Cybersecurity researchers at McAfee have uncovered a sophisticated Android phishing campaign targeting Indian users by impersonating the government’s PM Surya Ghar electricity subsidy program.
The attack leverages a multi-stage social engineering operation involving YouTube videos, fake government websites, and malicious apps hosted on GitHub to steal financial information and gain remote control of infected devices.
Multi-Platform Distribution Network
The attack begins with promotional YouTube videos claiming users can receive government electricity subsidies through a mobile app.
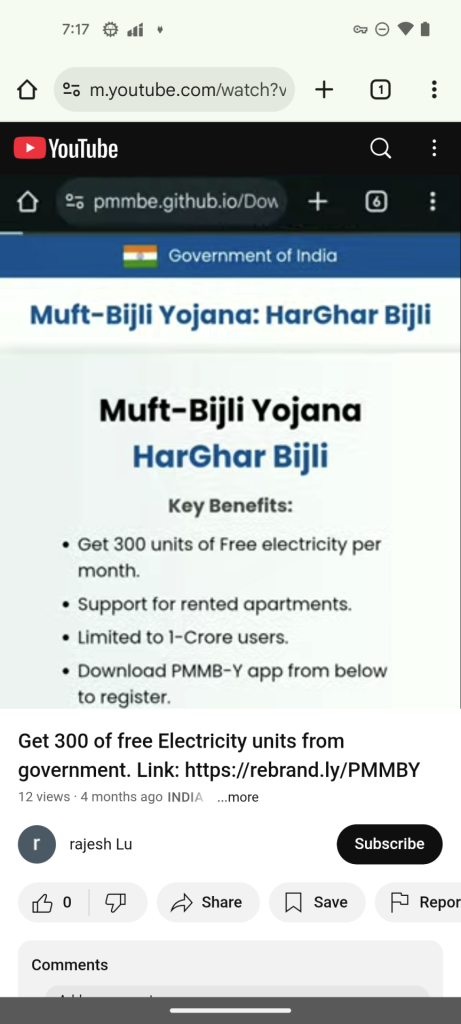
These videos contain shortened URLs in their descriptions that redirect victims to phishing websites hosted on GitHub, designed to mimic the official PM Surya Ghar portal at pmsuryaghar.gov.in closely.
The fraudulent site features fake registration instructions and displays a deceptive Google Play icon that downloads a malicious APK file from a GitHub repository instead of accessing the legitimate app store.
Security researchers discovered that both the phishing website source code and the APK file are hosted on the same GitHub repository, which likely allows them to bypass security detection systems and appear more legitimate.
The malicious repository has shown continuous development activity since October 2024, with frequent updates observed in recent weeks, indicating an active and evolving threat.
Advanced Evasion and Control Mechanisms
Once downloaded, the initial APK serves as a dropper that installs an embedded malware application called “PMMBY” under the guise of a “security update.”
During installation, victims are instructed to disable mobile data or Wi-Fi connections, potentially to reduce the effectiveness of cloud-based malware detection solutions.
The malware requests aggressive permissions, including contact access, SMS read/send capabilities, and phone call management.
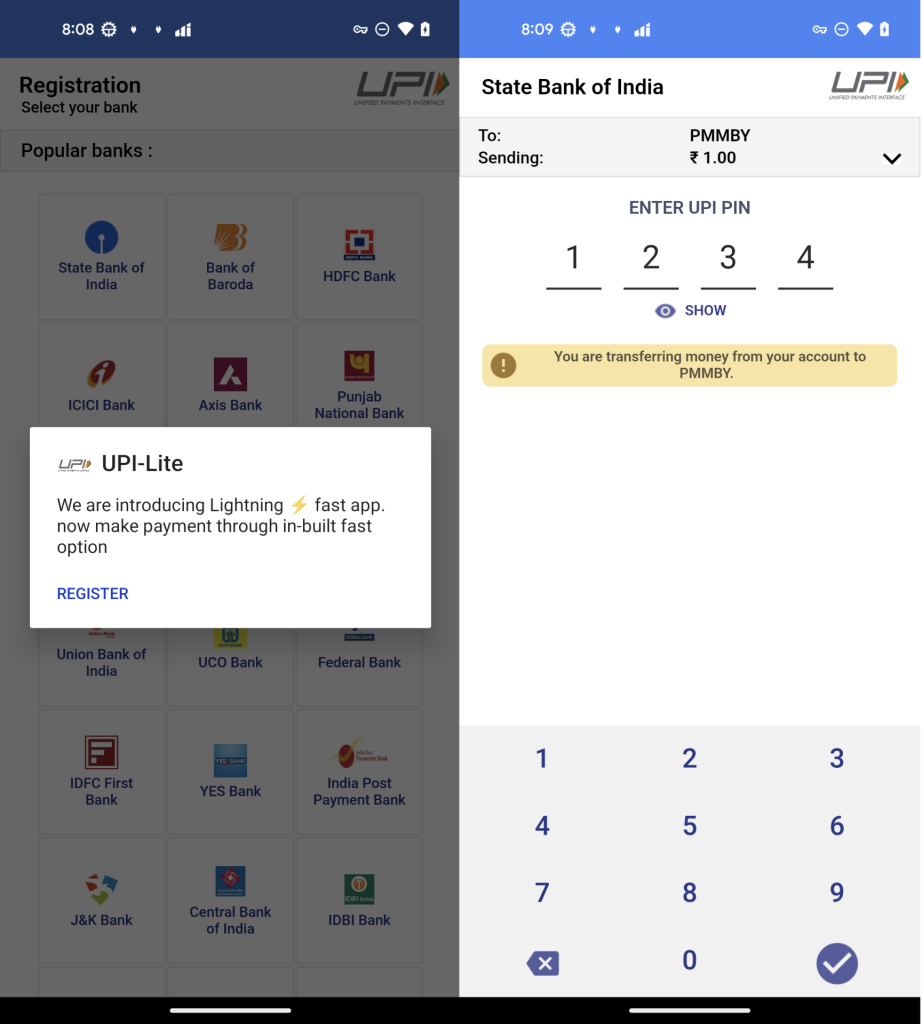
It then displays a fake electricity provider selection screen and registration form, ultimately directing users to enter their UPI PIN through a fraudulent HTML form hosted at sqcepo.replit.app/gate.htm.
The stolen financial credentials, including phone numbers, bank details, and UPI PINs, are uploaded to remote servers where attackers can exploit them for unauthorized transactions.
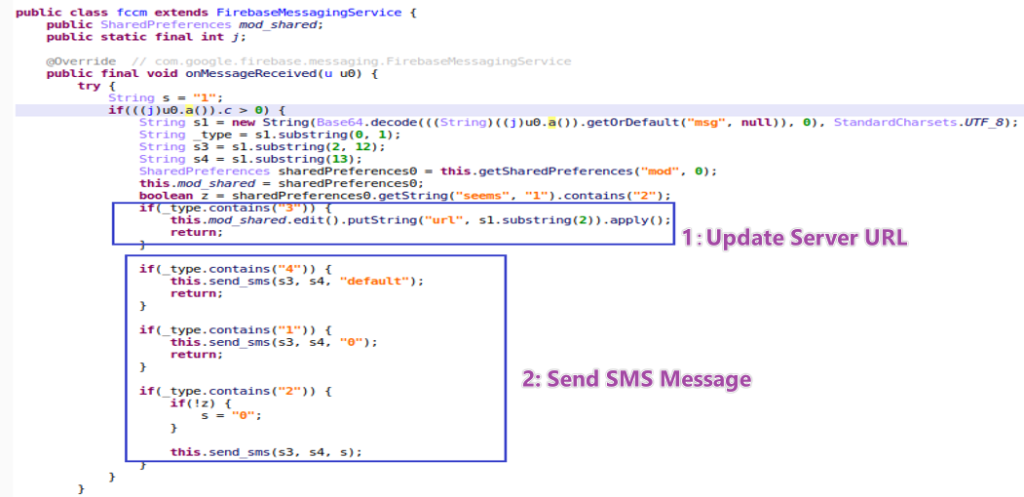
Beyond financial theft, the malware exhibits sophisticated behavioral capabilities. It automatically sends phishing SMS messages to the victim’s entire contact list, uploads incoming text messages to remote servers (potentially intercepting two-factor authentication codes), and accepts remote commands through Firebase Cloud Messaging (FCM).
Response and Protection
McAfee, as part of Google’s App Defense Alliance, reported the malicious applications to Google, resulting in the blocking of the associated FCM account.
The company also reported the GitHub-hosted repository to GitHub’s Developer Support Team, which subsequently removed it from the platform.
Security experts recommend users avoid downloading apps from unofficial sources, carefully review app permissions, and use reputable mobile security software with SMS protection capabilities to defend against such sophisticated social engineering attacks.
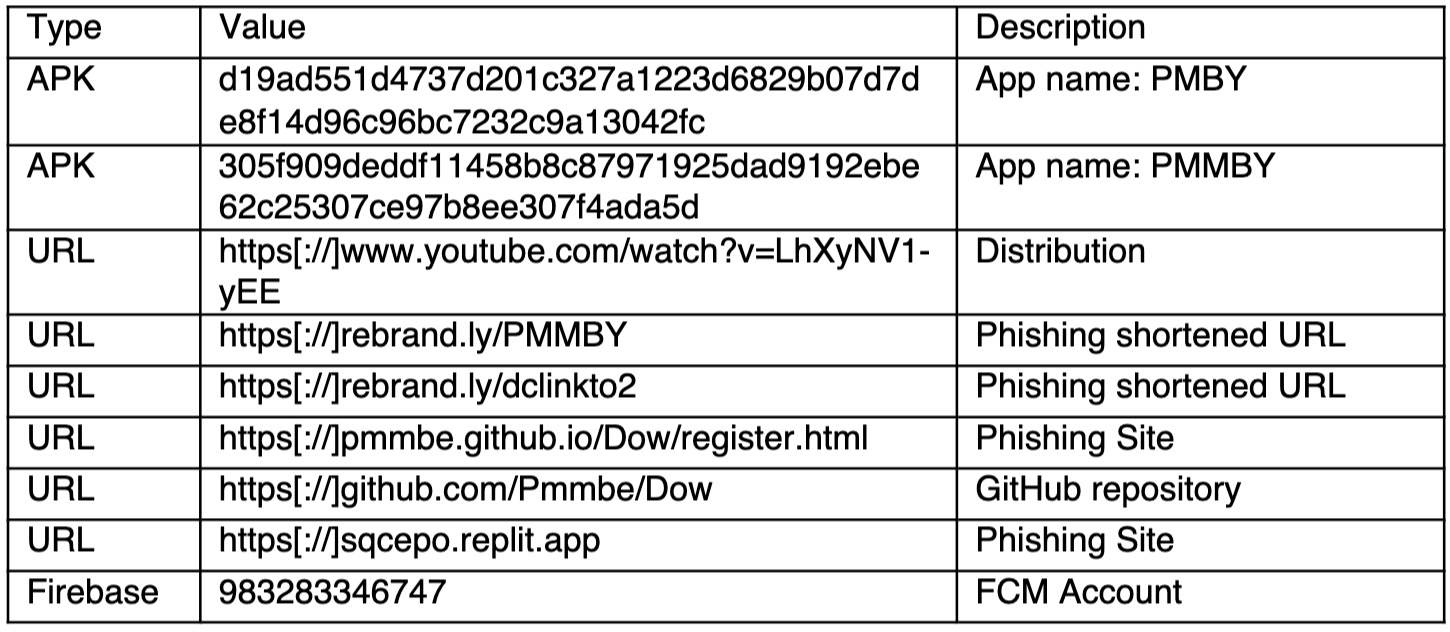
Indicators of Compromise (IOCs)
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates