Microsoft has issued a warning about a large-scale malvertising campaign that has compromised nearly one million devices worldwide.
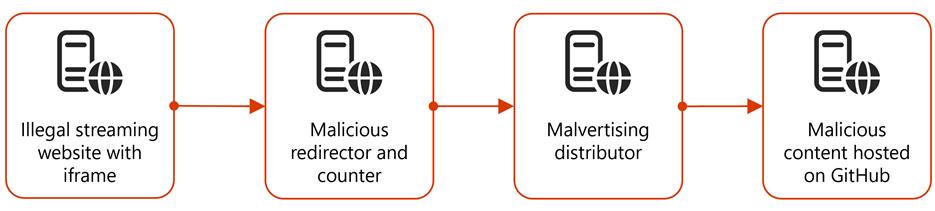
The attack, which began in early December 2024, leverages malicious redirects from illegal streaming websites to deliver malware hosted on platforms like GitHub, Discord, and Dropbox.
This campaign highlights the indiscriminate nature of the threat, affecting both consumer and enterprise devices across various industries.
Malware Delivery and Impact
The malware is delivered through a multi-stage attack chain.
Initially, users are redirected from streaming sites to GitHub via a series of malicious redirectors embedded in iframes.

Once on GitHub, the first-stage payload establishes a foothold on the device, acting as a dropper for subsequent malicious files and scripts.
These additional payloads include information stealers like Lumma Stealer and Doenerium, which collect system and browser information.
In some cases, the NetSupport remote monitoring and management (RMM) software is deployed alongside these stealers, further compromising device security.
The malware uses living-off-the-land binaries and scripts (LOLBAS) such as PowerShell.exe and RegAsm.exe to evade detection and exfiltrate user data.
It achieves persistence by modifying registry run keys and adding shortcuts to the Windows Startup folder.
The campaign’s modular approach allows threat actors to tailor their tactics based on environmental factors, including security configurations and user activity.
Mitigation and Recommendations
Microsoft recommends several mitigation strategies to reduce the impact of this threat.
These include strengthening Microsoft Defender for Endpoint configurations by enabling tamper protection, network protection, and web protection.
Additionally, users should run endpoint detection and response (EDR) in block mode to automatically remediate malicious artifacts.
Implementing multifactor authentication (MFA) and leveraging phishing-resistant authentication methods are also crucial in preventing similar attacks.
Microsoft has collaborated with GitHub to take down the malicious repositories involved in the campaign, emphasizing the importance of prompt action against such threats.