A sophisticated information-stealing campaign leveraging pirated gaming software has been actively targeting users since May 2025, according to cybersecurity researchers at Cyble Research and Intelligence Labs (CRIL).
The Maranhão Stealer malware represents a significant evolution in credential harvesting techniques, combining social engineering tactics with advanced evasion capabilities to compromise user accounts and cryptocurrency wallets.
The threat actors behind this campaign have strategically positioned themselves within the gaming community, distributing malicious software through cloud-hosted platforms disguised as popular game launchers, cheats, and pirated software.
Examples include files named “Fnafdoomlauncher.exe,” “essentiallauncher.exe,” and “Silent Client.exe,” which contain Inno Setup installers that deploy Node.js compiled binaries designed for credential extraction.
Technical Infrastructure and Persistence Mechanisms
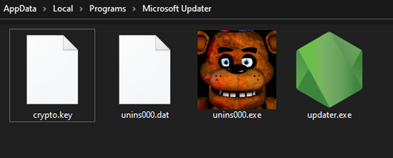
Once executed, the malware establishes a sophisticated footprint on victim systems by creating a deceptive directory structure under “%localappdata%\Programs\Microsoft Updater.”
The malware achieves persistence through multiple techniques, including registry Run keys and scheduled tasks, while simultaneously marking its components with hidden and system attributes using Windows’ attrib command to evade detection.
The stealer performs comprehensive system reconnaissance by executing Windows Management Instrumentation (WMI) queries to collect hardware specifications, operating system details, and disk information.
Additionally, it contacts external services like ip-api.com to gather geolocation data, enabling threat actors to profile victims and assess the value of compromised systems.
Maranhão Stealer’s most notable capability involves sophisticated browser exploitation through reflective DLL injection.
The malware targets multiple browsers, including Google Chrome, Microsoft Edge, Brave, and Opera, systematically extracting browsing history, stored credentials, cookies, and session tokens.
Advanced Browser Exploitation Techniques
The injection process involves spawning browser instances in headless mode, then injecting malicious code directly into browser memory using low-level Windows APIs such as NtAllocateVirtualMemory and CreateThreadEx.
This technique bypasses Chrome’s AppBound encryption, a security feature designed to protect sensitive user data. The malware creates named pipes for inter-process communication, allowing the injected code to transmit stolen credentials back to the primary process for staging and exfiltration.
The stolen data is exfiltrated to attacker-controlled infrastructure, primarily through the domain “maranhaogang[.]fun” and associated API endpoints. These include specialized URLs for infection reporting, victim tracking, and data upload operations.
The malware also establishes communication with IP address 104.234.65.186 to notify attackers of successful compromises.

CRIL’s analysis reveals that newer variants have evolved significantly from their initial May 2025 versions, transitioning from crude implementations using PsExec to more sophisticated execution methods through direct Win32 API calls.
This evolution demonstrates the threat actors’ commitment to improving their operational security and maintaining persistent access to victim systems.
Organizations should implement advanced endpoint detection and response solutions, network monitoring for suspicious outbound traffic, and application allowlisting to defend against this evolving threat landscape.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates