The AhnLab Security Intelligence Center (ASEC) has identified a sophisticated attack campaign targeting poorly managed MS-SQL servers, where threat actors are deploying XiebroC2, an open-source command and control framework that rivals CobaltStrike in functionality.
Diagram illustrating the stages of a data breach attack from initial link delivery to data exfiltration
Attack Vector and Initial Compromise
The attack begins with threat actors exploiting publicly accessible and unprotected MS-SQL servers that use weak or default credentials.
Once attackers gain initial access through credential-based attacks, they immediately begin installing various malware payloads, with cryptocurrency miners being the primary focus of these campaigns.
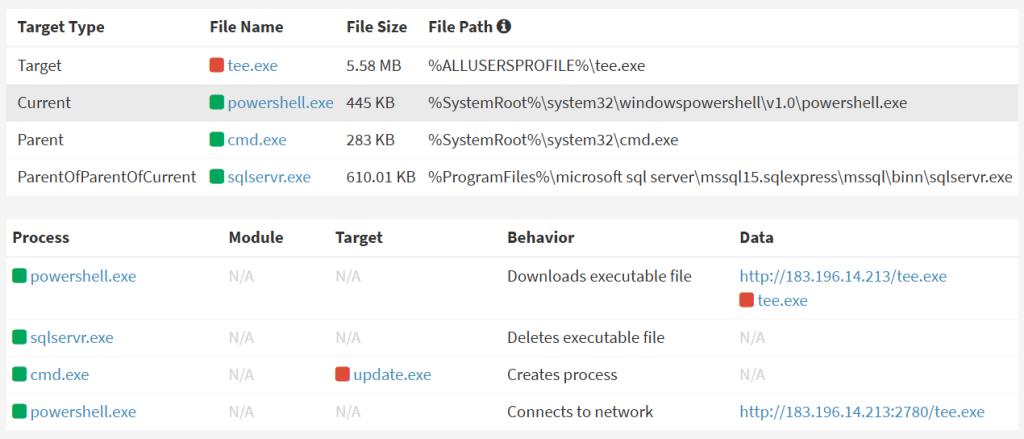
The attack methodology follows a predictable pattern observed in Microsoft SQL Server compromises. After successful authentication, attackers deploy JuicyPotato, a privilege escalation tool that exploits specific privileges within process tokens to elevate system access.
This step is crucial because MS-SQL service processes typically run with limited privileges by default, restricting the malware’s ability to perform advanced malicious activities without proper escalation.
Following privilege escalation, attackers utilize PowerShell to download and deploy XiebroC2 directly onto the compromised system, establishing persistent remote access capabilities.
XiebroC2 Framework Analysis
XiebroC2 represents a significant threat as an open-source alternative to commercial C2 frameworks. Written in the Go programming language, the framework supports multiple operating systems, including Windows, Linux, and macOS, making it highly versatile for cross-platform attacks.
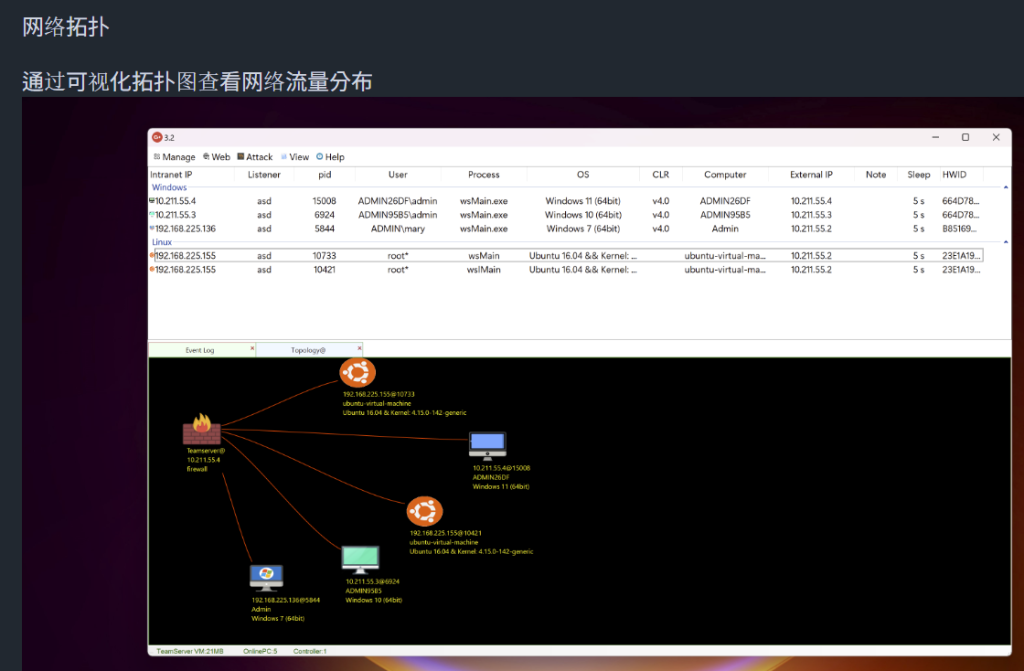
Network and command console view of C2 framework activity showing compromised Windows hosts, process communications, and privilege details for remote administration
The framework provides comprehensive remote control capabilities, including reverse shell access, file and process management, network monitoring, reverse proxy functionality, and screenshot capture.
Upon execution, XiebroC2 collects critical system information, including process IDs, hardware IDs, computer names, and user accounts, before establishing communication with its command and control server.
In the analyzed attack, XiebroC2 was configured to communicate with the command server at IP address 1.94.185[.]235 on port 8433, using WebSocket protocols and AES encryption with the key “QWERt_CSDMAHUATW” for secure communications.
Mitigation and Defense Strategies
Organizations can protect against these attacks through several security measures. Database administrators should implement strong, regularly rotated passwords for all MS-SQL accounts and avoid using default or easily guessable credentials.
Brute-force protection mechanisms should be enabled to prevent dictionary attacks against database services.
For publicly accessible database servers, network-level security controls, including firewalls and access control lists, should restrict external connections to authorized sources only.
Regular security updates and endpoint protection solutions should be maintained to detect and prevent malware installations.
The continued targeting of MS-SQL servers demonstrates the importance of proper database security configuration, as compromised systems provide attackers with valuable network footholds for lateral movement and data exfiltration activities.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates