Microsoft is enhancing the security of its Teams collaboration platform by introducing an automatic warning system that flags malicious URLs in chat messages.
As part of Microsoft Defender for Office 365, the new feature leverages threat intelligence and machine learning to identify harmful links shared in both internal and external conversations.
A public preview for enterprise customers is scheduled to begin in early September 2025, with worldwide general availability expected in mid-November 2025.
Once fully deployed, the warning banners will appear on Teams desktop, web, Android, and iOS apps, offering an additional layer of defense against phishing, spam, and malware attacks.
Enhanced Protection Against Malicious Links
To address the surge in link-based threats targeting collaboration tools, Teams will automatically display a warning banner on any message containing a URL deemed malicious by Defender’s detection engines.
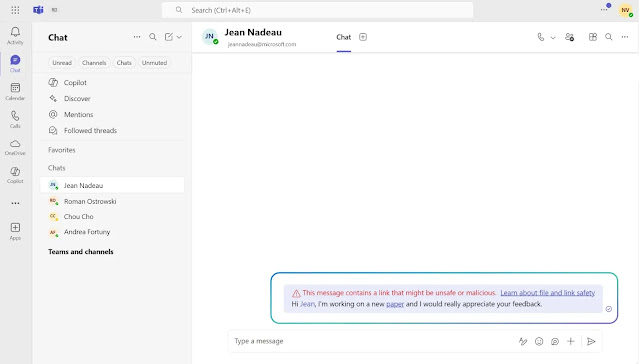
Users receive an onscreen alert before clicking, clearly indicating that the shared link may be unsafe.
The system continuously scans URLs against Microsoft’s threat intelligence database, and flagged links are highlighted in real time.
Senders also receive notifications when one of their shared links is identified as potentially harmful, allowing them to edit or delete the message and prevent inadvertent exposure across the organization.
Zero-Hour Auto Purge:
A standout capability of this update is its retroactive link scanning, known as Zero-hour Auto Purge (ZAP).
Even if a URL passes initial checks, Defender can detect newly emerging threats up to 48 hours after delivery.
If a link is subsequently classified as malicious, the system automatically applies a warning banner to the historical message thread.
When ZAP is configured to block messages outright, that action takes precedence, removing the threat before end users can interact with the link.
This retroactive protection ensures that organizations remain safe from evolving threats that may not have been detectable at the time of sharing.
During the public preview period beginning in September, IT administrators must opt in to enable the warning feature.
Settings are managed via the Teams Admin Center under “Messaging settings” or through PowerShell commands, allowing customization to align with each organization’s security policies.
Once the feature reaches general availability in November, it will be enabled by default for all tenants.
Administrators are advised to review the configuration options, update internal security documentation, and brief support teams on the new functionality to guarantee a smooth transition.
With over 320 million monthly active users, this layered defense marks a significant step toward safeguarding enterprise communications against sophisticated phishing campaigns.
Find this Story Interesting! Follow us on Google News, LinkedIn and X to Get More Instant Updates