A recent malware campaign has hijacked WordPress websites by embedding concealed PHP functions that fetch and serve attacker-controlled JavaScript, compromising every visitor’s session.
The breach was traced to a small code snippet appended to the active theme’s functions.php file, demonstrating how minimal modifications can have a significant impact.
The injected PHP leverages WordPress hooks to execute on every page load, silently contacting a command-and-control server to download malicious payloads and embed them directly into the site’s front end.
Infection Discovery and Entry Point
The initial indicator of compromise appeared as an unexpected external script loading on the site’s pages. A view of the page source revealed a single script tag referencing an unknown domain.
Further investigation via PublicWWW identified the same script on seventeen different websites, suggesting a widespread distribution network. A VirusTotal URL scan confirmed the domain’s reputation was blacklisted by seventeen security vendors, affirming malicious intent.
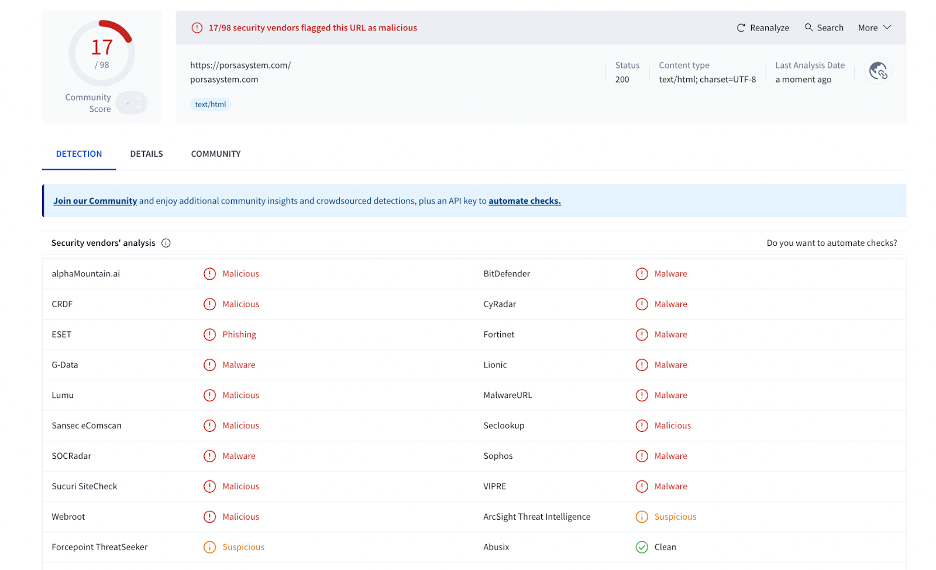
A thorough file integrity scan pinpointed the intrusion to the theme’s functions.php file. Attackers embedded a deceptively simple function ti_custom_javascript() at the bottom of the file.
This function is hooked into WordPress’s wp_head action, ensuring it executes on every page render. The PHP code establishes a POST request to hxxps://brazilc[.]com/ads[.]php, then echoes the server’s response into the HTML head section.
By fetching content at runtime, the attackers avoid storing JavaScript directly on the compromised server, reducing the likelihood of detection by static scanning tools.
Malicious Payload Mechanics
Upon contacting the C2 server, the PHP loader retrieves a dynamic JavaScript payload designed for stealth and persistence. The first component loads an external script from porsasystem[.]com/6m9x[.]js, which acts as a traffic distributor.
This distributor script orchestrates forced redirects, pop-ups, and other drive-by malware behaviors based on victim characteristics. Because the distributor controls subsequent payloads, attackers can adjust malicious activities in real time.
The second component of the payload utilizes an invisible 1×1 pixel iframe to conceal operations further. Inside this iframe, the JavaScript mimics legitimate Cloudflare assets, specifically the cdn-cgi/challenge-platform/scripts/jsd/main.js script.
By using data-cfasync='false' and async attributes, the injection bypasses Cloudflare Rocket Loader optimizations and ensures non-blocking execution.
This dual strategy of external script distribution and hidden iframe evasion exemplifies advanced tactics for avoiding detection by web application firewalls and endpoint security solutions.
Mitigation and Defense Strategies
Cleaning a compromised WordPress site begins with removing the injected code from functions.php and any associated backdoors. A comprehensive file integrity monitoring solution should run frequent server-side scans to detect unexpected modifications.
Implementing a Web Application Firewall (WAF) helps block malicious Command and Control (C2) communications and bad bot traffic, while enforcing unique, strong passwords for all administrative, FTP, and database accounts, thereby preventing unauthorized access.
Keeping WordPress core, themes, and plugins up to date remains the first line of defense against known vulnerabilities. Site owners should disable direct file editing in the dashboard to limit opportunities for code injection.
Regularly reviewing server and application logs can surface unusual POST requests or repetitive C2 check-ins. Finally, adopting a principle of least privilege for file and database permissions reduces the attack surface.
This infection underscores how attackers exploit minimal PHP code injections to weaponize WordPress installations.
By combining dynamic script loading with stealthy iframe techniques, threat actors maintain persistent, adaptive control over compromised websites. Vigilant patch management, proactive monitoring, and layered security solutions are essential to thwarting such sophisticated campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates