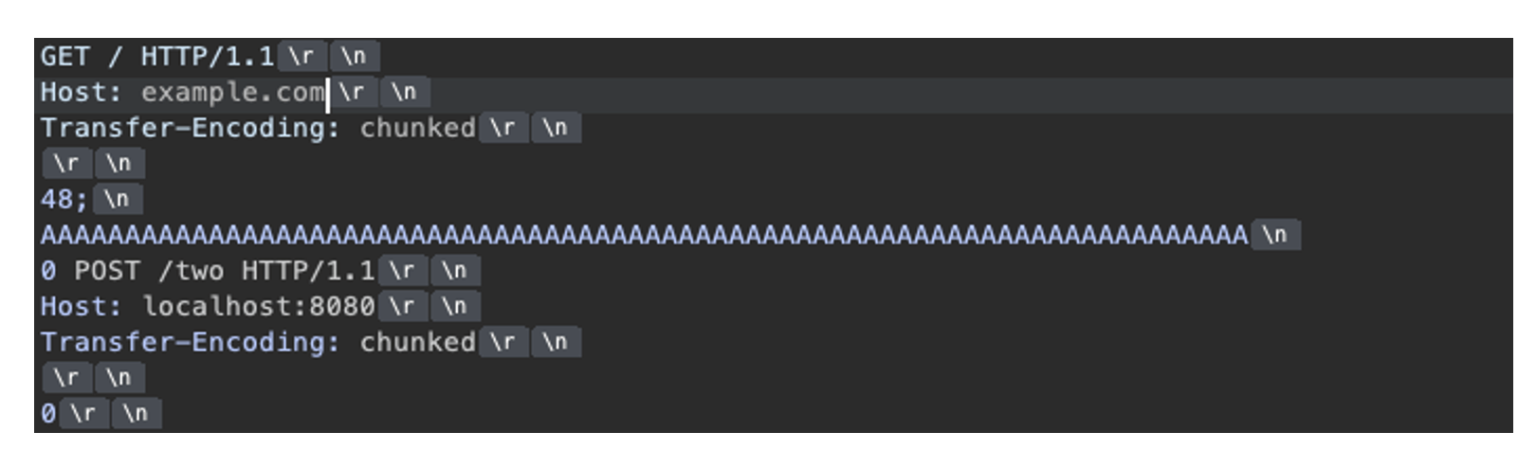
The back-end server processes this smuggled content as a legitimate new request, potentially granting access to restricted resources or bypassing authentication mechanisms that the front-end would have blocked.
HTTP Smuggling Technique
The fundamental vulnerability stems from HTTP/1.1’s text-based protocol design and its multiple methods for expressing message boundaries, including Content-Length headers, Transfer-Encoding chunked format, and various delimiters.
While RFC specifications define strict parsing rules, real-world implementations often exhibit variations due to different development timelines and interpretations.
Server implementations frequently employ lenient parsing to maintain compatibility with diverse client behaviors, accepting slightly malformed requests rather than rejecting them outright.
This tolerance creates subtle parsing differences between systems, particularly for rarely used features like chunk extensions, which developers often handle inconsistently or with insufficient RFC compliance.
The parsing ambiguities become exploitable when front-end proxies and back-end servers disagree on request boundaries.
Cloud WAF and on-premises WAF customers with updated software are now protected against this specific vulnerability variant.
These inconsistencies enable attackers to craft requests that appear as single messages to upstream security controls while being interpreted as multiple separate requests by downstream processing servers.
Mitigations
Comprehensive security patches have been successfully deployed across all affected systems, ensuring full protection for organizations maintaining current software versions.
Recent research, including PortSwigger’s analysis on HTTP/1.1 vulnerabilities, demonstrated that the older protocol remains fundamentally susceptible to new attack variants that continuously bypass existing protections.
Security researchers emphasize that the most effective long-term mitigation involves migrating to HTTP/2 protocol.
Unlike HTTP/1.1’s text-based structure, HTTP/2 employs binary framing mechanisms that eliminate the ambiguous parsing scenarios enabling request smuggling attacks.
Organizations should prioritize HTTP/2 migration not only for performance improvements but as a critical security enhancement addressing these protocol-level vulnerabilities.
The incident reinforces the importance of maintaining current security patches and evolving protocol standards to defend against sophisticated attack vectors targeting web infrastructure parsing inconsistencies.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.