A new cyber-espionage campaign attributed to the China-nexus threat actor Mustang Panda (aka TA416) has been uncovered by IBM X-Force, revealing the use of a refined DLL side-loading technique to target the Tibetan community for politically motivated purposes.
The campaign, first identified in June 2025, employs a multi-stage infection chain initiated via phishing emails that deliver a malicious ZIP archive containing an executable and a stealthily hidden dynamic-link library (DLL).
Hidden DLL and Decoy Loader
The malicious ZIP archive contains a decoy executable, Voice for the Voiceless Photos.exe, referencing the Dalai Lama’s book, and a companion DLL named libjyy.dll.
While the executable is visible to users, the DLL remains concealed by leveraging specific file attributes: read-only, hidden, system, and archive flags (-arhs-).
These settings prevent Windows Explorer from displaying the DLL even when “Show hidden files” is enabled, unless the “Hide protected operating system files” option is disabled.
Upon execution, the decoy loader dynamically loads libjyy.dll through the LoadLibraryW() API and calls its ProcessMain function. This DLL, masquerading under legitimate metadata from “Wargaming.net,” serves as the actual loader of Mustang Panda’s Claimloader malware.
The loader subsequently decrypts embedded strings, dynamically resolves critical Windows APIs, and initiates further payload stages.
Claimloader: Decryption, Persistence, and Shellcode Execution
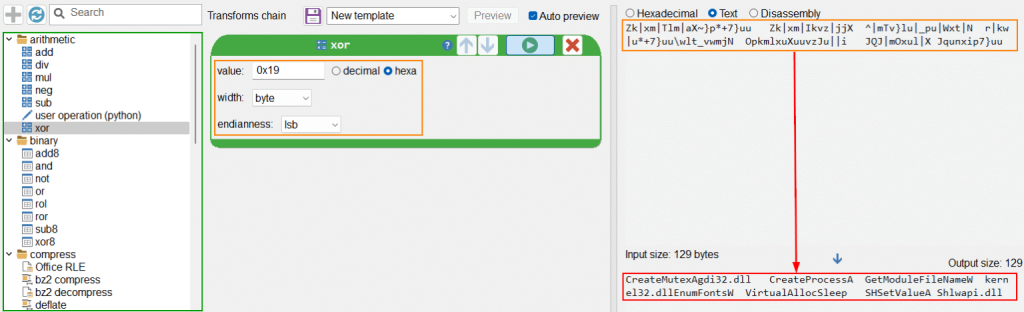
During analysis in Malcat using the Kesakode scanning engine and CAPA capability mapping, Claimloader demonstrated several malicious features, string decryption routines, persistence mechanisms, and shellcode deployment.
The string decryption employs a simple single-byte XOR (key 0x19) to hide API and DLL names, enabling the loader to retrieve necessary Windows functions during runtime through dynamic LdrLoadDll and LdrGetProcedureAddress.
If no execution argument is detected, Claimloader creates dual persistence mechanisms using MITRE ATT&CK techniques T1547.001 (Registry Run key) and T1053.005 (Scheduled Tasks).
It copies itself and the decoy into a fake directory C:\ProgramData\AdobeLicensingPlugin\ masquerading as legitimate Adobe software, and establishes autorun and scheduled task entries to ensure repeated self-execution with the correct argument “Licensing.”
In its second execution phase, Claimloader decrypts and launches an additional shellcode payload (identified as Publoader) into memory.
The shellcode resolves system APIs through PEB walking and ROR13 hashing, mapping DLLs dynamically to evade detection. Once executed, Publoader contacts Mustang Panda’s command-and-control servers to exfiltrate host details and execute remote instructions.
This campaign exemplifies Mustang Panda’s evolving sophistication and consistent reuse of DLL side-loading for covert payload delivery.
Through cleverly hidden binaries, customized string encryption, and multi-layer persistence, the group continues to advance its operational stealth and resilience against forensic detection.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates