Threat actors have been observed using hacked WordPress websites to distribute malicious versions of the genuine NetSupport Manager Remote Access Tool (RAT) in a recent wave of sophisticated cyberattacks.
According to analysts at Cybereason’s Global Security Operations Center (GSOC) Report, these actors have advanced their tactics with the use of the so-called “ClickFix” technique, coupling social engineering with technical evasion to infect endpoints and establish long-term control for post-exploitation activities.
Malicious Delivery Pathway
The attack chain typically begins with users being lured through classic phishing techniques, such as deceptive emails, embedded links in PDFs, and even posts on gaming forums.
Once a targeted user visits one of the attacker-controlled or compromised WordPress sites, malicious JavaScript often hidden in meta descriptions or anchor tags redirects the browser and injects a malicious iframe.
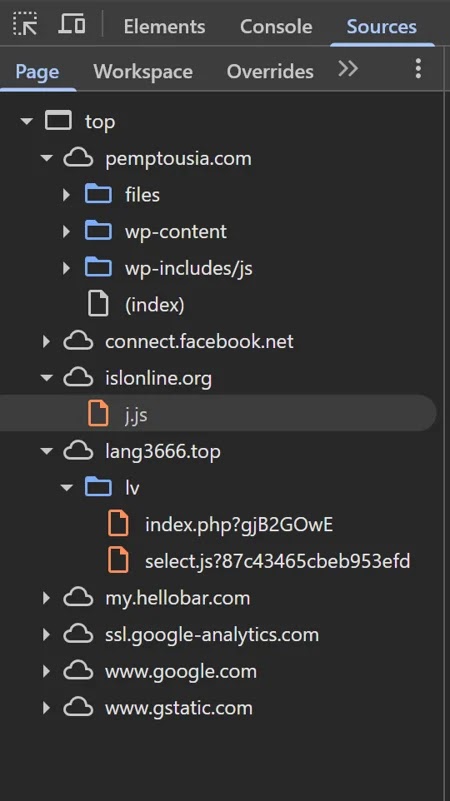
The JavaScript, hosted on domains like islonline[.]org, fingerprints the visitor’s environment and selectively deploys further payloads, targeting Windows users.
The script is highly adaptive: if the user has visited before, it avoids re-infection, masking the attacker’s presence.
If the user is a first-time visitor, an iframe is dynamically generated to pull down an additional PHP script that then loads a third-stage JavaScript, responsible for presenting a fake CAPTCHA challenge.
Social Engineering Meets Technical Abuse
This CAPTCHA page styled with Tailwind CSS and built using React appears wholly legitimate but is a critical part of the attack.
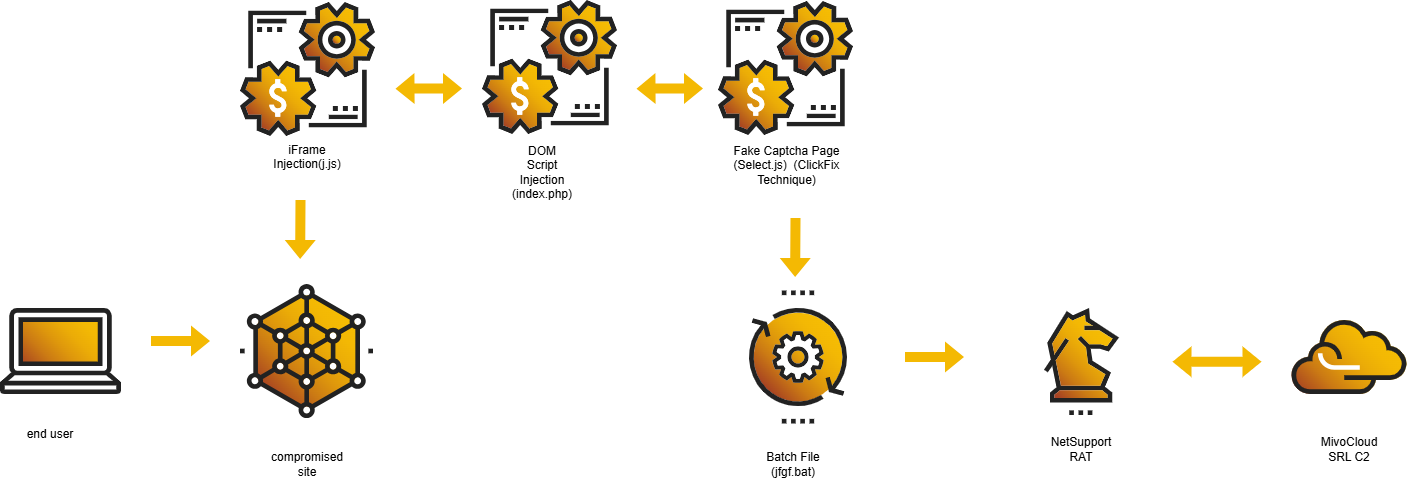
The script behind the page silently copies a pre-crafted malicious command to the user’s clipboard.
Victims, believing they are completing a routine human verification, are prompted to paste and execute this command in the Windows Run dialog.
The result: a batch file (containing obfuscated junk data for evasion) is fetched and executed, extracting a ZIP archive of NetSupport Manager components into the user’s %AppData% directory.
On execution, NetSupport Client establishes persistence via registry keys and cleans up initial artifacts to hinder forensic discovery.
The attack grants the adversaries full RAT access, with capabilities including file transfers, remote shell, and lateral movement.
Post-compromise, security teams observed rapid threat actor interaction sometimes within hours executing reconnaissance commands such as Active Directory enumeration and staging follow-on payloads.
NetSupport Manager, though designed for benign remote management, has become a major threat vector due to its robust feature set and ease of abuse.
Its configuration (client32.ini) directs compromised systems to connect to attacker-operated C2 infrastructure, in this case, IP addresses within the 94.158.245[.]0/24 range owned by Moldovan hosting provider MivoCloud SRL.
These servers were found exposing Remote Desktop and HTTPS services, facilitating robust control channels for adversaries.
Analysts rate this campaign as highly dangerous due to its blend of technical and psychological tactics, wide attack surface, and speed of post-infection exploitation.
Organizations are urged to respond rapidly isolating infected endpoints, acquiring forensic images if data compromise is suspected, resetting user credentials, blocking all associated indicators of compromise (IOCs), and reimaging machines to ensure root-level cleanup.
User awareness, especially regarding suspicious CAPTCHA requests and clipboard-based attacks, forms an essential pillar of defense.
Indicators of Compromise (IOCs)
| IOC | Type |
|---|---|
| 94.158.245[.]104 | IP |
| 94.158.245[.]118 | IP |
| 94.158.245[.]131 | IP |
| 94.158.245[.]137 | IP |
| 172.67.70[.]20 | IP |
| 79.141.173[.]158 | IP |
| 209.17.116[.]165 | IP |
| 23.23.49[.]179 | IP |
| 193.111.208[.]110 | IP |
| 162.214.153[.]12 | IP |
| 50.87.146[.]66 | IP |
| 77.83.199[.]34 | IP |
| 107.180.0[.]222 | IP |
| 83.229.17[.]68 | IP |
| pemptousia[.]com | DOMAIN |
| fmovies123[.]top | DOMAIN |
| badgervolleyball[.]org | DOMAIN |
| islonline[.]org | DOMAIN |
| lang3666[.]top | DOMAIN |
| ace-project[.]org | DOMAIN |
| jakestrack[.]com | DOMAIN |
| christianlouboutin2017[.]top | DOMAIN |
| jaagnet[.]com | DOMAIN |
| 9c4349534c137e3e43fb2e2caf049f9d | MD5 |
| 4f496bfde39ca83644265d8d1d9bc9da | MD5 |
| c05f8ec5afbabc36f1c1366549290ae6 | MD5 |
| 20ed4df3a9c734c1788bd2ca2658aedb | MD5 |
| ee75b57b9300aab96530503bfae8a2f2 | MD5 |
| 1768c9971cea4cc10c7dd45a5f8f022a | MD5 |
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates