A recent Phrack Magazine publication has revealed a large-scale data dump tied to a suspected North Korean-aligned threat group, exposing sophisticated Linux malware and rootkit modules.
The disclosure, believed to originate from a compromise of attacker infrastructure, sheds light on advanced operational tactics used against South Korean and Taiwanese government and private sector organizations.
Rootkit Capabilities and Stealth Features
The centerpiece of the leak is a Loadable Kernel Module (LKM) rootkit designed to evade traditional detection and provide persistent, covert access to Linux hosts. Built on the open-source khook library, the malware hooks Linux system calls to conceal its presence and activities. Its features include:
- Module hiding: Conceals itself from
lsmodand tamper-proof kernel listings. - Process/network evasion: Masks backdoor processes and hides socket activity, preventing discovery with tools like
psorss. - Persistence: Deploys startup scripts under
/etc/init.d/and runlevels (/etc/rc*.d) to load automatically on reboot. - Hidden binaries: Stores malicious components in non-standard paths like
/usr/lib64/tracker-fsand/usr/include/tracker-fs/tracker-efs. - Cloaked I/O: Establishes a covert communication channel through
/proc/acpi/pcicard.
The backdoor activates only after receiving a magic packet combined with a password, creating an encrypted connection that can run over any port, including those already used by legitimate services.
Capabilities extend to launching interactive shells, uploading and downloading files, opening SOCKS5 proxies, and lateral host chaining for multi-hop intrusions.
The rootkit also employs anti-forensic techniques. Spawned shells disable history logging by redirecting variables to /dev/null, making command activity difficult to reconstruct.
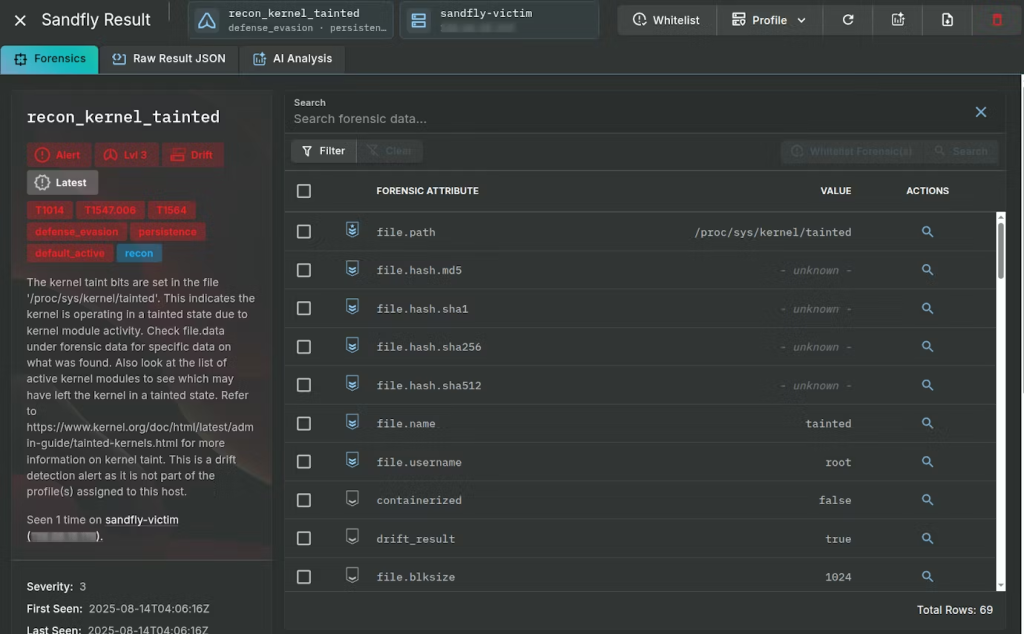
Detection and Incident Response
Security researchers warn that traditional defenses are insufficient. While kernel taint flags (dmesg | grep taint) may reveal unsigned modules like the malicious vmwfxsStealth techniques often remove traces after loading.
Detection methods include checking for cloaked files with stat or file commands, reviewing unexpected persistence scripts, and analyzing systemd services for anomalies (systemctl status tracker-fs.service).
Tools such as Sandfly Security’s decloaking utilities have been confirmed effective in identifying cloaked processes and hidden kernel modules.
However, experts stress that if a host is compromised at the kernel level, organizations should immediately isolate and rebuild systems rather than attempting direct clean-up, as trust in the integrity of the machine can no longer be guaranteed.
Conclusion
The emergence of this rootkit underscores the growing sophistication of North Korean state-linked operations. By weaponizing kernel-level stealth, the attackers can infiltrate networks while remaining nearly invisible to conventional monitoring.
Security teams are advised to enhance Linux incident response workflows with automation and anomaly detection, ensuring persistence and cloaked threats can be exposed before attackers achieve long-term footholds.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates