Cybercriminals have weaponized the demand for pirated games, using trusted piracy sites like Dodi Repacks to spread advanced malware that evades even robust security mechanisms such as Microsoft Defender SmartScreen and popular adblockers like uBlock Origin.
Recent analysis uncovers a highly deceptive infection chain that exposes downloaders to the sophisticated HijackLoader malware family.
Technical Analysis: Multi-stage Evasion and Payload Delivery
The infection begins when users navigate piracy forums or Google search results touting safe downloads, often with community claims that adblockers ensure safety.
However, the download journey becomes a labyrinth of redirects beginning at Dodi Repacks, passing through sites like zovo[.]ink and downf[.]lol, and ultimately landing on a MEGA-hosted archive.
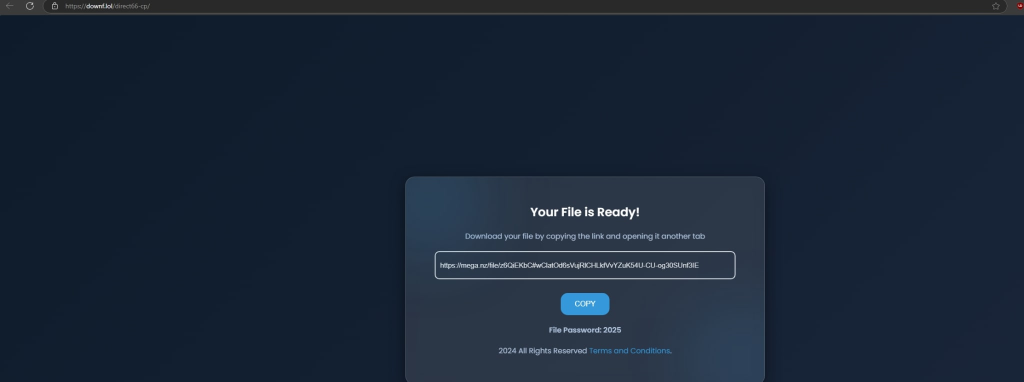
Even with uBlock Origin installed, these malicious redirects remain unobstructed, demonstrating the limited protection provided by adblockers against such threats.
Inside the downloaded archive, a bloated DLL (DivXDownloadManager.dll, over 500 MB) serves as the first malicious vehicle.
This inflation tactic thwarts many online scanners due to file-size restrictions. Upon extraction, the malware performs module stomping on system DLLs (notably shell32.dll), injecting its next-stage payload.
The loader retrieves configuration data from auxiliary files (such as quintillionth.ppt and paraffin.html), decrypts them using SIMD instructions or custom XOR routines, then decompresses with APIs like RtlDecompressBuffer.
HijackLoader utilizes sophisticated anti-analysis and anti-debug behaviors:
- Checks for virtual machines via hypervisor and vendor ID inspections.
- RAM and processor counts to evade sandboxes.
- Verification of system artifacts (e.g., usernames, computer names).
- If checks pass, the loader achieves persistence by manipulating environment variables, copying components to %APPDATA%, and executing the payload with custom mutex logic.
The modular nature of HijackLoader supports upwards of 40 plug-in modules with capabilities ranging from API resolution (via CRC32 hashing) and stack spoofing to aggressive unhooking of ntdll and wow64cpu.
Its anti-detection arsenal includes manipulating stack return addresses and remapping suspicious API calls, which present formidable obstacles to behavioral monitoring and endpoint security.
Widespread Abuse and Bypassed Defenses
Distribution is rampant: searching for cracked software often leads to poisoned links among top search results.
Campaigns have even leveraged streaming platforms like TIDAL and file-sharing sites such as weeklyuploads[.]click and MEGA, all serving HijackLoader variants delivering final-stage malware like LummaC2 or Redline Stealer.
Critical finding: Both Microsoft Defender SmartScreen and popular adblockers are readily bypassed as threat actors continually rotate domain infrastructure, maintain active development, and alter payload behavior in response to security vendor detections. This establishes pirated software downloads as a persistently high-risk activity, even with advanced user precautions.
Indicators of Compromise
| Domains | Risk Level |
| directsnap.click | High |
| readyf1.lol | High |
| weeklyuploads.click | High |
| File Names | Description | Detection Name | SHA256 Hashes |
| DivXDownloadManager.dll | DLL with hijacked control flow which loads paraffin.html and quintillionth.ppt | DLL/HijackedExecution.A | 5649F7535E388572096DDDCF3C50A66C51D189F31DC7769470E9A78C5B2EC34C |
| quintillionth.ppt | Configuration info specifying the file to be loaded | Generic Trojan.XAE | 8EF22B49AF1D7E67657BCFAC9D02DD1BFCC1D3AE20D1BBCB1A60C99D023D18D5 |
| paraffin.html | HijackLoader | Trojan/HijackLoader.RW | 0D24D4E72B7B22017C6FDE7B1A2DC1A1E1AD63B97B5811DC02C221AA68D9D00C |
| N/A | Final Payload, LummaC2 | ACL/Malware Generic.BRHJ | E575A3A2FBF1916D3AFB0A1ABFD8479C02B5B677550883F9A5D0E22EE738030A |
| blackthorn.vhd | HijackLoader | Trojan/HijackLoader.RW | 04677C4C70D9F61F011B0AC744F2DC5353AC0D1B4AA5D9EC37A291968D2A0B79 |
| N/A | Final Payload, MSIL Trojan | T-TRO-ZZA | EECDEA0F63F4E54D8EFB542700F3 |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates