Socket’s Threat Research Team has exposed a sophisticated supply chain attack involving 10 malicious npm packages that automatically deploy multi-stage credential theft operations upon installation.
The malware campaign, orchestrated by threat actor Andrew_r1 using the email parvlhonor@gmx[.]com, has been active since July 4, 2025, accumulating over 9,900 downloads across four months before detection.
The malicious packages employ typosquatting techniques to mimic legitimate JavaScript libraries, including typescriptjs (mimicking TypeScript), deezcord.js and dizcordjs (targeting discord.js), etherdjs and ethesjs (impersonating ethers.js), nodemonjs (imitating nodemon), react-router-dom.js, and zustand.js.
Each package leverages npm’s postinstall lifecycle hook to execute automatically when developers run npm install, launching the payload in a new terminal window to avoid detection during the installation process.
Four-Layer Obfuscation System Evades Detection
The attack employs an unprecedented four-layer obfuscation strategy designed to bypass static analysis tools. The outermost layer wraps the entire payload in a self-decoding eval wrapper that reconstructs and evaluates itself at runtime.
The second layer implements XOR decryption with a dynamically generated key based on hashing the decoder function itself, making automated decryption extremely difficult without code execution.
Additional layers include URL-encoding the payload string and control-flow obfuscation using switch-case state machines with hexadecimal and octal arithmetic.
This combination creates a nearly impenetrable barrier to traditional malware analysis tools, requiring full JavaScript execution to reveal the malicious functionality.
Cross-Platform Credential Harvesting Operation
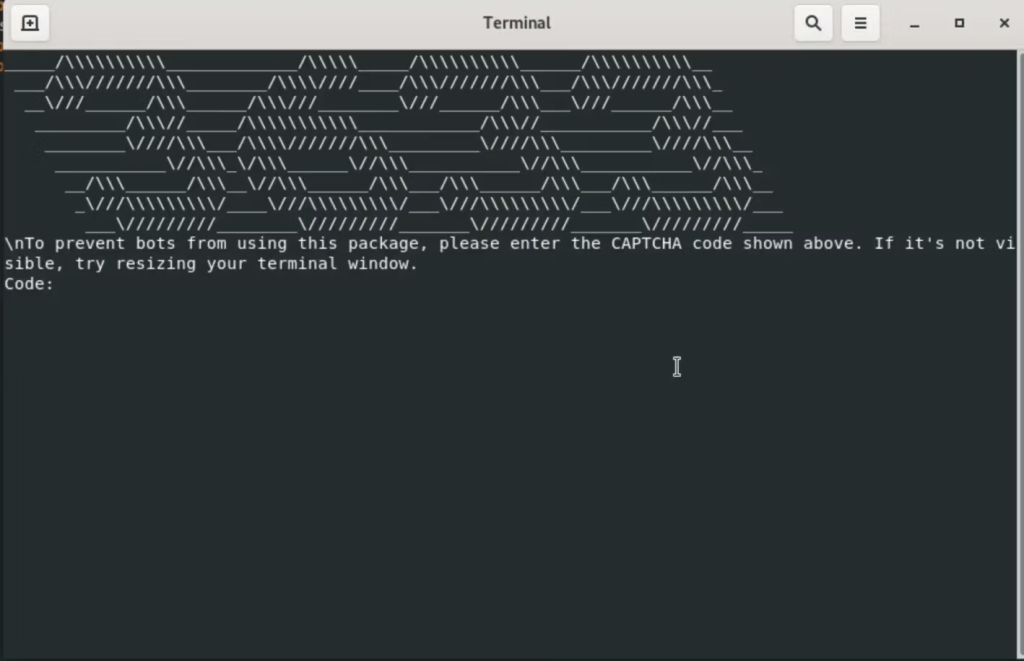
Once executed, the malware displays a fake CAPTCHA prompt to appear legitimate while performing IP fingerprinting by sending victim information to the command-and-control server at 195[.]133[.]79[.]43.
After any user interaction with the fake CAPTCHA, the system automatically downloads a 24MB PyInstaller-packaged information stealer called data_extracter, tailored to the victim’s operating system.
The credential harvester targets multiple storage mechanisms across Windows, Linux, and macOS systems, including system keyrings, browser password stores, SSH keys, OAuth tokens, JWT authentication, and configuration files containing API keys.
The malware systematically scans file systems for AWS credentials, Kubernetes configurations, Docker registry access, and Git authentication tokens, providing threat actors with comprehensive access to development and production infrastructure.
Organizations should immediately audit their dependencies for these malicious packages and assume any affected systems are fully compromised.
Critical security measures include resetting all stored credentials, revoking authentication tokens, enabling multi-factor authentication, rotating SSH keys, and implementing comprehensive monitoring for unauthorized access across all connected services and infrastructure.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates