Group-IB Threat Intelligence has exposed a sophisticated espionage campaign conducted by the Iran-linked Advanced Persistent Threat group MuddyWater, targeting over 100 government and international organizations worldwide.
The operation leveraged compromised email accounts accessed through NordVPN to distribute malicious Microsoft Word documents containing the Phoenix backdoor version 4, marking a significant evolution in the threat actor’s capabilities and operational tradecraft.
Sophisticated Phishing Campaign Exploits Compromised Email Accounts
The campaign began when MuddyWater gained unauthorized access to legitimate email accounts via a NordVPN exit node in France.
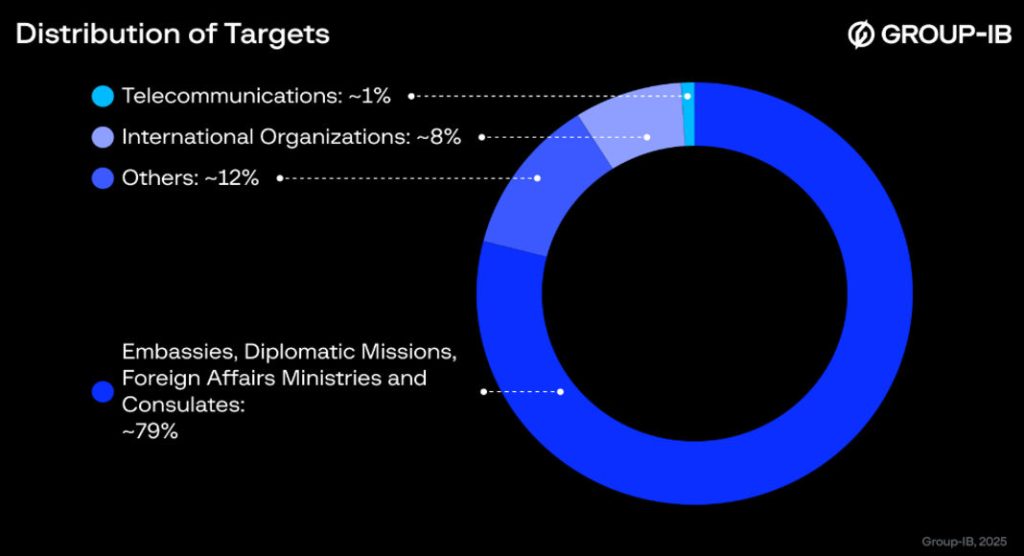
Using these compromised mailboxes, the threat actor sent phishing emails to government entities, diplomatic missions, and international humanitarian organizations across the Middle East, Europe, Africa, and North America.
The emails contained weaponized Word documents displaying blurred content, prompting recipients to enable macros to view the material a social engineering technique that bypassed conventional email security filters.
Upon macro activation, embedded Visual Basic for Application code executed as a dropper, writing a loader identified as FakeUpdate to C:\Users\Public\Documents\ManagerProc.log.
This injector-style loader decrypted an embedded second-stage payload using Advanced Encryption Standard encryption before injecting the Phoenix backdoor version 4 into its own process memory.
The malware then copied itself to C:\ProgramData\sysprocupdate.exe and established persistence by modifying the registry key HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon.
Phoenix Backdoor v4 Enables Full System Compromise and Data Exfiltration
The Phoenix backdoor version 4 demonstrated enhanced capabilities compared to previous iterations. Upon execution, the malware created a mutex named sysprocupdate.exe and gathered extensive system information including computer name, domain membership, Windows version, and username.
Through WinHTTP connections to the command-and-control server at screenai[.]online (IP: 159[.]198[.]36[.]115), the backdoor received commands enabling file upload and download, remote shell access, and configurable sleep intervals for evasive beaconing.
Group-IB identified command mappings including sleep (65), upload file (68), download file (85), start shell (67), and update sleep interval (83).
Infrastructure Analysis Reveals Multi-Stage Post-Exploitation Framework
Analysis of the C2 infrastructure revealed MuddyWater maintained an active attack window between August 19 and August 24, 2025. The screenai online domain was registered via NameCheap on August 17, 2025, and initially operated on Uvicorn before transitioning to Apache on August 24.
The exposed open directory contained additional post-exploitation tools, including a custom Chromium-based credential stealer disguised as a calculator application, PDQ RMM, and Action1 RMM utilities.
The credential stealer targeted browser profiles from Chrome, Opera, Brave, and Edge, extracting encrypted login credentials to C:\Users\Public\Downloads\cobe-notes.txt.
Group-IB attributes this campaign to MuddyWater with high confidence based on the exclusive use of custom malware, matching macro logic from historical operations, identical credential-stealing decoding techniques, and targeting patterns consistent with the group’s geopolitical objectives during ongoing regional tensions.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates