A new information-stealing malware dubbed Mi6 Windows Stealer is being actively marketed on dark web forums, according to a recent alert from the cyber threat intelligence platform DarkWebInformer.
The threat actor behind this malware is leveraging underground channels to sell the stealer as a malware-as-a-service (MaaS) product, enabling even low-skilled criminals to deploy sophisticated attacks targeting Windows systems.
This development follows a broader trend of info-stealers like Lumma, RedLine, and SamsStealer evolving their tactics to bypass defenses and monetize stolen data.
Technical Analysis of Mi6 Stealer
According to the post from DarkWebInformer, the Mi6 Windows Stealer appears to follow the architectural patterns of contemporary .NET-based stealers observed in campaigns such as SamsStealer and Lumma.
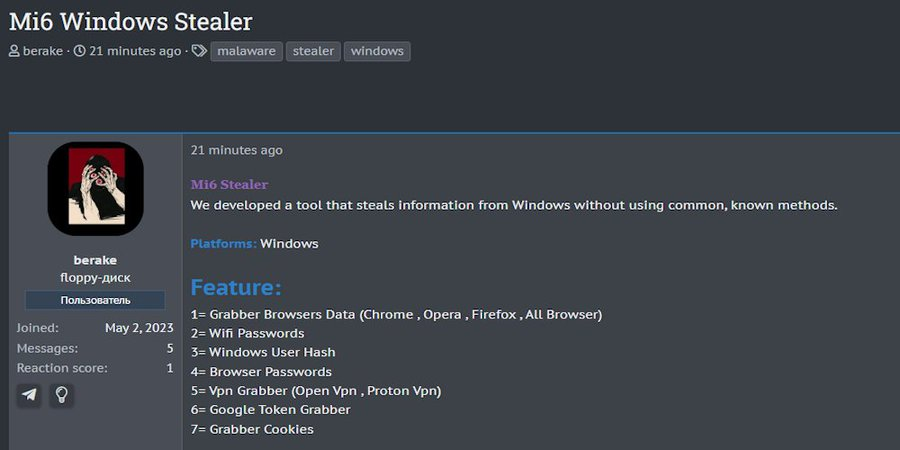
Initial analysis suggests the malware focuses on extracting credentials, cookies, and financial data from browsers like Chrome, Edge, and Firefox, while also targeting cryptocurrency wallets and messaging applications like Telegram and Discord.
Like its counterparts, Mi6 likely employs asynchronous execution flows to evade detection, using temporary directories (e.g., %LocalAppData%\Temp\) to stage stolen data before exfiltration.
Security researchers hypothesize that the stealer uses process hollowing or DLL sideloading techniques—similar to those observed in Lumma Stealer campaigns—to inject malicious code into legitimate executables such as msiexec.exe or explorer.exe.
This allows the payload to masquerade as benign system activity while harvesting sensitive information.
Distribution and Attack Chain
Threat actors are distributing Mi6 Stealer through phishing campaigns and fake software updates, mirroring tactics used by TA2726 and TA2727, who recently deployed Lumma Stealer via compromised websites displaying counterfeit browser update prompts.
In these scenarios, users are redirected to domains like cloudfasterapp[.]com, where they download malicious MSI installers that sideload malware through trojanized DLLs.
Another observed vector involves malicious PowerShell scripts hosted on platforms like Pastebin, which download and execute payloads from attacker-controlled servers.
For example, a script might use Base64 encoding to fetch a ZIP archive containing Mi6 Stealer, which then deploys secondary modules for credential harvesting.
Expanded Targeting and Data Exfiltration
The stealer’s advertisement highlights capabilities to extract:
- Browser-stored passwords and autofill data
- Session cookies for account hijacking
- Discord tokens and Telegram session files
- Cryptocurrency wallet seeds (e.g., Exodus, MetaMask)
- System information for fingerprinting victims
Stolen data is compressed into ZIP archives (e.g., Backup.zip) and exfiltrated via free file-sharing services like GoFile.io or directly to command-and-control (C2) servers using HTTP POST requests.
The integration with Telegram’s API allows attackers to receive real-time alerts when new data is captured, streamlining the monetization process through dark web marketplaces or ransomware deployments.
Mitigation Strategies
To counter such threats, organizations must adopt multilayered defenses:
- Endpoint Detection and Response (EDR): Deploy solutions capable of identifying code injection and anomalous process behavior, such as unexpected memory writes to
explorer.exe. - Network Traffic Analysis: Block connections to known malicious domains like
berb.fitnessclub-filmfanatics.comand CDNs associated with fake update campaigns. - User Education: Train employees to recognize phishing lures, especially fake CAPTCHA pages or browser update prompts that initiate PowerShell executions.
- Dark Web Monitoring: Services like Microsoft Defender’s dark web scanning can alert organizations if corporate credentials or assets appear in stealer logs or breach databases.
Industry and Law Enforcement Response
Microsoft’s Threat Intelligence Center (MSTIC) has documented over 300 active threat actors in 2024, including MaaS operators distributing stealers like Mi6.
Cross-industry initiatives, such as the FBI’s domain seizure programs tracked by tools like FBI_Watchdog, aim to disrupt these campaigns by taking down C2 infrastructure.
However, the persistence of dark web markets highlights the need for continued vigilance.
As Mi6 Stealer gains traction, its modular design suggests threat actors will incorporate evasion techniques from malware families like RedLine, which combines credential theft with ransomware payloads.
Proactive threat-hunting and intelligence-sharing platforms like DarkWebInformer remain critical to identifying emerging stealer variants before they achieve widespread impact.
Also Read: