A recently disclosed vulnerability in the Linux Kernel’s KSMBD module enables unauthenticated remote code execution (RCE) on systems running Linux 6.1.45 with KSMBD enabled.
KSMBD, the kernel-space SMB3 server for network file sharing, was thought to offer performance advantages over user-space alternatives.
However, security researchers have demonstrated a stable, 0-click exploit against two known CVEs patched by the Zero Day Initiative in late 2023 and early 2024, achieving successful RCE in over 95 percent of test cases.
Exploit Chain and Heap Abuse
The exploit begins with CVE-2023-52440, an unauthenticated heap overflow triggered during NTLM authentication.
An attacker crafts an oversized session key blob in an SMB2_SESSION_SETUP message, forcing a controlled overflow in a kmalloc-512 slab.
This overflow yields a “writeheap” primitive that corrupts adjacent kernel memory without any prior authentication or user interaction.
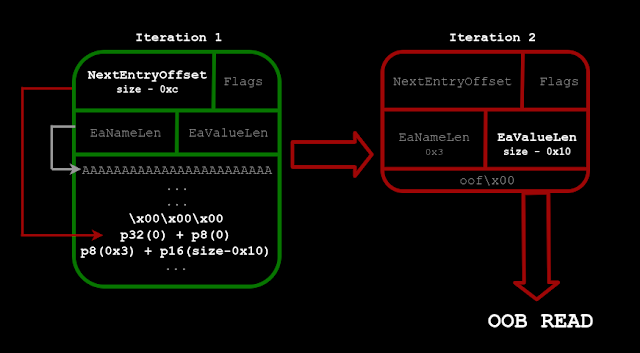
Next, CVE-2023-4130, an authenticated bug in the Extended Attributes (EA) parser, provides an out-of-bounds read primitive.
By sending a malicious EA buffer, the attacker leaks arbitrary heap contents through xattr metadata, establishing a “writeleak” primitive that exposes kernel pointers.
Researchers then abuse heap layout to bypass Kernel Address Space Layout Randomization (KASLR). By opening multiple SMB connections and sessions, they spray kernel objects and repeatedly trigger the overflow until a target connection’s memory is corrupted.
A guided spray-and-check loop reliably locates the overflow victim and leaked pointers from a kmalloc-1k slab holding KSMBD connection objects.
The leak reveals kernel pointers, allowing the attacker to calculate offsets and construct a kernel ROP chain that hijacks the session’s local_nls pointer.
With KASLR defeated, the attacker proceeds to manipulate function pointers within a kmalloc-1k chunk by leveraging an arbitrary free primitive that overlaps a connection object.
A carefully crafted SMB request allocates a large chunk containing the ROP chain, which pivots the kernel stack into controlled memory.
The gem of the exploit is invoking call_usermodehelper to spawn a user-mode reverse shell, all while preserving kernel stability.
A sleep gadget inserted in the ROP chain holds the kernel thread alive, preventing systemic crashes.
Although KSMBD is commonly disabled in production environments, any system running an unpatched 6.1.x kernel with KSMBD exposed to untrusted networks remains at risk.
Administrators are urged to upgrade to Linux Kernel 6.1.46 or later, where both CVEs have been backported and patched.
Enabling standard kernel hardening options—such as SMEP, SMAP, KPTI, and random slab freelist—reduces exploit reliability but does not fully eliminate the threat.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates