Threat intelligence researchers at Outpost24 have been closely tracking a corporate database seller operating under the alias “Lionishackers.”
This threat actor, whose activity first surged in September 2024, has become a significant player in the dark web marketplace, specializing in the exfiltration and sale of corporate databases.
The group’s targeting appears opportunistic, but data suggests a particular focus on organizations within Asian countries, especially industries such as gambling, government, pharmaceuticals, telecommunications, education, and retail.
Technical Operations and Methods
Lionishackers is largely financially motivated, yet their activities suggest occasional ideological undertones.
While their primary operation revolves around obtaining and selling stolen corporate databases, the actor has been observed collaborating with the “Hunt3r Kill3rs” group, signaling involvement in politically-charged Distributed Denial-of-Service (DDoS) attacks, including those targeting entities in Ukraine and Israel.
Operationally, Lionishackers favors SQL injection, an attack vector they have openly discussed on Telegram channels, often referencing automated tools such as SQLMap.

Their breaches have included not only classic corporate data sources but also credentials obtained from social media platforms and email services, hinting at the use of credential stuffing or simple password reuse for initial access.
Sales and communications are coordinated almost exclusively through Telegram, with advertisements for fresh data leaks disseminated across multiple underground forums and Telegram channels.
Notably, Lionishackers does not operate a proprietary Data Leak Site (DLS) but instead relies on the rapid, ephemeral marketing opportunities provided by these platforms.
The actors are known for adopting different aliases for each forum account, possibly to evade attribution and forum bans, but often share consistent Telegram contact details for operational continuity.
Brand Expansion
Beyond database sales, Lionishackers has diversified their offerings with penetration testing services, commercialization of the “Ghost” botnet (capable of supporting both Layer 4 and Layer 7 attacks), and the short-lived launch of “Stressed Forums,” an underground forum that emerged during a period of turbulence caused by law enforcement takedowns of other popular cybercrime forums.
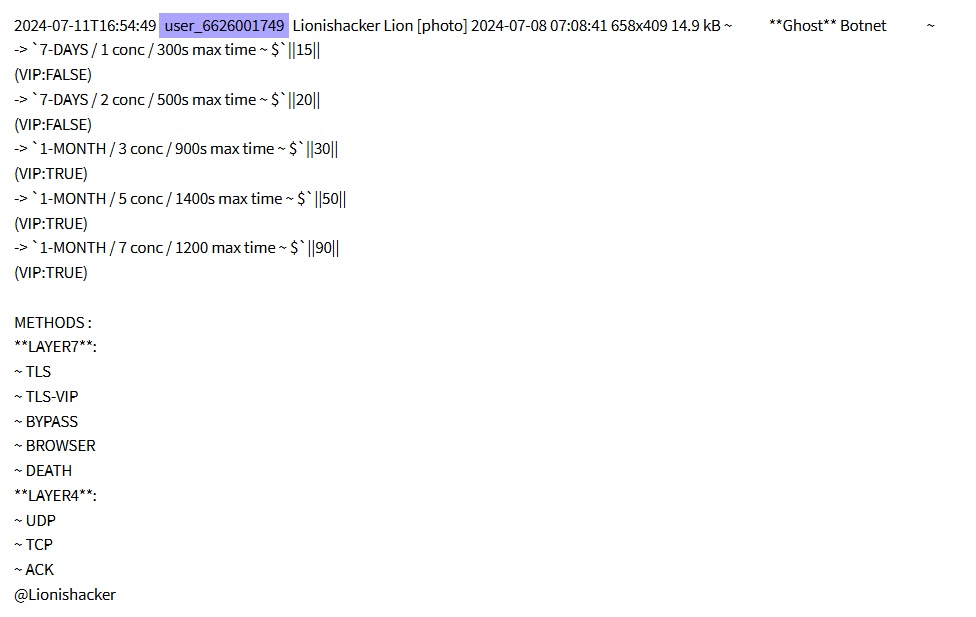
However, these secondary projects have not garnered significant long-term traction. The risk associated with this group and others with a similar modus operandi remains severe.
Unauthorized database leaks provide malicious actors with valuable data for credential reuse, corporate espionage, fraud, and sophisticated social engineering attacks.
The sale or free distribution of these databases in closed communities amplifies the threats faced by victim organizations, as news of breaches often reaches a wider criminal audience.
According to the report, Lionishackers’ tendency to publicize successful compromises with accompanying evidence adds to their credibility in the cybercrime underground, despite occasional accusations of scamming other forum users.
With regulations imposing heavy fines for data breaches and media attention popularizing data leak marketplaces, corporate database exfiltration remains a highly profitable avenue for both seasoned and emerging cybercriminals.
Indicators of Compromise
| Forum | Username | Registration/Ban Date |
|---|---|---|
| crackingx | Hacker82828 | September 3, 2024 |
| crackingx | Sussyba17 | September 23, 2024 |
| Crackia | Sectornull101 | September 19, 2024 |
| Crackia | Matadempo11 | September 24, 2024 |
| Leakzone | Fen888 | April 2025 |
| Sinister | datwkuvnj | June 21, 2025 |
| DarkForums | Datcomon23 | September 22, 2024 |
| DarkForums | Sudsyba17 | September 23, 2024 |
| DarkForums | Datajsbdj | October 31, 2024 |
| DarkForums | Datahellosui | November 18, 2024 |
| DarkForums | PremiumDataOnly | May 7, 2025 (Banned) |
| DarkForums | Captainfen | May 27, 2025 (Banned) |
| DarkForums | OfficialSalesMan | June 2025 (Banned) |
| DarkForums | foreman | June 21, 2025 |
| DarkForums | Datasellonly | July 5, 2025 |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates