A newly uncovered infostealer, dubbed ModStealer, is rapidly emerging as a major cross-platform threat, leveraging deceptive recruitment tactics to compromise macOS, Windows, and Linux systems.
First spotted on VirusTotal in early August, ModStealer marks a concerning shift in macOS malware sophistication, as it abuses Apple’s built-in tools to achieve stealthy persistence and harvest high-value credentials, including cryptocurrency wallet data.
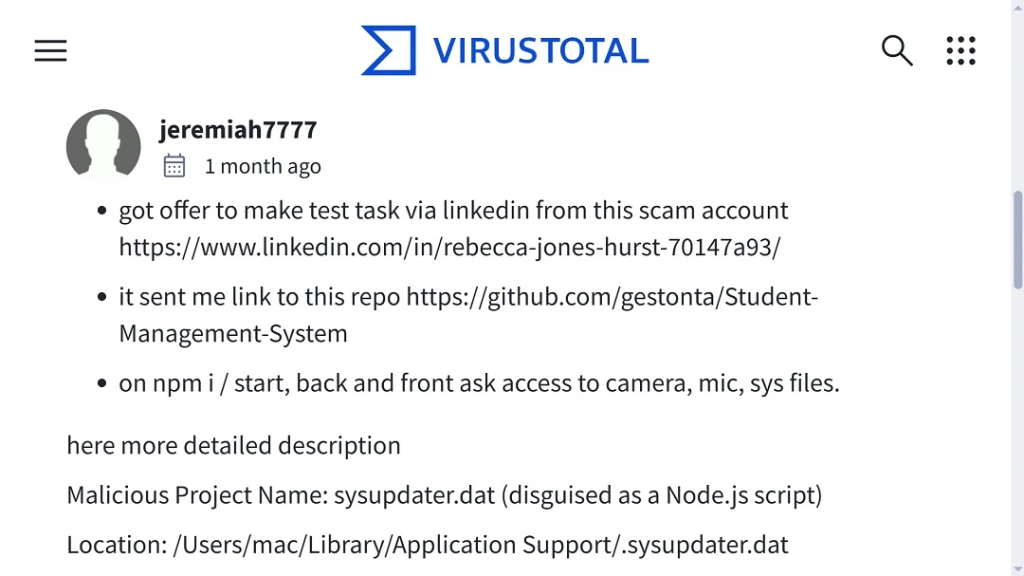
Deceptive Recruitment Campaign Lures Developers into Installing Trojans
ModStealer’s operators lure developers with fake job postings distributed via social media and email. Victims receive links to seemingly legitimate recruitment platforms where they download trojanized development tools or assessment packages.
This social engineering approach exploits developers’ trust in professional outreach, coaxing them into executing malicious payloads that appear benign at first glance.
Native macOS LaunchAgent Abuse Ensures Stealthy Persistence
On macOS, ModStealer installs itself as a LaunchAgent by invoking Apple’s native launchctl utility, embedding a plist that automatically relaunches the stealer on system startup.
Payload files are concealed under innocuous names sysupdater.dat within user Library directories, evading casual inspection and bypassing many antivirus scanners.
After installation, the initial download stub is deleted, leaving minimal forensic traces and making cleanup difficult without expert intervention.
Targeting Over 50 Crypto Wallet Extensions to Exfiltrate Seed Phrases
Upon activation, ModStealer enumerates installed browsers to identify more than fifty targeted extensions across Chrome and Safari, focusing on popular cryptocurrency wallets.
It extracts extension-specific data stores such as IndexedDB and LevelDB files alongside cookies and saved credentials.
The malware continuously monitors the clipboard for pasted seed phrases or private keys. It captures screenshots of active sessions, funneling all harvested information to a remote command-and-control server via encrypted HTTP requests.
ModStealer’s modular architecture enables attackers to deliver additional commands for lateral movement, allowing for the deployment of secondary payloads or the extraction of SSH keys and password manager vaults from developer environments.
This versatility makes it especially dangerous for those working with sensitive code repositories and cryptographic assets.
Security experts recommend that developers validate all recruitment communications and restrict job-related downloads to disposable, isolated virtual machines. Executing untrusted code on these VMs prevents wallet and SSH key exposure on primary workstations.
For cryptocurrency holders, migrating assets to hardware or cold wallets drastically reduces the online attack surface. Those requiring browser-based wallets should employ dedicated, locked-down profiles and enable multi-factor biometric authentication where possible.
As ModStealer demonstrates, macOS infostealers are evolving rapidly, combining sophisticated social engineering with native persistence techniques to evade detection.
Staying informed of threat actor tactics and enforcing strict operational hygiene remain essential defenses against these advanced data-stealing campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates