A sophisticated spear-phishing campaign attributed to APT MuddyWater is actively targeting Chief Financial Officers and finance executives across multiple continents, leveraging legitimate remote-access tools to establish persistent control over compromised systems.
The campaign employs multi-stage infection techniques, beginning with socially engineered emails impersonating Rothschild & Co recruiters that direct victims to Firebase-hosted phishing pages.
Advanced Multi-Stage Payload Delivery
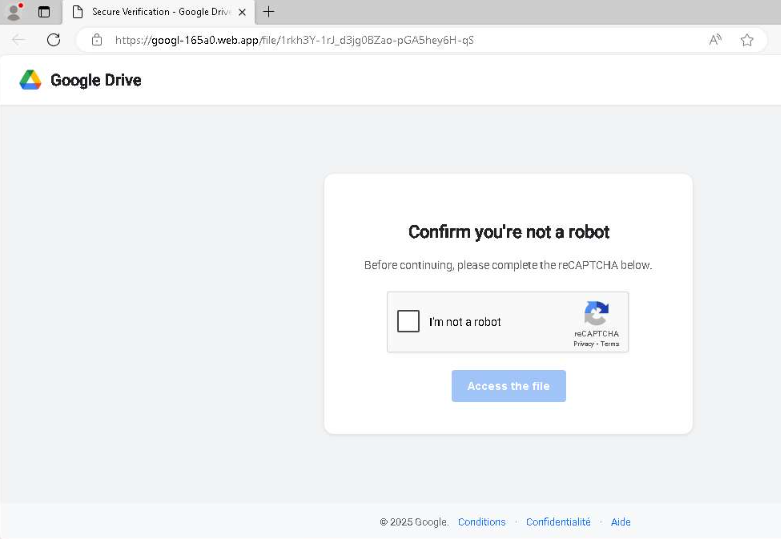
The attack chain begins with Firebase-hosted domains using custom CAPTCHA challenges that mask AES-encrypted redirect logic. Upon solving fake math-based verification prompts, victims are redirected to malicious landing pages hosting ZIP archives containing VBScript downloaders.
Security researchers identified infrastructure evolution from the original IP address 192.3.95.152 to the current operational host at 198.46.178.135, indicating active campaign updates.
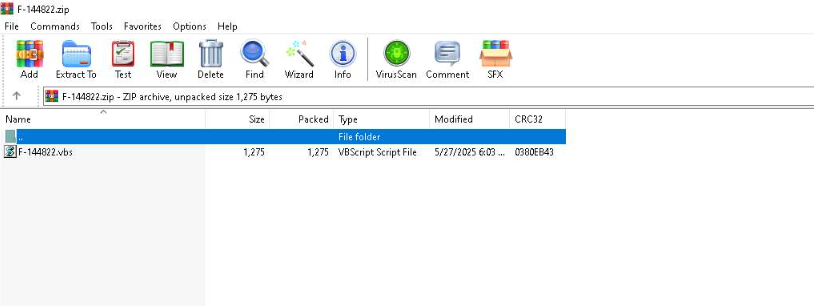
The initial VBS payload downloads a secondary script (cis.vbs) that orchestrates the installation of NetBird and OpenSSH MSI packages without user interaction.
The malware then configures both services for automatic startup and creates a hidden administrative account named “user” with the password “Bs@202122”. This account is added to Administrator groups while being concealed from Windows login screens through registry modifications.
Persistence Through Legitimate Tool Abuse
Following initial compromise, the campaign deploys NetBird using a hardcoded setup key (E48E4A70-4CF4-4A77-946B-C8E50A60855A) to establish encrypted remote access channels.
The malware simultaneously enables Remote Desktop Protocol (RDP) access and adjusts firewall configurations to allow incoming connections.
To ensure persistence across system reboots, the campaign creates scheduled tasks including “ForceNetbirdRestart” that automatically reinitiate services after one-minute delays.
Security analysts discovered the campaign’s infrastructure overlaps with previously documented MuddyWater operations, particularly through the reuse of IP address 192.3.95.152, which appears in Maltrail threat intelligence feeds associated with APT MuddyWater activity.
Additional pivoting revealed multiple related Firebase domains (googl-6c11f, cloud-ed980, cloud-233f9) utilizing identical phishing kits with AES-encrypted redirect mechanisms.
The campaign demonstrates significant operational security awareness by removing NetBird desktop shortcuts post-installation to avoid detection by victims.
Researchers also identified the abuse of AteraAgent.exe, a legitimate remote monitoring tool, in related infrastructure hosted on my-sharepoint-inc.com.
Organizations should implement proactive blocking of identified infrastructure, restrict legitimate remote access tools through application allowlisting, and deploy detection rules targeting VBS execution from temporary directories and suspicious local account creation.
The campaign’s use of legitimate tools and evolving infrastructure highlights the importance of continuous threat hunting and proactive infrastructure mapping to identify emerging attack patterns before widespread deployment.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates