COLDRIVER, a Russian state-sponsored threat group also known as UNC4057, Star Blizzard, and Callisto, has rapidly retooled its malware arsenal following the May 2025 public disclosure of its LOSTKEYS malware.
Google’s Threat Intelligence Group (GTIG) reports that the advanced persistent threat actor operationalized new malware families just five days after the disclosure, demonstrating an aggressive shift in tactics targeting high-profile individuals in NGOs, policy advisors, and political dissidents.
The threat group abandoned LOSTKEYS entirely after publication, with GTIG observing zero instances of the malware since disclosure.
Instead, COLDRIVER deployed a collection of related malware families connected through a sophisticated delivery chain, showing multiple iterations that indicate a rapidly increased development and operations tempo.
New Malware Arsenal and Infection Chain
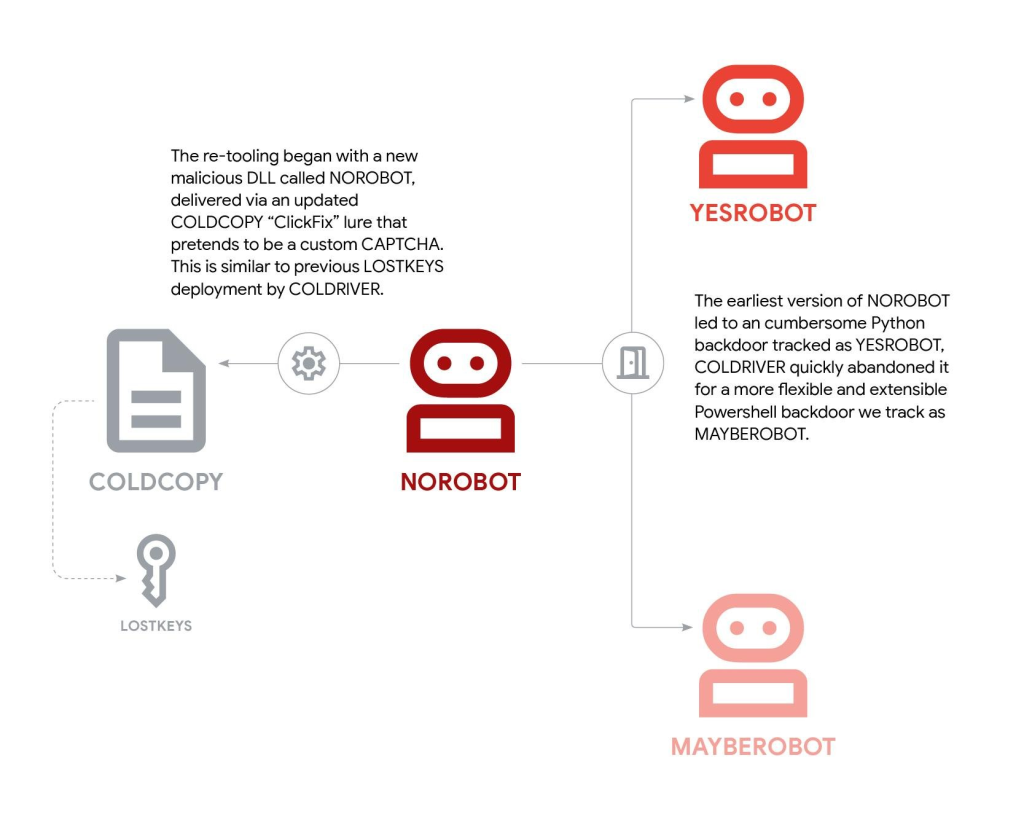
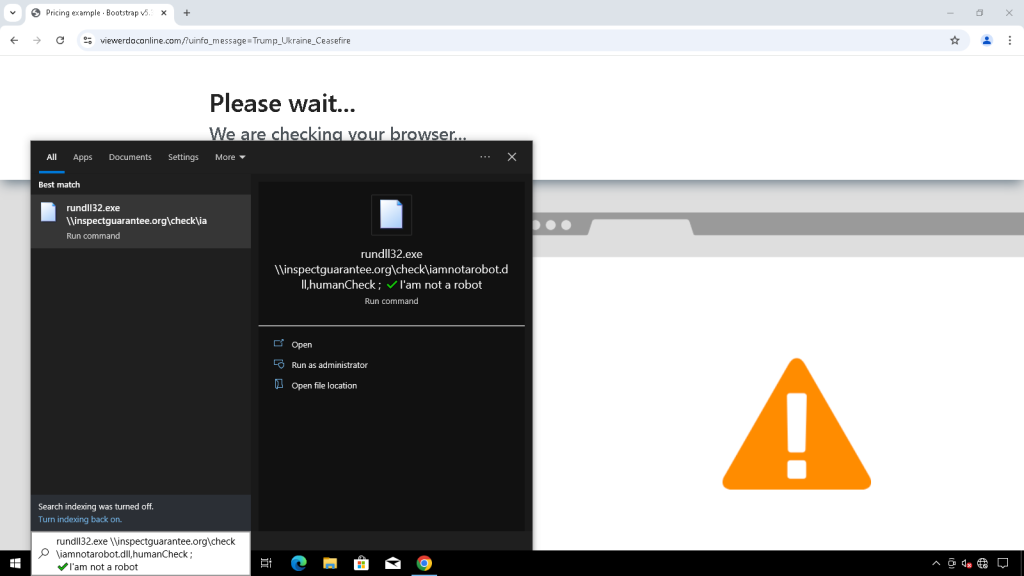
The retooling centers on three primary malware components delivered via an updated COLDCOPY “ClickFix” lure that masquerades as a custom CAPTCHA verification system.
The initial infection vector tricks users into downloading and executing a malicious DLL using rundll32, representing a significant departure from the older multi-stage PowerShell deployment method used with LOSTKEYS.
NOROBOT, also disclosed as BAITSWITCH by Zscaler researchers, serves as the primary DLL downloader that retrieves the next stage from hardcoded command and control addresses.
The malware underwent regular development from May through September 2025, with various versions showing different levels of complexity.
Early versions implemented split cryptography keys across multiple components to hinder analysis, though this also introduced noisy artifacts like a full Python 3.8 installation that raised detection risks.
The infection chain initially deployed YESROBOT, a minimal Python backdoor that uses HTTPS to retrieve AES-encrypted commands from hardcoded C2 infrastructure. System information and usernames are encoded in User-Agent headers during communications.
However, YESROBOT’s requirement for valid Python commands made typical backdoor functionality cumbersome to implement. GTIG observed only two YESROBOT instances over two weeks in late May before COLDRIVER abandoned it, assessing it was a hastily deployed stopgap mechanism.
By early June 2025, COLDRIVER replaced YESROBOT with MAYBEROBOT, also known as SIMPLEFIX. This heavily obfuscated PowerShell backdoor provides greater flexibility through a custom protocol supporting three primary commands: download and execute from URLs, execute commands via cmd.exe, and execute PowerShell blocks.
MAYBEROBOT eliminates the Python installation requirement while maintaining extensibility for complex operations.
Throughout June to September 2025, GTIG observed COLDRIVER implementing basic evasion techniques including rotating infrastructure, changing file naming conventions and DLL export names, and reintroducing cryptographic complexity to make infection chain reconstruction more difficult for network defenders.
The consistent development of NOROBOT variants contrasts with the unchanged MAYBEROBOT backdoor, suggesting COLDRIVER has high confidence in the final payload’s detection evasion capabilities while focusing development efforts on delivery mechanism protection.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates