Security researchers have uncovered a sophisticated Magecart campaign that leverages heavily obfuscated JavaScript to steal payment card data from compromised e-commerce websites.
The malicious infrastructure, centered around the domain cc-analytics[.]com, has been actively harvesting sensitive customer information for at least one year.
The attack begins with threat actors injecting malicious script tags into vulnerable ecommerce platforms. These scripts reference external JavaScript files hosted on attacker-controlled domains, with the primary payload located at https://www.cc-analytics[.]com/app.js.
The malicious code employs advanced obfuscation techniques using hex encoding and string manipulation to evade detection by security tools and analysts.
Analysis of the deobfuscated JavaScript reveals a targeted data collection mechanism that monitors checkout forms and payment method selections. The script attaches event listeners to critical form elements, including checkout input fields and credit card payment sections.
When customers enter their payment information, the malware captures credit card numbers, billing addresses, and other sensitive data in real-time.
Infrastructure Analysis Reveals Broader Campaign
Threat hunting efforts based on the initial cc-analytics[.]com discovery have exposed a larger criminal infrastructure spanning multiple domains.
Researchers identified at least six related domains, following similar naming patterns, including jgetjs[.]com and getnjs[.]com, getvjs[.]com, getejs[.]com, and utilanalytics[.]com. These domains share common hosting infrastructure and serve nearly identical malicious JavaScript payloads.
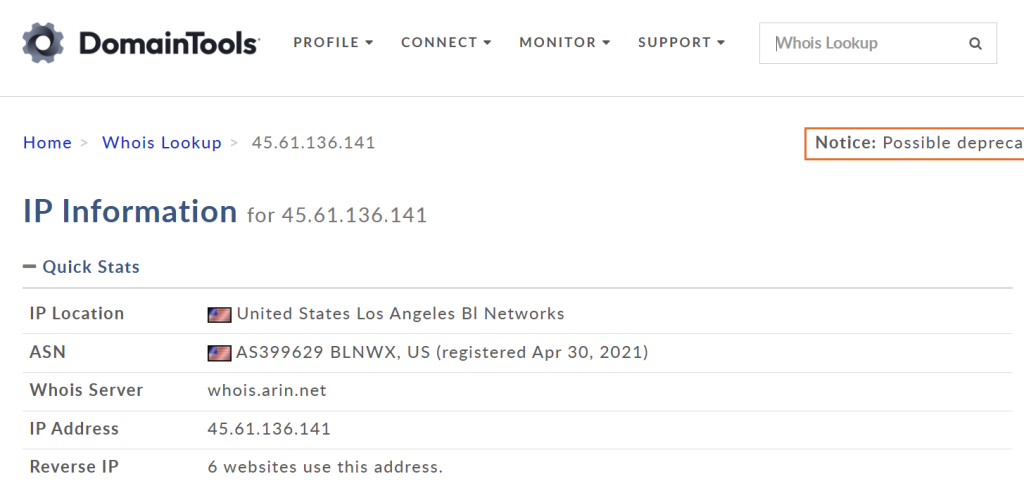
The entire operation traces back to IP address 45.61.136.141, which hosts the command-and-control infrastructure. Stolen payment data is exfiltrated to https://www.pstatics[.]com/i via HTTP POST requests containing the compromised customer information formatted as form data.

URLScan.io scans reveal widespread injection patterns across multiple compromised websites, with malicious scripts consistently inserted through two primary injection points on victim e-commerce platforms.
The threat actors demonstrate operational security awareness by recycling domain infrastructure and maintaining consistent naming conventions for their malicious domains.
The campaign’s longevity and sophisticated obfuscation techniques suggest an organized cybercriminal operation with significant technical capabilities.
The use of legitimate-sounding domain names like “cc-analytics” and “utilanalytics” helps the malicious infrastructure blend in with regular website analytics services, making detection more challenging for both automated security tools and manual analysis.
Security teams are advised to implement content security policies, monitor for unauthorized script injections, and regularly audit third-party JavaScript dependencies.
Website owners should validate all external script references and implement integrity checking for critical payment processing components to prevent unauthorized modifications that could enable payment skimming attacks.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates