The internet weathered new and alarming extremes in the second quarter of 2025 as Cloudflare’s latest DDoS Threat Report revealed the largest Distributed Denial of Service (DDoS) attack ever recorded, peaking at an unprecedented 7.3 terabits per second (Tbps) and surging to a staggering 4.8 billion packets per second (Bpps).
The report, which draws on a comprehensive, global dataset from Cloudflare’s expansive network, underscores a rapidly escalating threat landscape one not just defined by sheer scale, but by the evolving sophistication and persistence of threat actors targeting critical sectors worldwide.
Escalating Global DDoS Threat
June 2025 was particularly volatile, accounting for nearly 38% of all DDoS activity in the quarter.
Among those targeted was an Eastern European news outlet, which came under sustained DDoS attack following its coverage of an LGBTQ Pride parade illustrating the frequent use of DDoS as a blunt instrument of censorship and disruption.

While the overall number of attacks decreased compared to the extraordinary surge in the previous quarter driven then by a targeted campaign against Cloudflare and internet backbone providers the attack volume in Q2 2025 still exceeded the comparable period last year by an astonishing 44%.
Hyper-volumetric DDoS attacks, defined as those that exceed 1 Tbps or 1 billion packets per second, now occur with alarming frequency.
According to the Report, Cloudflare automatically mitigated more than 6,500 such incidents this quarter, averaging roughly 71 attacks per day.
The leap in attack magnitude is matched by a diversification of techniques, with year-over-year HTTP DDoS activity (targeting application-layer protocols) jumping 129%.
Financial Sectors in the Crosshairs
Meanwhile, Layer 3/4 attacks which typically bombard networks with floods of SYN, UDP, or DNS requests dropped sharply but still maintain a substantial presence, with DNS flood attacks alone comprising nearly a third of all high-volume assaults.
Industries and geographies saw significant shifts in targeting patterns. Telecommunications, Service Providers, and Carriers again suffered the heaviest barrage, followed closely by internet infrastructure, IT services, and online gaming platforms.
Notably, the agriculture sector surged into the top ten most attacked industries with a 38-place leap, reflecting broadening motivations among attackers.
Regional analysis showed China reclaiming the unwanted top position as the most targeted customer location, with Brazil, Germany, India, and South Korea also experiencing elevated threat levels.
However, these rankings reflect attack volumes against customers’ billed entities, not necessarily geopolitical targeting.
Attribution of DDoS origin remains challenging 71% of surveyed victims could not identify their attackers.
Where attribution was claimed, most pointed to business competitors, particularly in gaming and cryptocurrency, while a significant minority blamed state-sponsored actors, extortionists, or even self-inflicted disruption (“self-DDoS”).
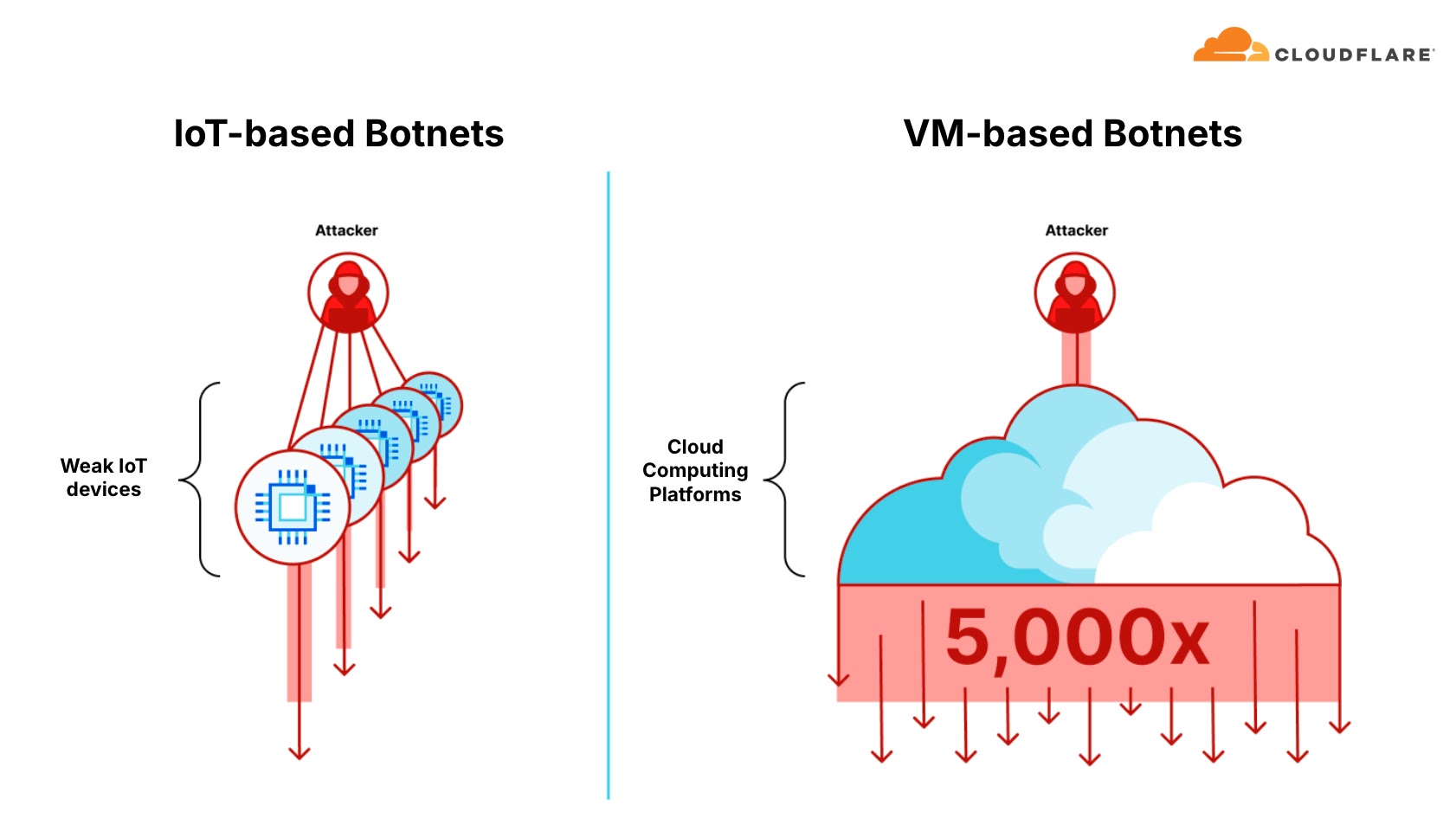
Technical telemetry paints a complex picture of sources: Indonesia leads the list of botnet node origins, narrowly ahead of Singapore and Hong Kong, with the VM-hosting ASN market now overwhelmingly favored for botnet command and control yielding attack traffic that is up to 5,000 times as potent as legacy IoT-based botnets.
While the majority of attacks were short-lived and “small” by internet backbone standards less than 500 Mbps for most Layer 3/4 events even these pose existential threats to typical enterprise servers, which can be quickly overwhelmed in the absence of cloud-based mitigation.
Hyper-volumetric events, though rarer, are growing both in frequency and ferocity; six out of every hundred HTTP assaults now exceed one million requests per second.
Attackers employ brief, high-intensity bursts, some as short as 45 seconds, to evade detection and maximize disruption before countermeasures engage.
Emerging threats show a return to and the reinvention of old vectors. The past quarter witnessed dramatic spikes in abuse of obscure or legacy protocols such as Teeworlds, RIPv1, and VxWorks, exploited to circumvent standard mitigations.
These findings highlight the arms race between attackers’ innovation and defenders’ automation: 71% of HTTP DDoS attacks leveraged known botnets, and real-time threat intelligence is essential to neutralize them network-wide the moment they appear.
Cloudflare’s continued expansion of automated defense systems, coupled with community botnet intelligence sharing, remains critical as DDoS tactics grow ever more momentary, multi-vector, and global.
The imperative for always-on, adaptive protection across all industries and regions is clearer than ever, as the internet’s most relentless adversaries show no sign of relenting.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates