A newly uncovered phishing campaign is exploiting Facebook’s trusted infrastructure to steal business credentials at scale.
According to Check Point researchers, attackers have leveraged the Facebookmail.com domain and Meta’s legitimate Business Suite invitation feature to deliver tens of thousands of convincing phishing emails, successfully bypassing traditional email security filters.
Exploiting Facebook’s Trust
With over 5.4 billion global social media users, Facebook remains the world’s largest online platform and a vital marketing tool for small and medium-sized businesses.
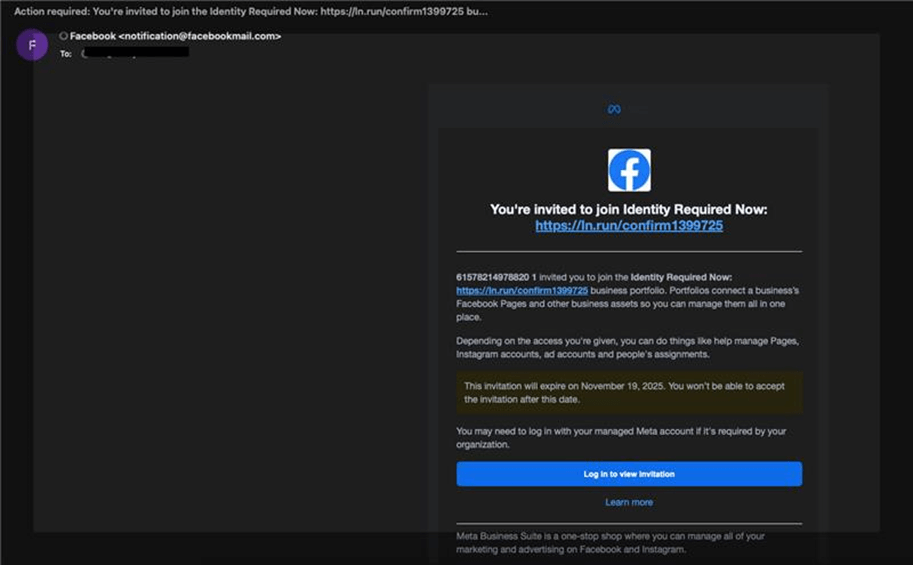
Attackers have seized on this dependence by crafting phishing emails that appear identical to legitimate Meta Business notifications.
These emails carry urgent subject lines such as “Meta Agency Partner Invitation” or “Account Verification Required” and are sent from the authentic facebookmail.com domain commonly used by Meta for business communications.
This design choice eliminates one of the main red flags users are trained to spot: suspicious or spoofed sender addresses.
How the Attack Works
The campaign begins when threat actors create fraudulent Facebook Business pages that mimic official Meta branding, including logos and page names. Using the Business Suite’s invitation system, the attackers send mass “invites” that embed malicious URLs.
Once clicked, victims are redirected to phishing sites hosted on Vercel.app domains that replicate Meta’s login pages.
Check Point’s telemetry identified over 40,000 phishing messages targeting 5,000 organizations across North America, Europe, Canada, and Australia.
The industries most affected include automotive, real estate, education, finance, and hospitality, which often rely on Facebook Ads for customer engagement.
One firm reportedly received more than 4,200 identical phishing messages in a single wave, suggesting the campaign uses templated automation for maximum reach.
Technical Implications and Defense
The success of this operation lies in its abuse of legitimate Meta tools. Because the emails originated from an authorized Meta domain, they slipped through multiple layers of domain reputation and SPF/DKIM validation.
This technique exemplifies a broader shift toward platform-based phishing, in which attackers weaponize trusted digital ecosystems rather than merely spoofing them.
Check Point has updated its SmartPhish engine to detect and block Meta-themed phishing using behavioral analysis and AI-driven pattern recognition.
Experts recommend that organizations implement multi-factor authentication, expand employee awareness training beyond domain-spotting, and verify any Meta Business notifications directly through the official platform rather than clicking embedded links.
As phishing actors increasingly co-opt legitimate services, the boundaries between trustworthy communication and social engineering continue to blur. This campaign underscores how even the most respected platforms can become unwitting conduits for large-scale credential theft.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates