Microsoft Threat Intelligence has identified a financially motivated threat group tracked as Storm-2657 orchestrating “payroll pirate” campaigns against U.S. organizations, with a concentration in higher education.
By compromising employee accounts, the actor gains unauthorized access to HR-SaaS platforms like Workday, allowing them to redirect salary disbursements to attacker-controlled bank accounts stealthily.
These incursions exploit weak or non-existent multifactor authentication (MFA) and leverage advanced social engineering rather than platform vulnerabilities, underscoring the urgent need for phishing-resistant authentication controls.
Attack Overview
Storm-2657 initiates campaigns by sending highly tailored phishing emails to faculty and staff. Between March and June 2025, eleven university accounts were compromised and used to distribute further phishing lures to nearly 6,000 recipients across twenty-five institutions.
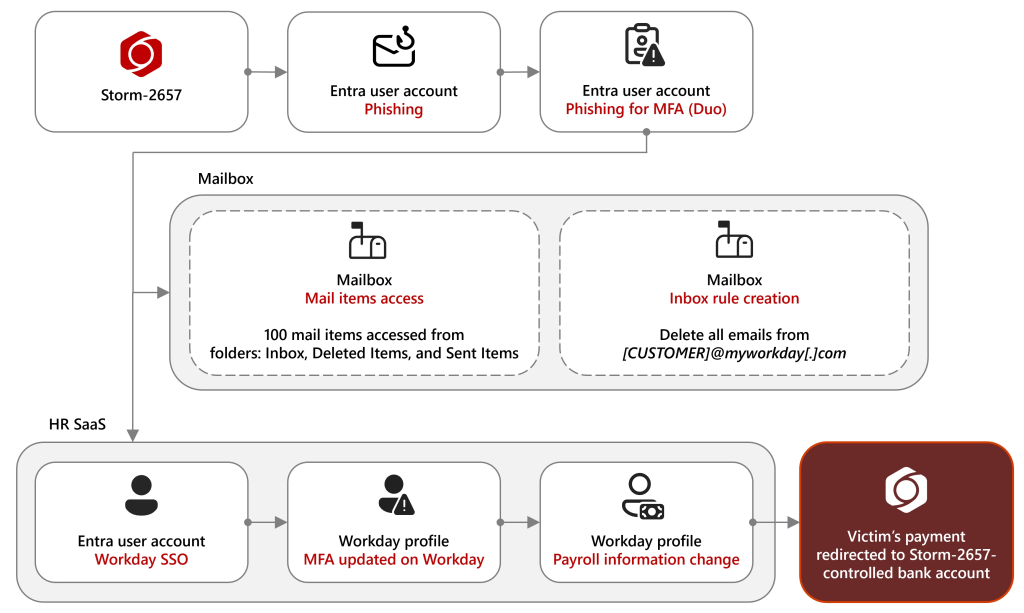
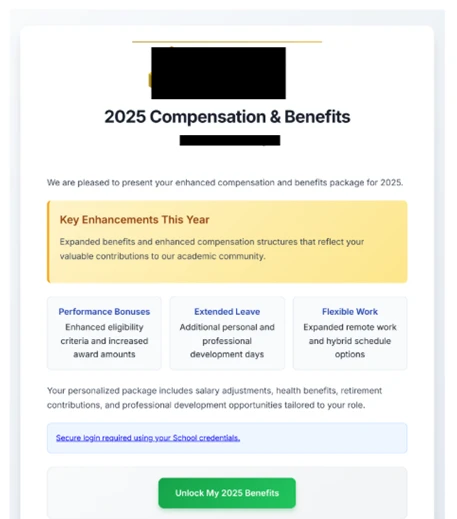
Initial phishing messages often impersonated campus health authorities, warning of communicable illness exposure and directing targets to Google Docs links that deployed adversary-in-the-middle (AiTM) proxies. These proxies harvest real-time MFA codes when victims log in.
After harvesting credentials and MFA tokens, the actor accesses Exchange Online mailboxes to establish persistence.
They often create inbox rules, named after memorable characters, to delete or move any incoming notifications from Workday that could alert victims to unauthorized payroll changes.
In one observed incident, a single rule suppressed all “Direct Deposit” and “Payment Elections” alerts, effectively blinding victims to financial alterations.
Once email defenses are evaded, Storm-2657 leverages single sign-on credentials to log into Workday. The actor navigates to the “Manage Payment Elections” function, updating the victim’s bank account details to redirect future paychecks.
They may also enroll their own phone numbers as MFA devices via Duo or Workday’s native settings, bypassing legitimate user approvals and securing ongoing access.
Mitigation and Detection Guidance
To block “payroll pirate” attacks, organizations must eliminate reliance on legacy MFA methods and deploy phishing-resistant, passwordless authentication such as FIDO2 security keys, Windows Hello for Business, or Microsoft Authenticator passkeys.
Enforce conditional access policies that require phishing-resistant MFA for all users with HR system privileges. Regularly audit MFA device registrations and disable any unrecognized phone or hardware tokens.
Monitoring Exchange Online and Workday audit logs is critical to detect post-compromise activity. Analysts should hunt for suspicious inbox rule creations filtering messages from “@myworkday.com” with delete or move actions.
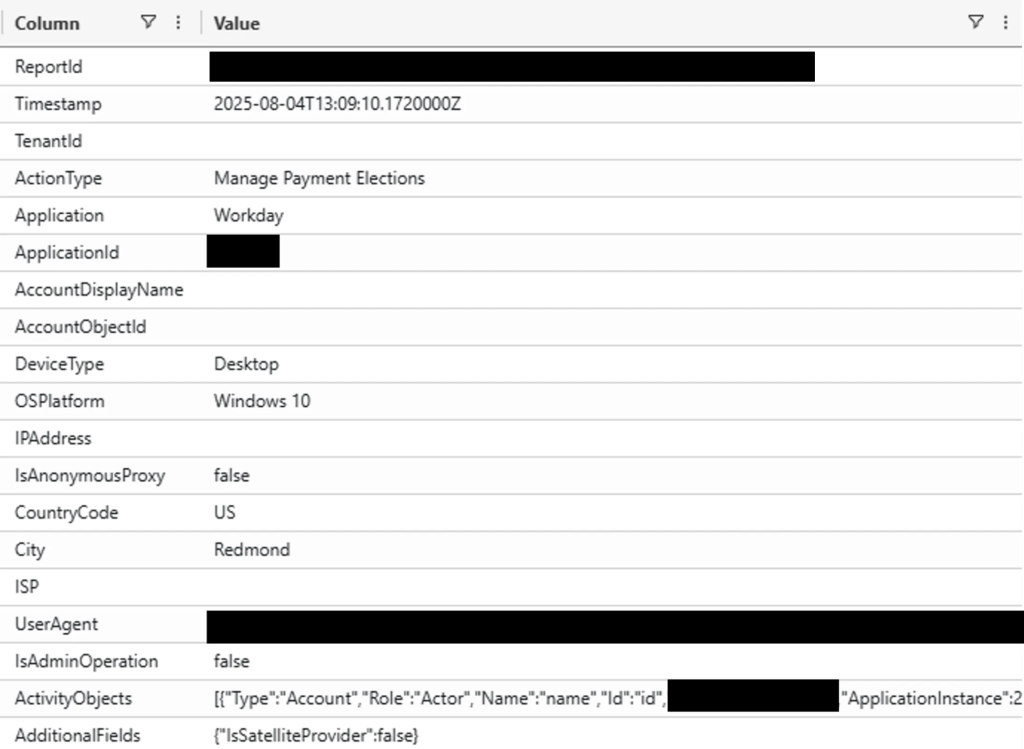
In Microsoft Defender XDR, queries against CloudAppEvents can surface “New-InboxRule” and “Set-InboxRule” actions containing “DeleteMessage” parameters.
Similarly, reviewing CloudAppEvents for Workday actions like “Change My Account” or “Manage Payment Elections” can reveal unauthorized payroll adjustments.
If alerts indicate compromise, immediately reset affected user credentials and revoke sessions. Remove malicious inbox rules and reconfigure MFA devices to approved, phishing-resistant methods.
Revert any unauthorized payroll changes and notify internal finance teams to prevent future payment redirects. By combining robust authentication controls with vigilant monitoring of SaaS audit logs, organizations can disrupt Storm-2657’s campaigns and safeguard employee payroll integrity.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates