Iran-linked advanced persistent threat group MuddyWater has intensified its operations in 2025 by deploying a suite of custom backdoors and migrating its command-and-control infrastructure to mainstream cloud services concealed behind content delivery networks.
Recent analysis reveals that the group has replaced many opportunistic Remote Monitoring and Management (RMM) intrusions with narrowly targeted spear-phishing campaigns and custom malware families designed for stealth, persistence, and counter-analysis.
New Malware Arsenal – StealthCache and Phoenix
MuddyWater’s latest toolkit includes the StealthCache backdoor and the Phoenix loader, both offering enhanced evasion and modular capabilities.
StealthCache communicates via HTTPS beacons to a custom Python-based C2 server hosted on AWS, using unique endpoints such as /aq36 for tasking and /q2qq32 for error reporting.
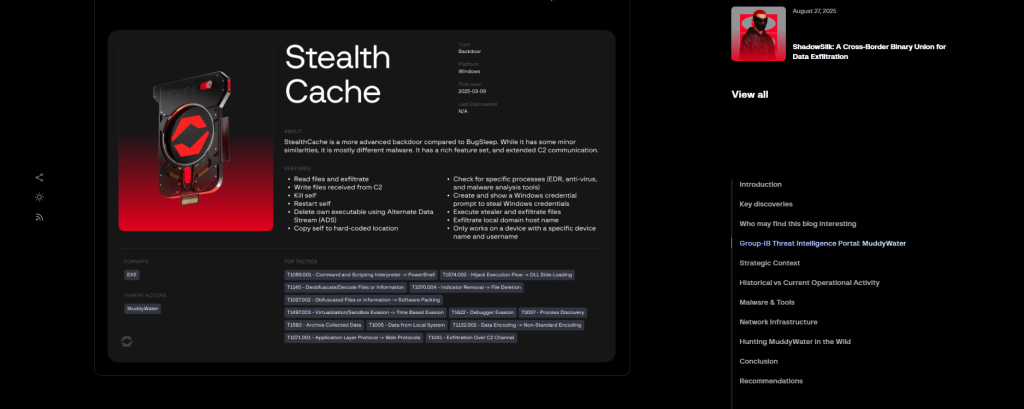
It supports over a dozen commands, including credential harvesting via Windows credential prompts and enumeration of over 250 EDR processes, reporting detected security products without terminating its own execution.
StealthCache also employs alternate data streams to delete its executable (ADS tag wtfbbq) and creates mutexes like DocumentUpdater to avoid duplicate infection.
Phoenix, a minimalistic backdoor, decrypts an embedded PE payload in memory using a simple XOR algorithm. It establishes persistence by copying itself to C:\Windows\System32 via PowerShell and generates a unique machine GUID by concatenating the host and user names.
Phoenix periodically sends “iamalive” beacons and supports interactive shells, file transfer commands, and timeout adjustments through HTTP C2 endpoints such as /register and /request.
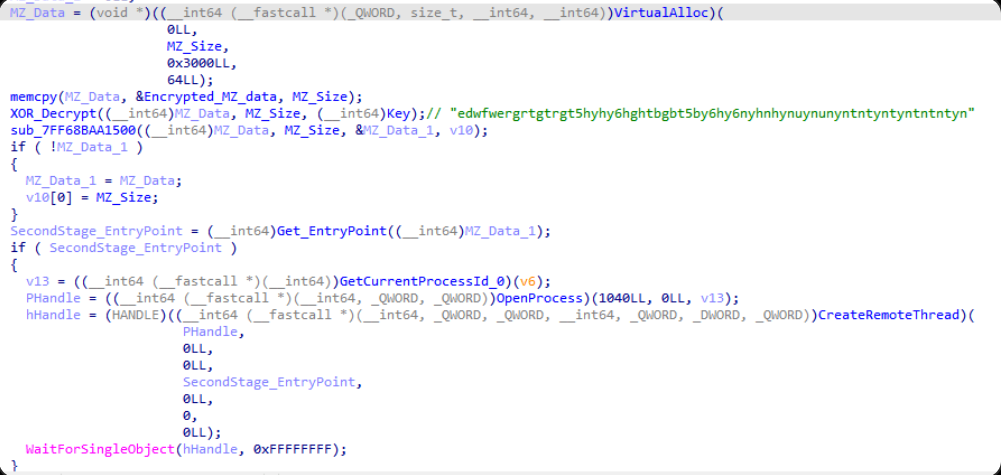
The Fooder loader enables side-loading of malicious DLLs by spawning new threads for payload execution, thwarting automated sandbox analysis.
It decrypts its payload at runtime using the Microsoft Enhanced RSA and AES Cryptographic Provider, deriving keys via CryptHashData and CryptDeriveKey functions, then executing via dynamic API resolution keyed to the host’s device name.
Cloud-Focused Infrastructure for Stealth and Resilience
Infrastructure analysis shows MuddyWater hosting its C2 servers on Amazon Web Services and DigitalOcean, with domains protected by Cloudflare to obscure accurate IP addresses.
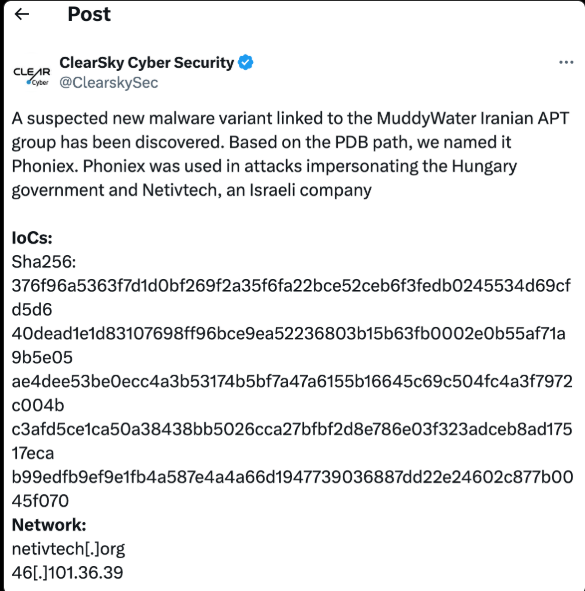
Historical pivoting on the domain netivtech.org revealed passive DNS records transitioning from SEDO hosting to Cloudflare IPs, with TTL-based domain uptime limited to a few days per campaign.
Group-IB identified hosting across mainstream providers like OVH and bulletproof services such as Stark Industries, demonstrating a deliberate mix that maximizes both reliability and resilience against takedown efforts.
Python frameworks Werkzeug and Uvicorn were prevalent in server-side C2 handlers, suggesting rapid deployment capabilities. TLS certificates from Let’s Encrypt and Google Trust Services further reduced the cost and complexity of establishing new C2 infrastructure.
Analysts noted continued use of NordVPN for geofencing evasion, alongside reuse of unique server banners and certificates for attribution.
By combining custom malware that resists static and dynamic analysis with cloud-based hosting cloaked behind CDN services, MuddyWater has significantly raised the bar for detection.
Organizations are urged to strengthen email defenses, disable Office macros, enforce multi-factor authentication, and implement robust monitoring of outbound HTTPS traffic for anomalous patterns consistent with MuddyWater’s known C2 endpoints.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates