A recent investigation has uncovered that cybercriminals are leveraging legitimate adtech platforms, sometimes even controlling them to distribute malware, phishing kits, and credential stealers at scale.
By exploiting the real-time bidding (RTB) model and convoluted corporate structures, threat actors achieve plausible deniability while maintaining resilient, high-volume malvertising campaigns.
A Threat Actor Masquerading as an Adtech Platform
One of the most ubiquitous operators, dubbed Vane Viper, has been observed in half of the monitored enterprise networks, generating over a trillion DNS queries in the past year.
Operating under the umbrella of AdTech Holding, a Cyprus-based company, Vane Viper’s flagship subsidiary is PropellerAds, which functions as both a supply-side platform (SSP) and demand-side platform (DSP).
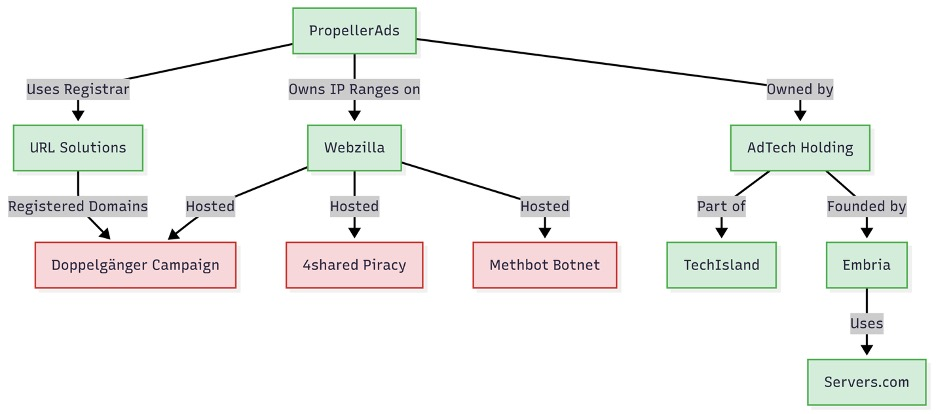
PropellerAds sources ad inventory from hundreds of thousands of compromised websites and routes clicks through its Traffic Distribution System (TDS) to malicious landing pages.
By cycling through thousands of domains monthly (peaking at 3,500 in October 2024), Vane Viper evades takedown efforts and sustains threat delivery through cloaking kits, geofencing, and dynamic response to ad blockers.
PropellerAds’ infrastructure overlaps with notorious registrars and hosts: its domains are bulk-registered via URL Solutions (a registrar ranked among the riskiest for phishing) and hosted on Webzilla and Servers.com network platforms, which have been previously linked to the Methbot click-fraud botnet, Doppelgänger disinformation campaigns, and piracy giants like 4shared.com.
IP allocations, such as 188.42.160.0/24, are directly assigned to PropellerAds, providing complete control over reverse DNS and routing for malicious campaigns.
Push Notifications, Script Chaining, and TDS Abuse
Vane Viper employs in-browser push notification abuse to achieve persistence on endpoints. Service worker scripts fetched from hardcoded domains execute remote code via eval(), presenting users with permission prompts that, once accepted, transform devices into perpetual malvertising vectors.
For users who deny permission, randomized subdomain redirects maintain the funnel, while browser history poisoning traps victims on malicious pages.

The TDS generates unique identifiers, OAID tokens, and global GIDs for fingerprinting, then consults a command-and-control server to determine the subsequent redirection based on geolocation, time-zone offsets, and feature toggles (e.g., smartOverlay, clickAnywhere, iOSClickFix).
This dynamic orchestration ensures only high-value targets receive harmful payloads, while researchers and automated scanners are diverted to benign dead ends.
Investigations also uncovered campaigns delivering Android trojans (e.g., Triada via .apk downloads), malicious browser extensions, fake shopping sites, survey scams, and simulated software downloads masquerading as legitimate installers.
A notable campaign utilized a bit.ly link to initiate a push subscription gate, then funneled users through PropellerAds-controlled domains, which were entirely owned and orchestrated by Vane Viper.
The permeation of threat actors into adtech supply chains illustrates a fundamental flaw in the digital advertising ecosystem: prioritizing scale and profitability over accountability.
As Vane Viper demonstrates, when adtech platforms become indistinguishable from malicious networks, user trust and security are irrevocably compromised.
Effective defense requires greater transparency from adtech vendors, stringent domain registration policies, and robust takedown procedures across registrars and hosting providers.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates