Cybersecurity researchers at Socket have uncovered a sophisticated spamware campaign involving 131 Chrome extensions that target WhatsApp users through automated bulk messaging capabilities.
The extensions, which share identical codebases and infrastructure despite different branding, collectively affect at least 20,905 active users and represent a significant violation of both Chrome Web Store and WhatsApp policies.
Franchise-Style Spamware Operation
The malicious extension cluster operates through a franchise-style business model orchestrated by DBX Tecnologia, a Brazilian company that developed the original tool and licensed white-label versions to resellers.
Partners pay approximately $2,180 USD upfront to rebrand the extension with their own logos and names, with DBX promising 30 to 70 percent margins and recurring revenue between $5,450 to $15,270 USD.
Despite the varied branding across 131 different extensions, the entire cluster was published through only two developer accounts: [email protected] and [email protected]. The dominant publisher label appearing on 83 listings is WL Extensão and its variant WLExtensao.
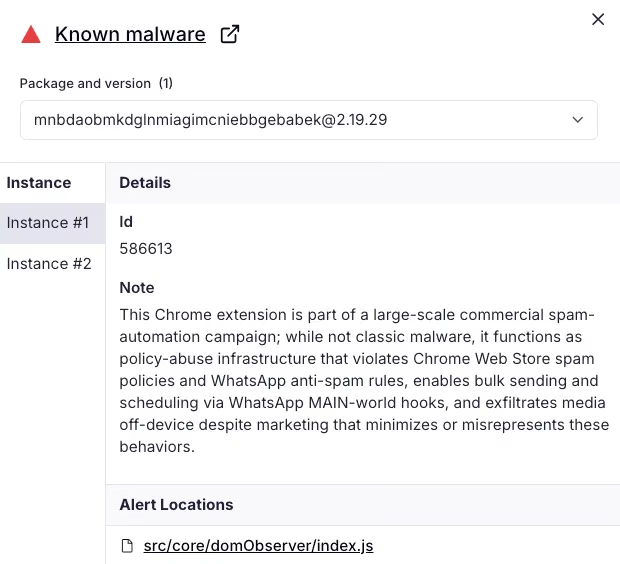
Socket’s AI Scanner flagged one extension, Organize-C (mnbdaobmkdglnmiagimcniebbgebabek), as malware due to its spamware behavior that directly injects code into WhatsApp Web pages.
The operation has run for at least nine months throughout 2025, with regular waves of rebrands and updates landing consistently, including new uploads and version bumps observed as recently as October 14, 2025.
Marketing materials for these extensions are supported by at least 23 near-identical websites promoting individual branded clones, backed by matching YouTube, LinkedIn, Instagram, and TikTok accounts that funnel buyers into monthly subscription plans.
Technical Exploitation Methods
The extensions employ sophisticated technical methods to inject malicious code at document-start directly into the WhatsApp Web interface, allowing them to run alongside WhatsApp’s legitimate scripts.
They utilize window.WPP.* helpers to automate message dispatch and employ a Manifest V3 service worker for scheduled sending functionality.
This technical approach enables the tools to bypass WhatsApp’s anti-spam enforcement mechanisms through highly configurable parameters including send intervals, pauses, and batch sizes specifically designed to evade detection algorithms.
DBX Tecnologia published YouTube tutorials explicitly demonstrating how to configure the extensions to avoid WhatsApp bans by manipulating traffic patterns and shaping outbound message flow.
The tutorial videos show controls for adjusting send intervals and batch sizes while explaining techniques to bypass WhatsApp’s anti-spam algorithms.
The extension interface provides users with templates that vary message text to reduce detection, enabling continuous bulk campaigns while evading automated security systems.
Policy Violations and Security Implications
The campaign directly violates Chrome Web Store spam and abuse policies that prohibit developers and affiliates from submitting multiple extensions providing duplicate experiences and forbid extensions from sending messages on a user’s behalf without confirmation.
Marketing materials falsely claim that Chrome Web Store presence implies rigorous security audits and privacy compliance, when Chrome’s process is actually a policy compliance review rather than a security certification.
WhatsApp’s Business Messaging policy requires explicit opt-in before contacting users, places the burden of proving consent on the sender, and prohibits spam or deceptive messaging.
These extensions fundamentally contradict those requirements by automating bulk outreach without recipient consent, shifting the defense burden to recipients who must block numbers and report abuse after receiving unsolicited promotional messages.
Socket has filed takedown requests with Chrome’s security team and requested suspension of the related publisher accounts.
The company recommends organizations implement Chrome extension protection tools to inventory every extension in use, surface permissions and host access, and block risky updates before they reach endpoints.
Security teams should enforce allowlists in Chrome Enterprise, restrict installs to approved extension IDs, and monitor permission changes over time while watching for lookalike domains as operators rotate infrastructure.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates