A financially motivated threat actor cluster tracked as CL‑CRI‑1032, and assessed to overlap with Atlas Lion (STORM‑0539), has conducted a large‑scale cybercrime spree known as the Jingle Thief campaign.
Originating from Morocco and active since 2021, the group strategically launches attacks around festive periods, exploiting increased holiday traffic and reduced staffing to execute massive gift card fraud against global retail and consumer service enterprises.
Cloud Intrusion Without Malware
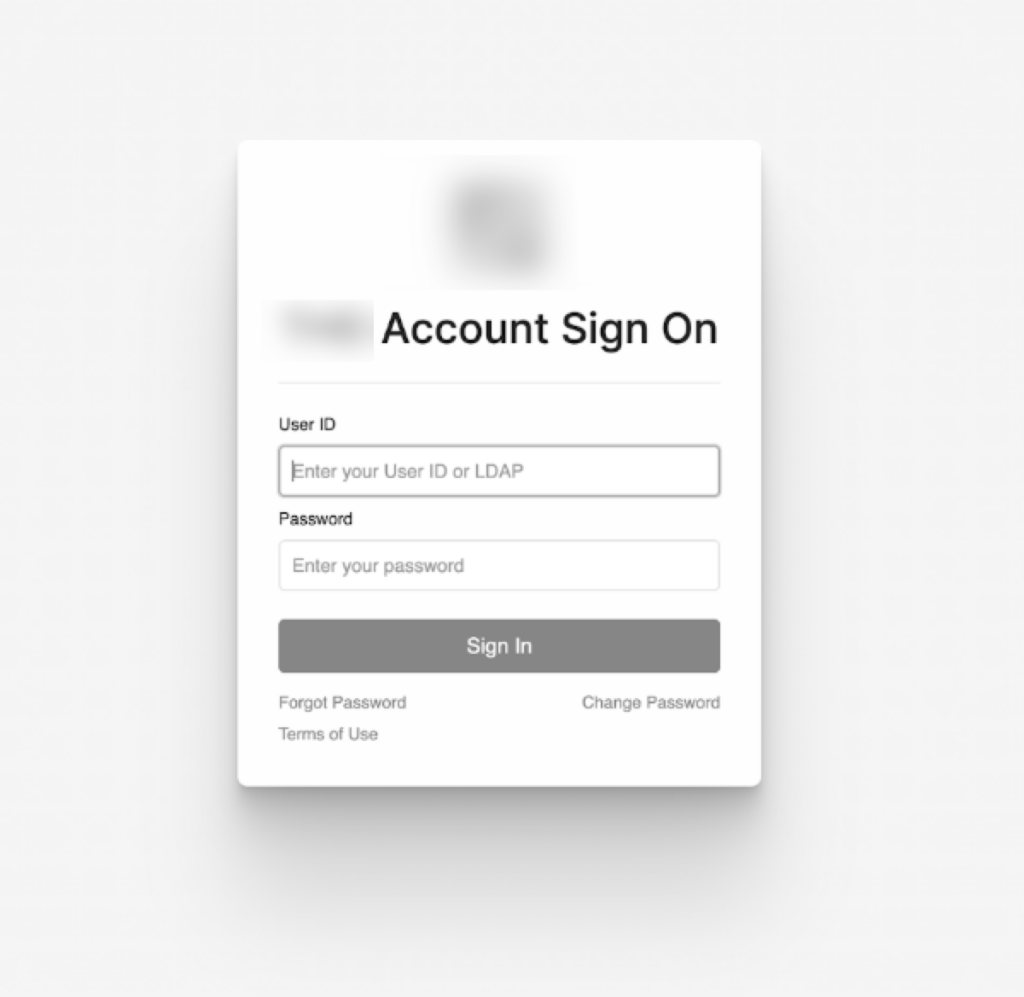
Unlike traditional malware campaigns, Jingle Thief relies almost entirely on phishing and smishing to harvest Microsoft 365 credentials.
Attackers send emails and SMS lures that impersonate legitimate corporate notifications, often using self-hosted PHP mailers on compromised WordPress servers, to redirect victims to counterfeit Microsoft 365 login pages.
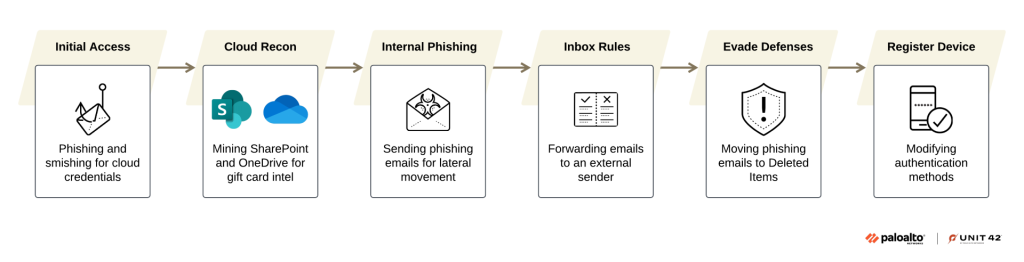
Once credentials are obtained, threat actors conduct cloud‑only operations, leveraging legitimate Microsoft services like SharePoint, OneDrive, Exchange, and Entra ID.
In incidents observed by Unit 42, Jingle Thief maintained persistent access for nearly 10 months, compromising over 60 user accounts within a single enterprise.
After initial infiltration, the attackers performed intensive reconnaissance, mining internal documentation for gift‑card issuance workflows and financial processes stored in SharePoint.
They then launched internal phishing using compromised accounts to move laterally, sending realistic ServiceNow‑style notifications to expand their foothold.
Identity Abuse and Rogue Device Persistence
The campaign’s persistence mechanisms stand out for their abuse of Entra ID device registration and user self‑service features. Attackers silently enroll rogue devices, register fraudulent authenticator apps, and reset passwords through legitimate flows.
These tactics grant MFA‑resistant access, even after credentials are revoked. Email rules are created for passive monitoring of communications tied to financial approvals, while inbox folders are manipulated moving sent and received phishing messages to Deleted Items to delay detection.
Telemetry revealed that most malicious logins originated from Moroccan IP ranges associated with MT‑MPLS, ASMedi, and MAROCCONNECT providers, occasionally obscured through Mysterium VPN.
The infrastructure shows recurring patterns in domain naming and URL formatting, confirming regional attribution.
The motive remains clear: monetize stolen credentials by issuing unauthorized gift cards, then resell them at discounted rates on gray markets or use them for low‑risk money laundering.
Unit 42 emphasizes that the Jingle Thief campaign underscores a critical shift in cybercrime: identity misuse replacing endpoint exploits.
Retailers and service providers are urged to strengthen identity controls, enforce conditional access, and deploy solutions like Cortex UEBA, ITDR, and Advanced Email Security to detect anomalous behaviors across cloud environments before fraud scales during the holiday season.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates