A new wave of infostealer malware has emerged, leveraging a clever social engineering trick dubbed “ClickFix” to infect both Windows and macOS users.
Researchers have identified this campaign as dangerously effective, as cybercriminals entice victims to unwittingly execute malicious commands, allowing thieves to harvest credentials, personal data, and financial information on a massive scale.
ClickFix: A Clever Social Engineering Tactic
Unlike traditional phishing, ClickFix attacks bypass email security solutions entirely. Instead, adversaries lure victims through organic search results, malicious web pages, and direct messages on social platforms.
The central ploy is simple yet effective: a victim is convinced to run a command or script in their command line, ostensibly to pass a security check or unlock cracked software. In many cases, attackers use pages that mimic legitimate Cloudflare security checks.
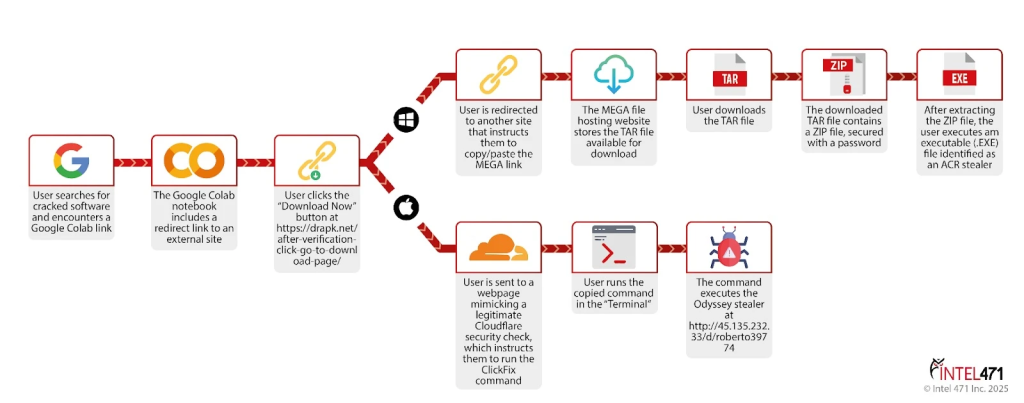
These contain instructions for users to run a terminal command that pulls a hidden malware payload directly into the computer’s memory. This technique is typically invisible to most security solutions until endpoint detection and response (EDR) software activates.
Technical analysis shows the commands are Base64-encoded and, when decoded, use curl or similar utilities to fetch an executable or shell script from remote servers. The payload, deployed as a clean fileless process, enables infostealers such as ACR for Windows and Odyssey for macOS.
These stealers are highly effective at exfiltrating login credentials, browser cookies, wallet keys, and other sensitive data to attacker-controlled infrastructure, allowing logs of compromised data to proliferate on underground markets like Russian Market.
Attack Chain and Payloads: Windows and macOS Targeted
Threat actors typically target users searching for cracked software via Google-hosted services (Colab, Drive, Looker Studio, etc.), which they use to host initial landing pages that funnel victims to the actual malicious payload.
The infrastructure is sophisticated, often filtering users by operating system: Windows users receive a .tar archive that, upon extraction, delivers a password-protected ZIP containing an infostealer executable (notably ACR, which also acts as a loader for follow-on malware such as cryptocurrency clippers).
MacOS users, meanwhile, are redirected to parallel fake security check pages where they download payloads such as the Odyssey stealer.
This infection chain demonstrates significant adaptation. The malicious pages are rarely blocked because they are hosted on trusted domains (e.g., Google services), and what appears to be a legitimate browser command is actually a hidden Base64-Encoded shell script.
Notably, distribution of ACR stealer logs surged nearly 700% within a month, with over 133,000 new log sets uploaded to the Russian Market in one recent campaign, indicating both high infection rates and valuable harvested data.
Current Trends and Recommended Defense
With advanced persistent threat (APT) actors and financially motivated cybercriminals alike adopting ClickFix, organizations and individuals must be vigilant.
Since attacks often evade gateway and browser security tools, detection largely relies on robust EDR solutions that can identify fileless and memory-based threats. Users should be cautioned never to execute unsolicited scripts or commands from unknown web pages, comments, or messages.
Security teams are urged to monitor for unusual command-line activity, Base64-encoded payloads, and suspicious network traffic linked to file-sharing services and remote servers.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates