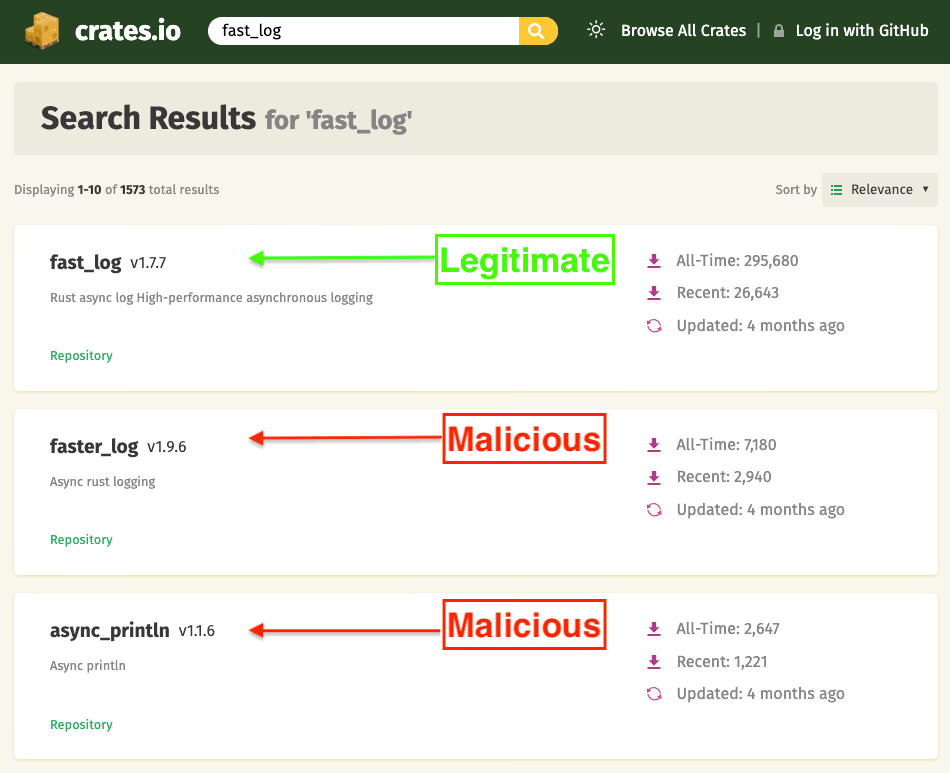
Socket’s Threat Research Team has uncovered two malicious Rust crates, faster_log and async_println, that impersonate the legitimate fast_log logging library.
Published on May 25, 2025, by threat actor aliases RustGuruMan and DumbnBased, these crates collectively amassed 8,424 downloads before being removed.
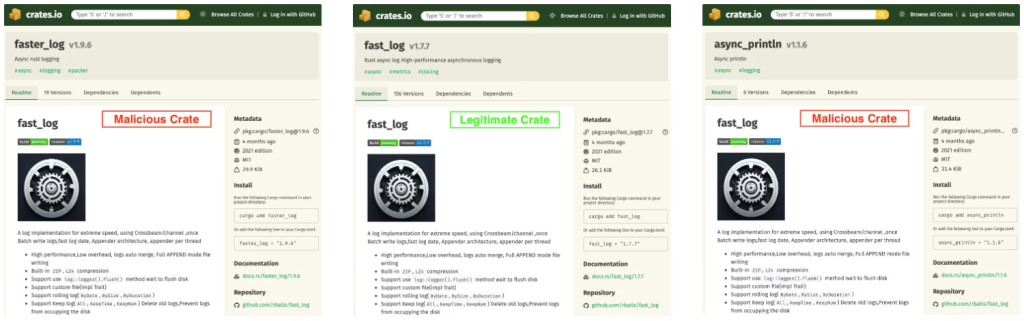
Under the guise of functional logging, each crate embeds routines that scan local Rust source files for Solana and Ethereum private keys, then exfiltrate any matches via HTTP POST to a hardcoded Cloudflare Workers endpoint at https://mainnet[.]solana-rpc-pool[.]workers[.]dev/.
Malicious Functionality Hidden Behind Logger Cover
Both crates include complete logging implementations copied from the genuine fast_log project to evade cursory inspection. The core malicious logic resides in a Packer struct that recurses through directories, reads .rs files, and applies three regular expressions to extract:
- Ethereum private keys matching
"0x[0-9a-fA-F]{64}" - Base58-encoded strings 32–44 characters long, typical of Solana keys
- Bracketed byte arrays (e.g.,
[0x12,0xAB,…]or[12,34,…]) that may represent raw key bytes
Each detected item is wrapped in a FoundItem A record containing the key type, exact value, source file path, and line number, then batched into a PackResult The JSON payload was POSTed to the attacker’s C2.
The crates rely solely on standard Rust libraries and the reqwest HTTP client, ensuring cross-platform execution on Linux, macOS, or Windows. No user prompts, local alerts, or build-time hooks are employed; the scanning runs at application or test runtime.
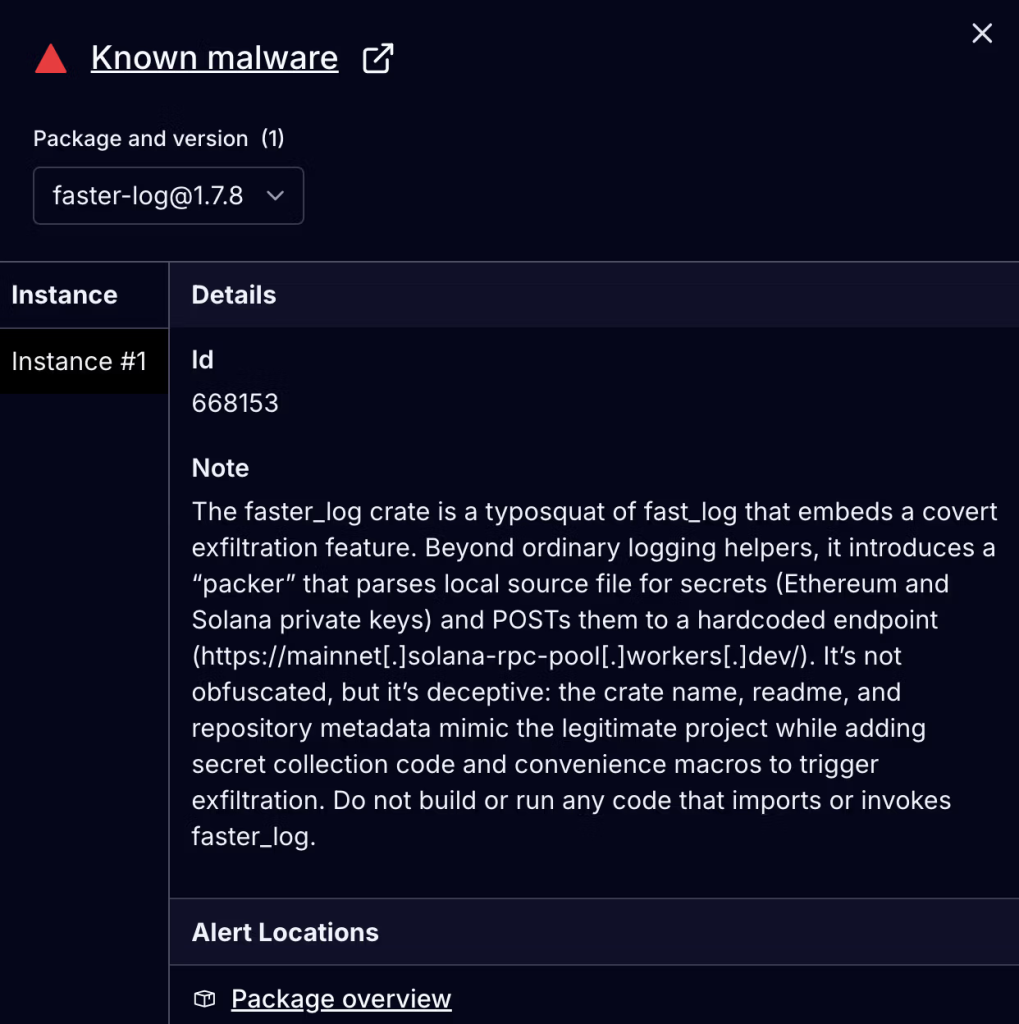
Within an hour of Socket’s report, the Crate’s security team preserved malicious code for analysis, removed the package listings from crates.io, locked both publisher accounts, and published an advisory detailing their investigation.
No downstream dependents existed for faster_log or async_println, minimizing immediate impact. Legitimate fast_log at nearly 296,000 downloads remains unaffected.
This incident highlights the growing threat to the supply chain posed by typosquatted libraries that reuse project metadata to bypass manual review.
Defenders should treat this as a supply chain compromise: remove any lingering dependencies on faster_log or async_println, then rotate all secrets that may appear in source, tests, or fixtures.
Implement file-level secret scanning, enforce network egress controls in developer and CI environments, and write detections for HTTP POST requests containing JSON arrays of key data.
Socket’s ecosystem of defenses, including the Socket GitHub App for PR scanning, the Socket CLI for install-time warnings, and the Socket browser extension for package-page annotations, provides layered protection against future typosquats and covert exfiltration routines.
Integrating these controls alongside robust secret hygiene will help block minimal-code, high-impact supply chain attacks before they compromise critical wallet keys.
Indicators of Compromise (IOCs)
Malicious Crates
Threat Actor’s Crates Aliases
dumbnbasedrustguruman
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates