Cybersecurity researchers have identified a sophisticated malware campaign involving the Efimer script, a cryptocurrency-stealing trojan that has significantly expanded its distribution methods and capabilities since its emergence in October 2024.
The malware employs multiple attack vectors, including compromised WordPress sites, malicious torrents, and targeted email campaigns, while communicating with command-and-control servers through the Tor network to evade detection.
Email Distribution Campaign Mimics Legal Threats
The most recent wave of Efimer attacks involves mass email campaigns impersonating lawyers from major companies, falsely claiming recipients’ domain names infringe on trademark rights.
These deceptive messages threaten legal action while offering to purchase the allegedly infringing domain, with attachments supposedly containing “details” about the infringement and proposed buyout amounts.
The attack chain begins with ZIP attachments containing nested, password-protected archives with cleverly obfuscated password files.
Attackers use Unicode character U+1D5E6 instead of a standard uppercase “S” to prevent automated tools from efficiently extracting passwords.
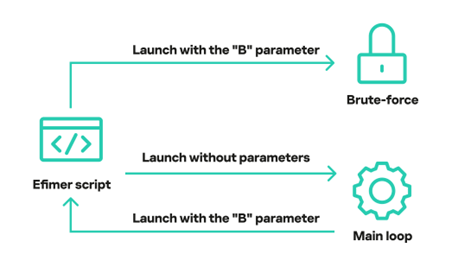
When victims execute the malicious “Requirement.wsf” file, the script checks for administrator privileges and either adds exclusions to Windows Defender or modifies registry keys for persistence.
Technical Capabilities and Infrastructure
Efimer operates as a ClipBanker-type trojan, designed to replace cryptocurrency wallet addresses copied to clipboards with attacker-controlled wallets.
The malware supports Bitcoin, Ethereum, Monero, Tron, and Solana wallets, using sophisticated matching algorithms to ensure replacement addresses share similar starting or ending characters with legitimate ones to avoid suspicion.
The Trojan employs multiple hardcoded URLs to download Tor proxy clients, ensuring continued operation even if some URLs become blocked.
It establishes communication with command-and-control servers at 30-minute intervals to avoid detection, using the onion address “cgky6bn6ux5wvlybtmm3z255igt52ljml2ngnc5qp3cnw5jlglamisad.onion”.
Expanding Attack Methods
Beyond cryptocurrency theft, Efimer deploys additional scripts for WordPress site compromise and email harvesting.
The “btdlg.js” component performs brute-force attacks against WordPress installations, using up to 20 concurrent processes to guess passwords from Wikipedia-derived word lists. Successfully compromised sites are used to host malicious torrents disguised as recently released movies.
The malware also includes an email harvesting script called “Liame” that collects email addresses from specified websites for future malicious campaigns.
This multi-faceted approach enables attackers to expand their infrastructure and target base continuously.
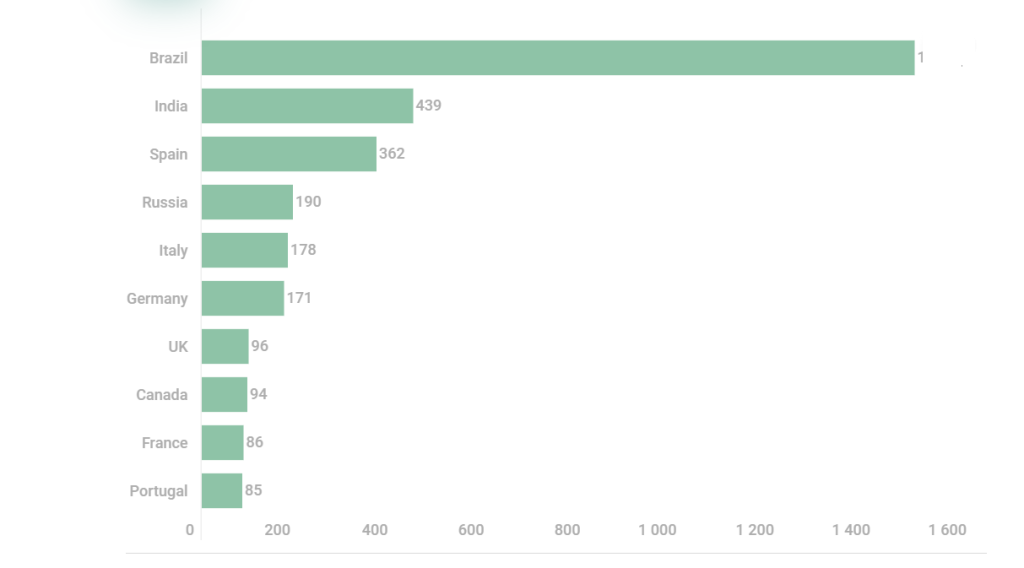
Kaspersky products detect this threat using multiple verdicts, including HEUR: Trojan-Dropper.Script.Efimer, HEUR: Trojan-Banker.Script.Efimer, and HEUR: Trojan-Spy.Script.Efimer.gen.
The sophisticated nature of Efimer’s distribution methods and technical capabilities represents a significant evolution in cryptocurrency-targeting malware campaigns.