A sophisticated information-stealing malware known as Lumma Infostealer is resurging as a major cyber threat. It targets high-value credentials and sensitive assets stored on Windows systems.
The malware, distributed through a Malware-as-a-Service (MaaS) model, enables even low-skilled attackers to execute complex data theft campaigns by simply subscribing to a service.
Lumma Infostealer is being deployed in phishing campaigns disguised as cracked or pirated software, often hosted on legitimate platforms such as MEGA Cloud to evade detection.
Once executed, the malware performs multi-stage decryption and process injection to activate its payload while concealing its actual behavior from traditional antivirus solutions.
Technical Breakdown of Lumma Operations
According to Genians Security Center (GSC) researchers, the latest Lumma samples use Nullsoft Scriptable Install System (NSIS) as a deceptive installer package.
When a victim runs the downloaded “setup.exe,” it extracts malicious payloads into the %Temp% directory and launches a fake “Contribute.docx” file through cmd.exe.
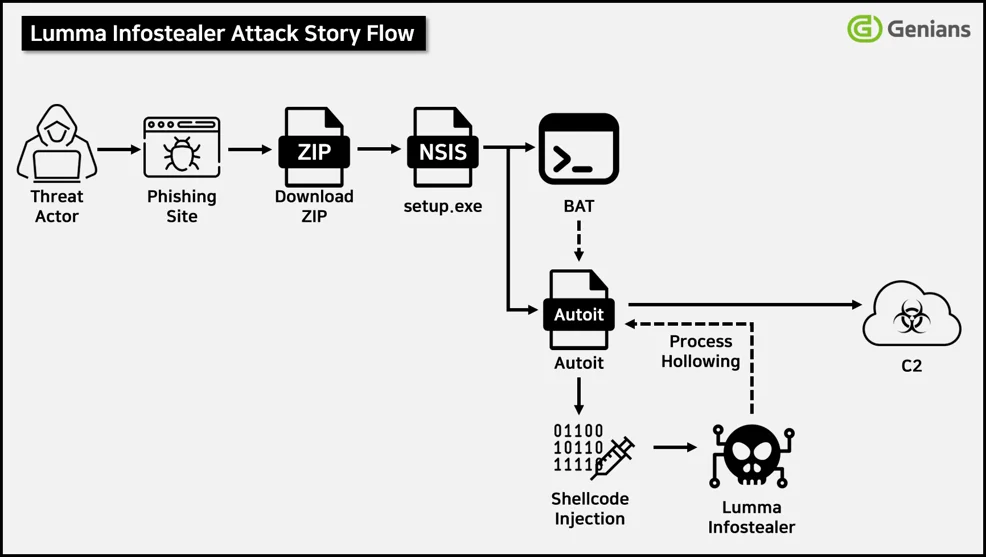
This document triggers a series of commands reconstructing a hidden AutoIt-based loader for deploying Lumma’s encrypted core.
The AutoIt script uses shellcode injection and process hollowing to embed the Lumma payload inside a benign process, masking its activity.
The injected process then decrypts command-and-control (C2) domains and initiates communication with remote attacker servers. rhussois[.]su, diadtuky[.]su, and todoexy[.]su.
Once connected, Lumma Infostealer systematically collects stored browser credentials, session cookies, Telegram data, remote access (VPN/RDP) configuration files, and cryptocurrency wallet information.
The stolen data is exfiltrated to C2 servers for further exploitation, where it may be reused for identity theft, corporate breaches, or credential resale on dark web forums.
The malware checks running processes to avoid early termination and deactivates its functions if security solutions such as Sophos, Norton, ESET, Bitdefender, or Avast are detected. Its modular structure and frequent updates make signature-based detection largely ineffective.
EDR-Based Detection and Response
Analysts emphasize that detection requires behavior-based Endpoint Detection and Response (EDR) systems, capable of tracking command chains, file drops, and process relations.
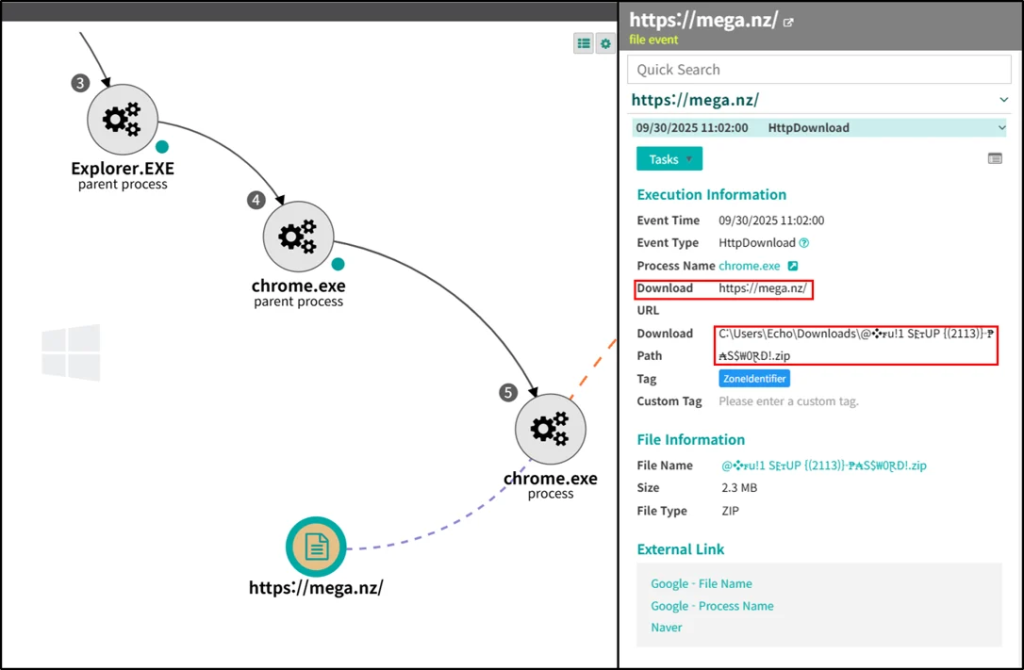
Genian EDR, for instance, visualizes Lumma’s attack storyline, providing visibility into shellcode injection, AutoIt script execution, and network communication events in real time.
To mitigate exposure, security professionals recommend avoiding credential storage in browsers, enforcing multi-factor authentication (MFA), and monitoring for suspicious child processes stemming from installer files.
As Lumma continues to evolve under the MaaS economy, the campaign underscores the growing industrialization of cybercrime and the urgent need for intelligent, correlational threat monitoring.
IoC (Indicator of Compromise)
- MD5
E6252824BE8FF46E9A56993EEECE0DE6
E1726693C85E59F14548658A0D82C7E8
19259D9575D229B0412077753C6EF9E7
2832B640E80731D229C8068A2F0BCC39
- Domain
diadtuky[.]su
rhussois[.]su
todoexy[.]su
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates