The Trellix Advanced Research Center has uncovered a sophisticated North Korean espionage operation that exploited GitHub’s legitimate developer platform as a covert command-and-control channel to target diplomatic missions worldwide.
Between March and July 2025, DPRK-linked Kimsuky hackers executed at least 19 spear-phishing attacks against embassies in South Korea, successfully deploying XenoRAT remote access trojans to steal sensitive diplomatic intelligence.
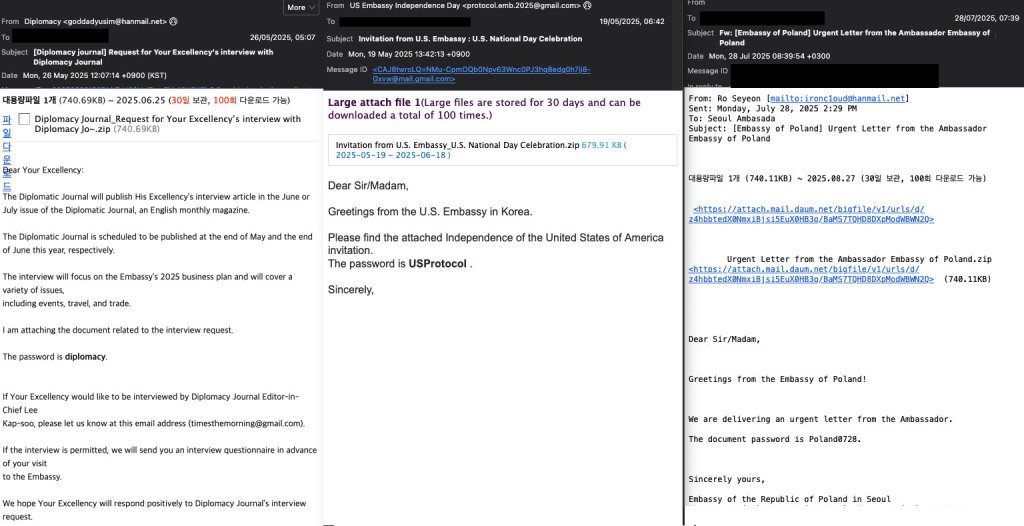
Sophisticated Social Engineering Campaign Targets Diplomatic Personnel
The campaign employed highly credible social engineering tactics, with attackers impersonating trusted diplomatic contacts through carefully crafted emails containing meeting invitations, official letters, and event announcements.
One notable example involved spoofing a U.S. Embassy protocol officer inviting recipients to an Independence Day celebration, while another impersonated an EU delegation First Secretary offering “political counselors meeting minutes”.
The attack chain began with password-protected ZIP archives delivered through legitimate cloud services like Dropbox and Daum, containing malicious Windows shortcut files disguised as PDF documents.
When victims opened these files, embedded PowerShell scripts would execute, downloading additional payloads from attacker-controlled GitHub repositories using accounts “blairity” and “landjhon”.
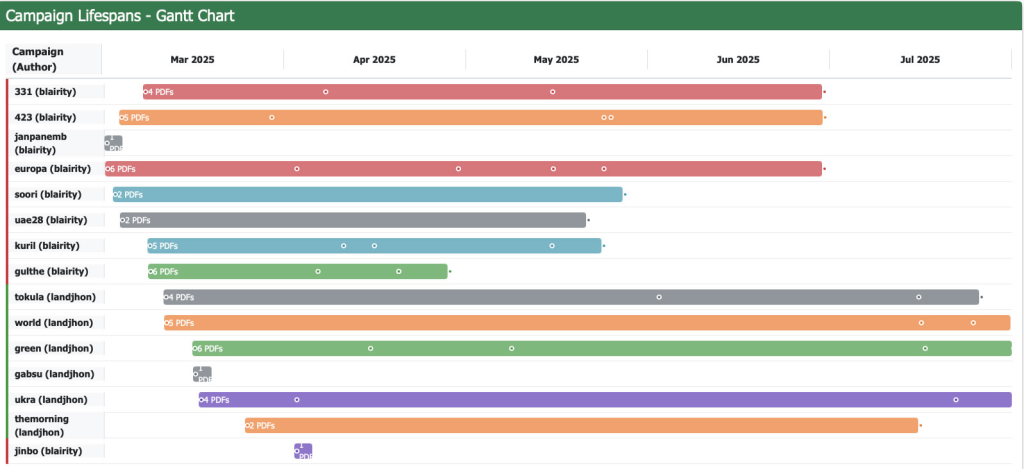
GitHub Repositories Used as Command-and-Control Infrastructure
The hackers demonstrated remarkable innovation by abusing GitHub’s API for both data exfiltration and payload distribution.
Stolen reconnaissance data, including system information and network details, was automatically uploaded to private repositories using hardcoded personal access tokens.
The malware formatted exfiltrated data with timestamps and IP addresses in specific filename patterns before base64-encoding and uploading via HTTPS requests that blended seamlessly with legitimate GitHub traffic.
For command-and-control operations, attackers maintained text files in their repositories that served as payload indicators, directing infected machines to download compressed XenoRAT variants from Dropbox.
This technique enabled rapid infrastructure rotation, with payload URLs updated multiple times within hours to deploy malware and remove traces.
Advanced Malware Deployment and Attribution
The final payload was a sophisticated XenoRAT variant obfuscated using Confuser Core 1.6.0, providing complete system control through keystroke logging, screenshot capture, webcam access, and remote shell capabilities.
Technical analysis revealed that the malware employed a unique GZIP header manipulation technique consistently observed across multiple North Korean campaigns.
Attribution to Kimsuky (APT43) was confirmed through infrastructure overlap with known DPRK espionage operations, including IP addresses 158.247.230.196 and 141.164.49.250 linked to previous campaigns.
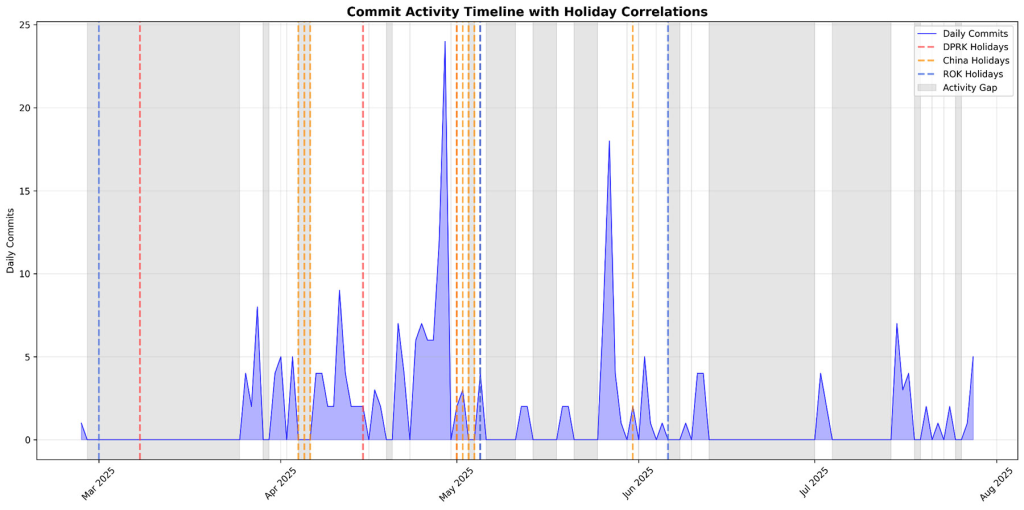
However, timezone analysis revealed operators primarily worked from UTC+8 (China timezone), with activity gaps perfectly aligning with Chinese national holidays, suggesting North Korean operatives may be operating from Chinese territory.
The campaign remains active as of July 28, 2025, highlighting the ongoing threat to diplomatic communications worldwide.
Indicators of Compromise (IoCs)
Name: Diplomacy Journal_Request for Your Excellency’s interview with Diplomacy Jo~.zip
MD5: 5f704db7552a0b6b535b9c7c5f240664
SHA256: 1e10203174fb1fcfb47bb00cac2fe6ffe660660839b7a2f53d8c0892845b0029
Name: Invitation from U.S. Embassy_U.S. National Day Celebration.zip
MD5: 8b605de9d28c8c6477a996d4e5873e4e
SHA256: cf2cba1859b2df4e927b8d52c630ce7ab6700babf9c7b4030f8243981b1a04fa
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates