A wave of malicious Android applications impersonating legitimate Indian banking apps has prompted serious concern among cybersecurity experts, as these apps are being used to steal users’ login credentials, enable financial fraud, and enact extensive surveillance.
Security researchers at CYFIRMA have uncovered a complex and evasive banking malware campaign that utilizes advanced techniques such as silent installation, deep abuse of Android permissions, and remote command execution, all orchestrated through Firebase-based command-and-control (C2) infrastructure.
Advanced Infection Techniques
In their technical analysis, investigators found that the malware employs a modular structure, typically relying on a dropper APK to load a hidden, more potent payload (main banking malware).

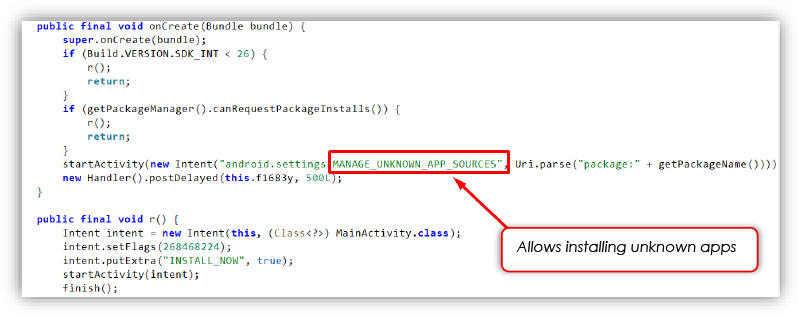
The dropper leverages several sensitive Android permissions most notably, REQUEST_INSTALL_PACKAGES, ACCESS_NETWORK_STATE, and QUERY_ALL_PACKAGES which allow the threat actors to silently install additional malicious APKs, monitor the device’s network state for optimal timing, and profile installed apps, especially security or banking applications.
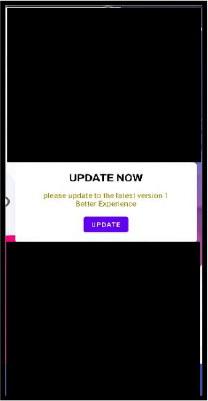
The silent installation mechanism ensures the payload is delivered and activated with minimal user awareness, often by prompting for “Install Unknown Apps” permissions and deceiving users via fake update popups or phishing overlays.
The main payload intensifies the threat by demanding permissions such as READ_SMS, SEND_SMS, and RECEIVE_SMS enabling interception and exfiltration of verification codes and one-time passwords (OTPs) straight from the user’s device.
Notably, READ_PHONE_STATE, READ_PHONE_NUMBERS, and RECEIVE_BOOT_COMPLETED permissions facilitate device fingerprinting, unauthorized call redirection, and persistence across device reboots. The malware also captures push notifications, further aiding in OTP theft and persistent presence.
Credential Harvesting Modules
A signature characteristic of this malware family is its ability to perfectly mimic the user interface of popular Indian banking apps.
Meticulously crafted phishing pages validate user inputs with checks identical to those of legitimate apps verifying phone numbers, MPIN, debit card number, CVV, and ATM PIN before submission.
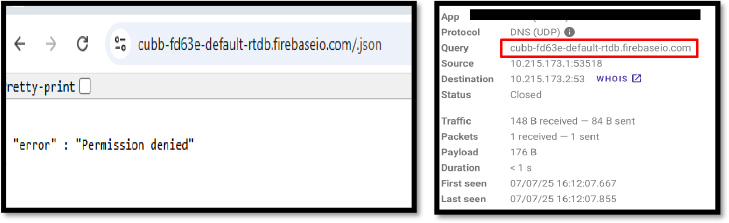
These details are then exfiltrated to attacker-controlled Firebase databases in real time, all without raising user suspicion.
Researchers observed modular class implementations for specialized data theft routines, such as separate modules for harvesting account login credentials, debit card data, and persistent autostarting.
The malware also hides its icon and launcher activity, running almost invisibly in the background. One of the more sophisticated aspects of the campaign is the abuse of legitimate cloud infrastructure.
Firebase Cloud Messaging (FCM) is weaponized not just for receiving remote commands but also for storing stolen data. Exfiltrated SMS, banking credentials, and device information are uploaded directly to the attackers’ Firebase Realtime Database.
Push notifications can even trigger malicious functionality like call forwarding via the injection of USSD codes, allowing threat actors to silently reroute victim calls without consent.
The research team also noted that access to the C2 server requires authentication, suggesting ongoing active operations.
Delivery mechanisms for these Android banking threats are diverse and increasingly sophisticated. Social engineering remains a favorite, with victims lured through SMS phishing (smishing), emails, messaging apps, and fake support calls.
Attackers have also optimized fake banking websites, search engine poisoning, adware, and even malicious QR codes for payload distribution.
There is growing evidence of supply chain attacks, such as malware preloaded on low-cost handsets and exploitation of system vulnerabilities (e.g., accessibility abuses and recent Android CVEs) to bypass protections.
The campaign underscores the attackers’ technical acumen, exploiting both human and system weaknesses to escalate privileges and maintain persistence, all while evading detection through stealthy techniques.
This new breed of banking malware represents a serious threat to the Indian financial ecosystem, combining user deception with technical exploitation at multiple layers.
By leveraging silent installations, permission abuses, Firebase-based remote control, and turnkey phishing modules, attackers are successfully bypassing security defenses and compromising unsuspecting users.
Institutions and individuals alike are urged to enforce stricter installation controls, conduct regular security audits, and remain vigilant against unsolicited app installation prompts and communications.
Indicators of Compromise (IOCs)
| Indicator | Type | Remarks |
|---|---|---|
| ee8e4415eb568a88c3db36098b7ae8019f4efe565eb8abd2e7ebba1b9fb1347d | Sha256 | Base Payload or Dropper |
| 131d6ee4484ff3a38425e4bc5d6bd361dfb818fe2f460bf64c2e9ac956cfb13d | Sha256 | Main Payload |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates