Security researchers at Datadog have disclosed a significant vulnerability in Microsoft’s Entra ID that allows attackers to escalate privileges to the Global Administrator level through the exploitation of first-party applications.
The vulnerability, detailed in a comprehensive report published this week, demonstrates how Service Principals (SPs) with specific administrative roles can hijack Microsoft’s built-in Office 365 Exchange Online application to gain unauthorized access to hybrid user accounts.
Technical Exploitation Method Revealed
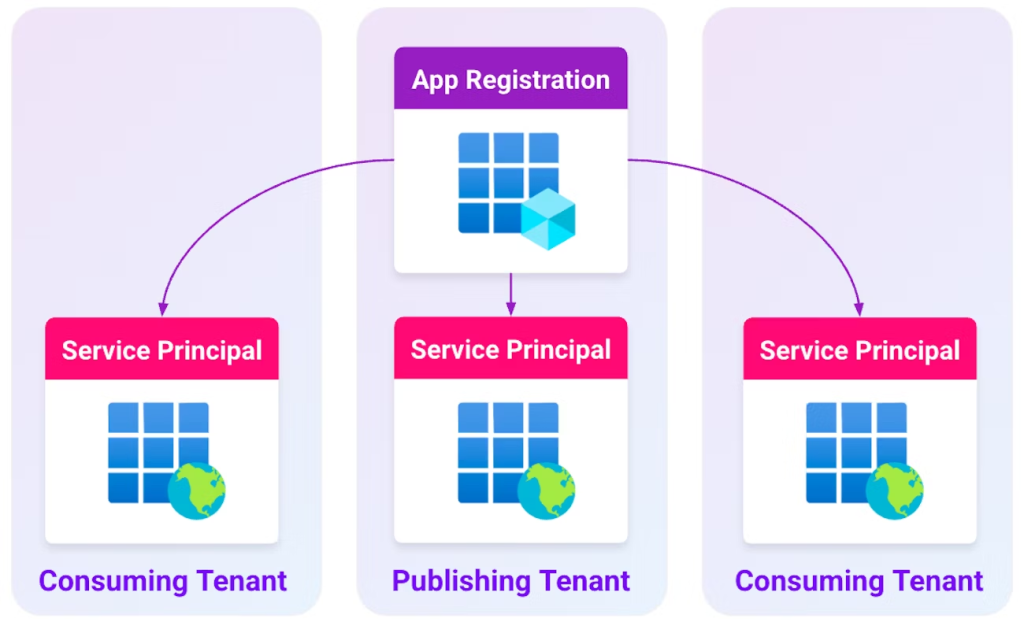
The attack vector centers on Service Principals assigned the Cloud Application Administrator role, Application Administrator role, or Application.ReadWrite.All permission.
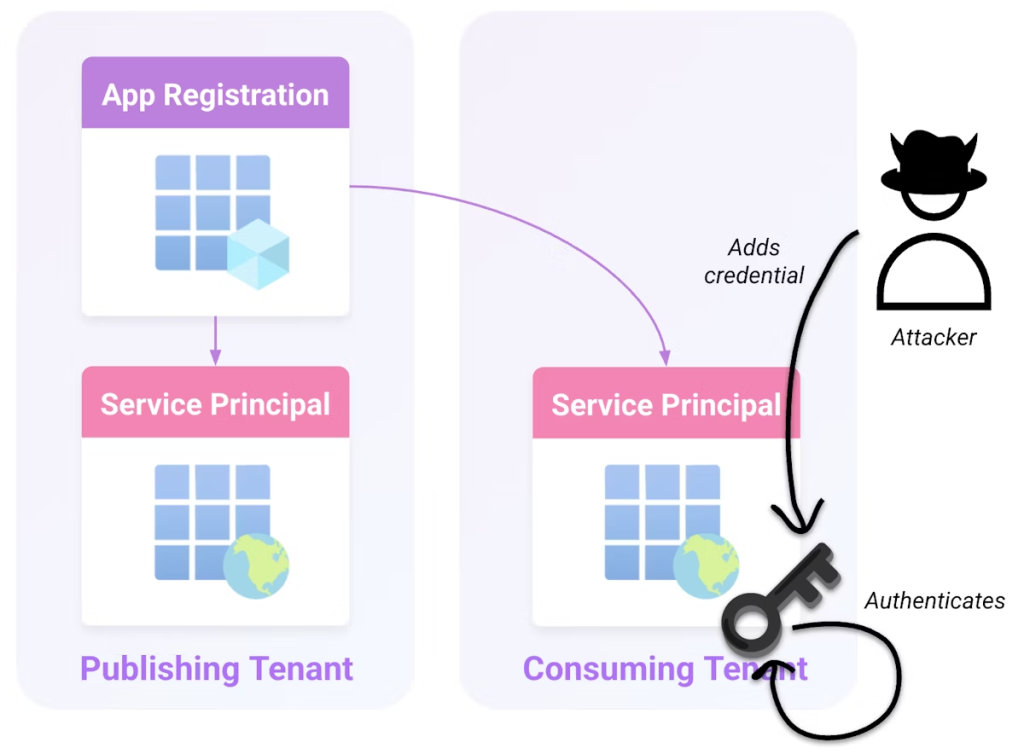
These privileged accounts can exploit the Office 365 Exchange Online SP (Client ID: 00000002-0000-0ff1-ce00-000000000000) by adding malicious credentials to the application’s local Service Principal.
The exploitation process involves several critical steps using Microsoft Graph API endpoints.
Attackers first authenticate using the client credentials grant flow with a POST request to /{tenant-id}/oauth2/v2.0/token, including parameters such as client_id, client_secret, and scope=https://graph.microsoft.com/.default.
Once authenticated, the compromised Office 365 Exchange Online identity provides access to powerful permissions, including Domain.ReadWrite.All and Group.ReadWrite.All.
The most dangerous aspect involves using the Domain.ReadWrite.All permission to add a new federated domain through the /v1.0/domains endpoint, followed by configuring federation settings via /v1.0/domains/{domain}/federationConfiguration.
This allows attackers to forge SAML tokens for any hybrid user synchronized between on-premises Active Directory and Entra ID.
Microsoft’s Response and Security Implications
Following responsible disclosure to Microsoft Security Response Center (MSRC) on January 14, 2025, Microsoft initially acknowledged the issue and confirmed replication by March 20, 2025.
However, on May 14, 2025, MSRC concluded that this behavior represents “misconfiguration, not a security bypass” and is consistent with documented risks of the Application Administrator role.
The vulnerability particularly affects hybrid environments where users possess the onPremisesImmutableId property, making them vulnerable to SAML token forgery.
Attackers can leverage tools like AADInternals to execute commands, such as Open-AADIntOffice365Portal -ImmutableId with forged certificates, bypassing multi-factor authentication requirements through the federatedIdpMfaBehavior configuration set to acceptIfMfaDoneByFederatedIdp.
Defensive Measures and Monitoring Requirements
Security teams should implement comprehensive monitoring for credential additions to applications, specifically watching for “Add service principal credentials” and “Update application – Certificates and secrets management” activities in Core Directory logs.
Organizations must also monitor domain-related events, including “Add unverified domain,” “Verify domain,” and “Set federation settings on domain” activities.
Microsoft recommends enforcing cloud-only administrators for privileged roles, ensuring Global Administrator accounts have no ties to on-premises Active Directory.
The company also advises configuring the app instance property lock setting, enabled by default for applications created after March 2024, to prevent credential additions to associated Service Principals.
This disclosure highlights the complex security landscape of hybrid cloud environments and the importance of carefully managing application permissions and federated authentication configurations in enterprise Microsoft 365 deployments.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates