Threat researchers have uncovered a sophisticated, multinational phishing campaign targeting government and financial organizations across East and Southeast Asia, characterized by multilingual lures delivered through ZIP file attachments and powered by a unified automated infrastructure.
The investigation, conducted through Hunt.io’s AttackCapture™ and HuntSQL™ datasets, identified 28 interconnected phishing webpages across three distinct language clusters: 12 Chinese, 12 English, and 4 Japanese, all employing identical backend scripts and deployment mechanisms.
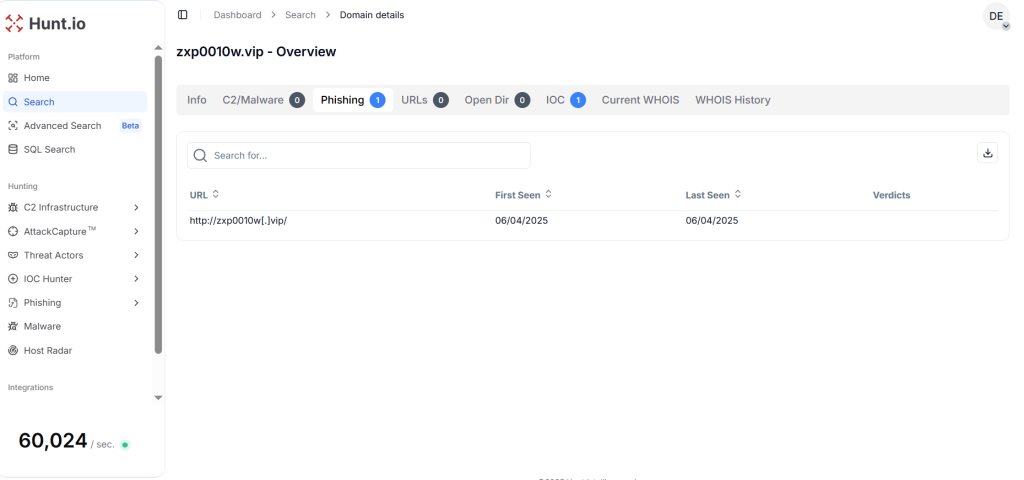
The campaign represents a significant evolution in adversarial tactics, moving from localized phishing waves documented in early 2025 to a regionalized, template-driven infrastructure capable of simultaneous multilingual targeting.
Security researchers traced the operation’s origins to Taiwan and Mainland China before observing expansion into Japan, Indonesia, Malaysia, Thailand, and Cambodia, suggesting coordinated targeting of corporate and governmental entities across multiple jurisdictions.
Shared Infrastructure and Automation-Driven Deployment
Technical analysis indicates that the adversaries operate through a centralized hosting provider, Kaopu Cloud HK Limited (AS138915), which manages infrastructure distributed across Tokyo, Singapore, Hong Kong, Thailand, and Cambodia.
Multiple IP addresses associated with the campaign share identical SSL certificate fingerprints, indicating systematic reuse of infrastructure components.
The unified backend logic uses three critical PHP scripts: visitor_log.php for tracking visitor metadata, such as IP addresses and user agents; download.php for dynamic payload delivery; and force_download.php for enforcing file downloads upon user interaction.
This architecture demonstrates clear evidence of automation-driven deployment, where a single operator or a coordinated team leverages a modular toolkit to generate language-specific variants targeting distinct regional audiences rapidly.
The webpages dynamically retrieve file information from centralized backend servers and display download links only when valid ZIP payloads are available, a design pattern consistent across all 28 identified pages, regardless of language or targeting region.
Multilingual Luring and Region-Specific Payloads
The campaign employs deceptive filenames adapted to each target region’s business environment. Chinese-language pages use Traditional Chinese titles such as “文件下載” (File Download) and distribute archives with bureaucratic themes, “稅務電子發票名單.rar” (Tax Invoice List) and “進出口申報.zip” (Import-Export Declaration).
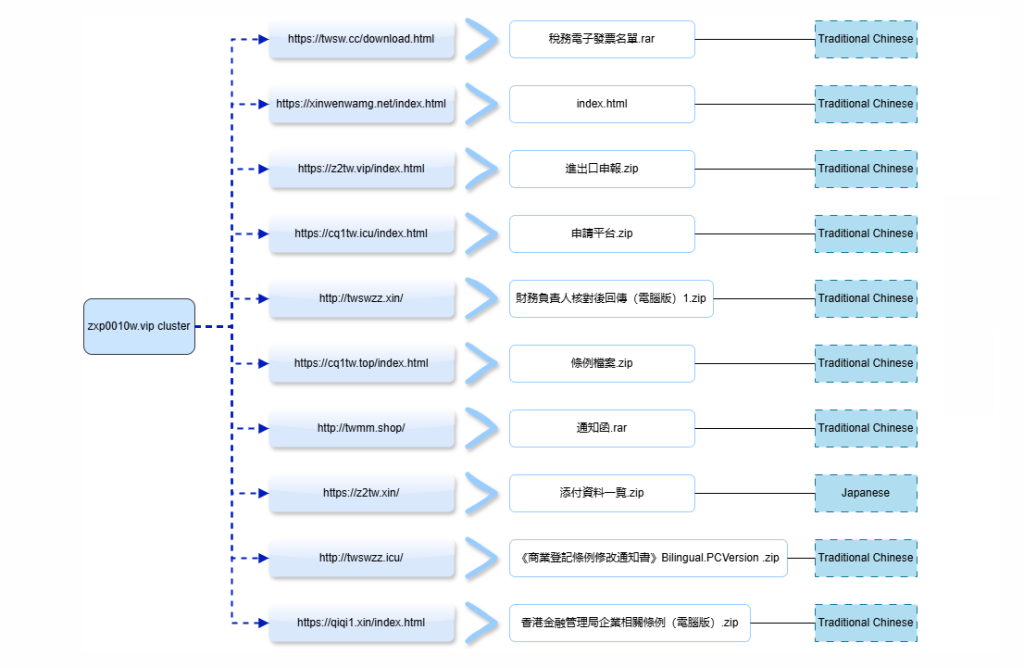
English-language variants incorporate Southeast Asian targeting with filenames like “Tax Filing Documents.zip” and Hindi-labeled payloads, while Japanese pages present “給与制度見直しのご案内.zip” (Notice of Salary System Review) and tax-related archives designed to deceive Japanese corporate targets.
Notably, pages maintain linguistic inconsistencies, with the Indonesian text “Klik untuk melihat lampiran” (Click to view attachment) appearing on Traditional Chinese pages, suggesting deliberate cross-regional targeting strategies to maximize reach across multiple Southeast Asian markets simultaneously.
![domain "jpjpz1[.]cc"](https://cyberpress.org/wp-content/uploads/2025/10/image-283-1024x483.png)
Security organizations should immediately block discovered domains across the .vip, .sbs, .xin, .cc, and .cn extensions, and implement email gateway detection for ZIP/RAR archives with financial, HR, or government-themed filenames.
Organizations are advised to restrict script execution from compressed attachments and deploy real-time infrastructure monitoring using threat intelligence platforms capable of identifying emerging campaigns through backend script patterns and SSL fingerprint correlation.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates