A sophisticated threat campaign has emerged, marked by the pairing of LeakyInjector and LeakyStealer, two newly discovered malware strains targeting users to siphon cryptocurrency assets and browser history.
Hybrid Analysis’s deep dive exposes these threats’ technical prowess and operational coordination, signaling a dangerous escalation in cybercriminal ambition throughout October 2025.
Two-Stage Attack: Precision and Stealth
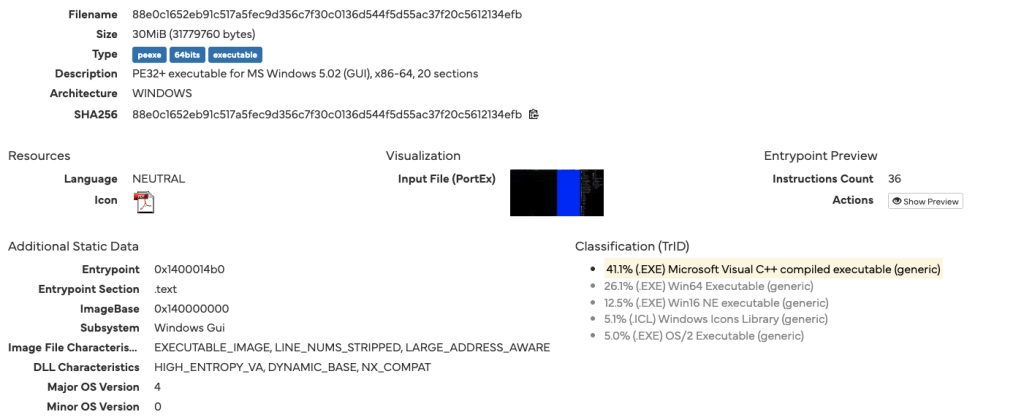
The infection cycle begins with LeakyInjector, a 64-bit Windows executable ingeniously signed with a valid Extended Validation (EV) digital certificate.
This unusual legitimacy enables it to bypass security scrutiny, while its large file size, padded with null bytes, further hinders detection.
Upon execution, LeakyInjector searches for the explorer.exe process and deploys low-level Windows APIs to inject an encrypted payload, LeakyStealer, into memory.
This second-stage loader is protected by ChaCha20 encryption, with decryption parameters embedded within the binary.
Once resident, LeakyStealer takes root by establishing persistence through a registry entry called “EdgeUpdateCore” and masquerading as MicrosoftEdgeUpdateCore.exe within the user’s AppData directory.
It gathers reconnaissance data, computing a unique Bot ID, collecting hostnames, usernames, and domain data before connecting to a command-and-control (C2) server at everstead[.]group via encrypted HTTP POST requests, impersonating browser network traffic.
LeakyStealer’s standout feature is its polymorphic engine, capable of altering specific memory bytes during runtime using randomized assembly instructions.
While this does not directly modify operational logic, it complicates static detection and analysis.
The malware performs reconnaissance for dozens of popular crypto wallets, including Electrum, Exodus, Atomic, Ledger Live, Sparrow, Guarda, and BitPay.
It also searches for browser wallet extensions like MetaMask, Phantom, Coinbase, and Trust Wallet.
In parallel, LeakyStealer scans for, copies, and exfiltrates browser history files from Google Chrome, Edge, Brave, Opera, and Vivaldi.
These files are read in-memory and quickly deleted, minimizing forensic traces.
All data is transmitted to the C2 using carefully forged network packets bearing a Bot ID in custom headers.
The malware includes two powerful backdoor commands: downloading and executing files from the C2 and executing arbitrary Windows commands, with the output stealthily relayed back to the threat actor.
Digital forensics ties multiple samples to the same compromised certificate infrastructure, all masquerading as legitimate Windows components across October 2025.
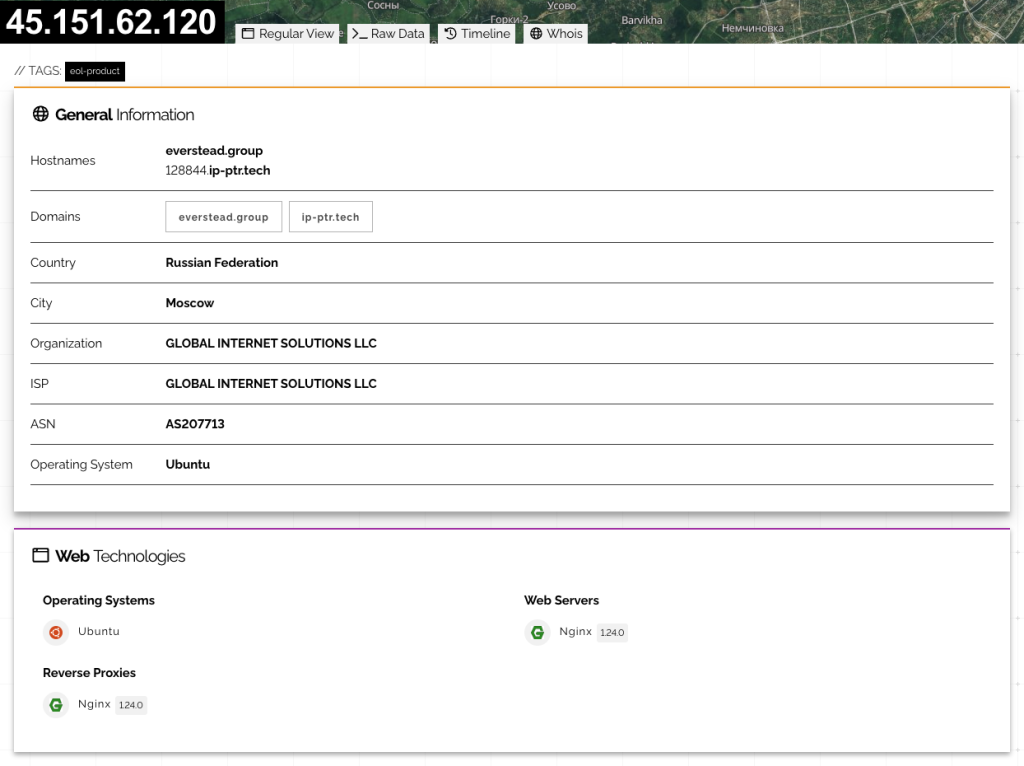
Shodan data links the campaign to IP 45.151.62.120, with domains everstead[.]group and ip-ptr[.]tech and the payload distributed via MSI installers from paycnex[.]com.
Indicators of Compromise
- SHA256 Samples:
9b8bd9550e8fdb0ca1482f801121113b364e590349922a3f7936b2a7b6741e82
88e0c1652eb91c517a5fec9d356c7f30c0136d544f5d55ac37f20c5612134efb - Files Created:
%AppData%\MicrosoftEdgeUpdateCore.exe,C:\Users\<User>\AppData\Local\Temp\history_%d.db - Registry:
EdgeUpdateCore - C2:
everstead[.]group
Hybrid Analysis underscores the campaign’s sophistication, particularly the abuse of code signing and stealthy exfiltration mechanisms, warranting immediate attention from incident response teams and defenders.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today