A newly discovered ransomware strain, Midnight, has drawn attention from the security community for both its lineage and its unusual vulnerabilities.
Identified by Gen researchers, Midnight closely mirrors the structure of the infamous Babuk ransomware, which first appeared in 2021 before its source code leak fueled a surge in copycat variants.
Babuk gained notoriety for its use of advanced encryption frameworks such as HC256 and ECDH, enabling fast, partial encryption while maximizing operational disruption.
Midnight inherits much of Babuk’s Ransomware-as-a-Service (RaaS) architecture, expanding on it with modified file encryption routines and configurable command-line parameters.
However, these changes introduced critical weaknesses that security researchers have successfully exploited to enable free data recovery.
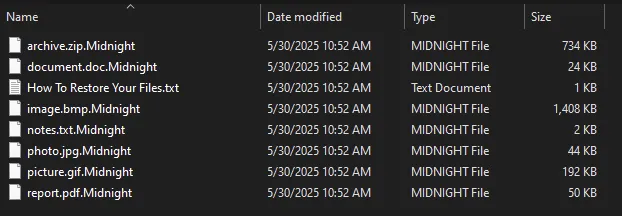
The ransomware typically appends “.Midnight” or “.endpoint” extensions to compromised files, though some configurations insert the extension directly into the file content rather than renaming it.
Victims often find a ransom note titled How To Restore Your Files.txt placed across affected directories, while a mutex named “Mutexisfunnylocal” prevents multiple instances of the encryption process from running simultaneously.
Some builds produce diagnostic logs, such as Report. Midnight or debug. An endpoint that helps researchers reverse-engineer the malware.
Cryptographic Flaws Enable Decryption
Unlike Babuk’s mixed HC256 and ECDH scheme, Midnight employs the ChaCha20 stream cipher to encrypt data and RSA to protect the encryption keys.
The RSA-encrypted ChaCha20 key and its SHA256 checksum are appended to the end of each encrypted file, maintaining uniformity across observed variants.
The ransomware’s intermittent encryption mechanism targets only segments of larger files, improving performance but leaving potential recovery points. Using this design quirk, researchers were able to isolate decryption keys and reconstruct affected data without paying a ransom.
Technical analysis revealed command-line arguments such as “/e” to alter file extension behavior, “/n” to encrypt network drives, and “–paths=” to target specific directories.
Early variants focused on high-value file types like database and backup formats (.mdf, .bak, .sql), but newer versions indiscriminately encrypt nearly all non-executable files.
Security specialists, including those from Avast and Norton, have published a fully functional decryptor that relies on exploiting Midnight’s implementation flaws. Both 64-bit and 32-bit Windows versions are available, offering victims a legitimate recovery option.
Users are advised to run the decryptor with administrative privileges and enable the automatic backup option before initiating the restoration process.
Researchers emphasize that, despite its decryptable flaws, Midnight underscores a growing trend among ransomware developers to iterate on leaked codebases such as Babuk.
Organizations are urged to maintain offline backups, restrict privilege escalation, and monitor system logs for mutex or file extension indicators associated with Midnight.
IoCs: Ransomware Samples
dd9de77c6e17093b0b2150b3f0c66e8526369ba68fb7b9a5758ff9274d85342e
3d9a71cfec82fef531227465f40d9106e671ef162fa3ab21119e2ee08612e0aa
300c46bf17e8bd0cd5ac800a33e1d27ef9001aecef1f98965414bf9c33af19e0
1e58448808006de410ddb31a4d6ff8292aa70168f69f2b7e08144d6090d5084d
aa8a043fd3d64fc96864cf5361bbb82012cc4b2e1a909c747038edcf2b4369e7
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates