Security researchers have successfully breached one of the most widely used eSIM technologies, exposing critical vulnerabilities that could affect billions of devices worldwide.
In a comprehensive security analysis conducted by Security Explorations, researchers demonstrated how they could compromise Kigen eUICC cards, extract private encryption keys, and download arbitrary eSIM profiles from major mobile network operators including AT&T, Vodafone, and T-Mobile.
The research, disclosed in July 2025 after a 90-day coordinated vulnerability disclosure process, reveals fundamental weaknesses in Java Card virtual machine implementations that have persisted since 2019, despite being previously reported to Oracle.
The Security Breach: How Researchers Exploited eSIM Technology
The attack exploited fundamental flaws in the Java Card virtual machine implementation used by Kigen’s eUICC cards, which are embedded in modern smartphones to enable eSIM functionality.
Security Explorations discovered that they could leverage type confusion vulnerabilities—the same class of issues they had reported to Oracle in 2019—to gain unauthorized access to the secure element’s memory and extract critical cryptographic keys.
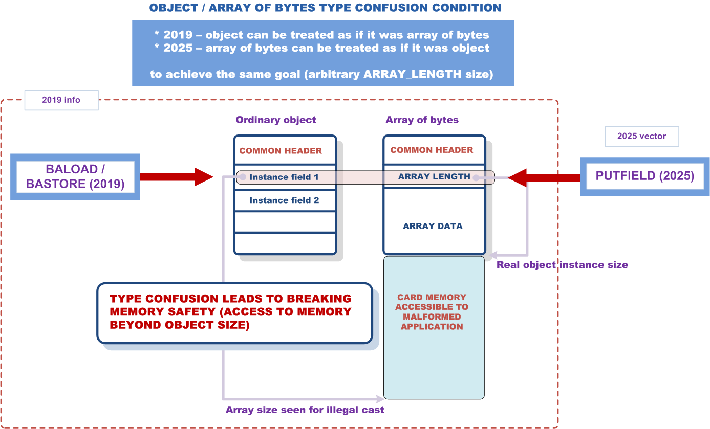
The researchers successfully extracted private ECC keys for GSMA certificates, which are supposed to provide the foundation of trust for the entire eSIM ecosystem.
What makes this attack particularly concerning is its broad impact potential.
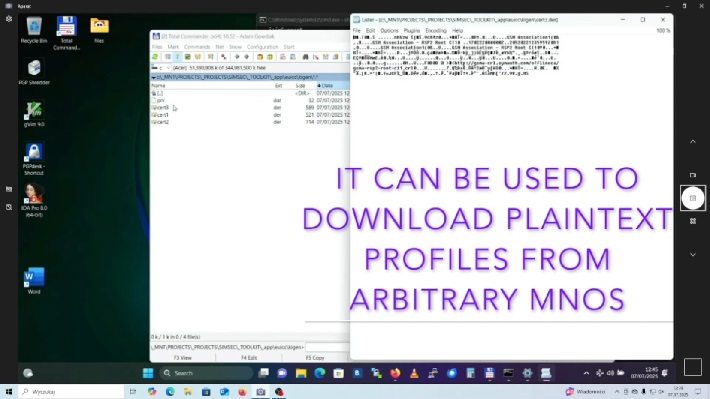
Once researchers obtained a single compromised eUICC identity, they could download eSIM profiles from multiple mobile network operators in plaintext, revealing sensitive subscriber information, network authentication keys, and even Java Card applications embedded within the profiles.
The attack demonstrated that a single breached eUICC could be used to access profiles from operators across different countries, effectively turning one compromised device into a master key for the global eSIM infrastructure.
The researchers also proved that the attack could be conducted remotely through over-the-air (OTA) channels, simulating malicious applet installation via SMS-PP protocol.
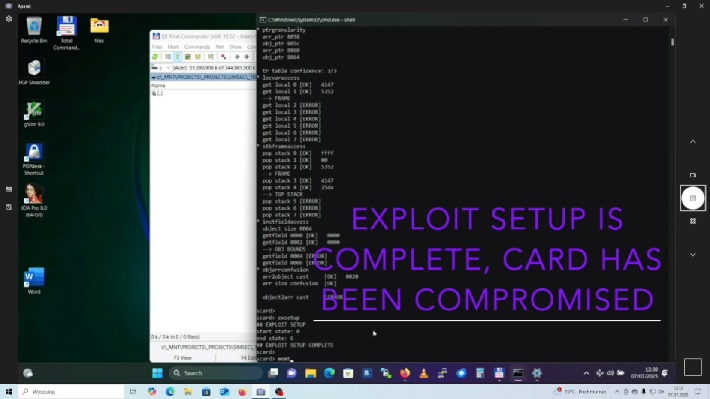
This remote capability significantly amplifies the threat, as attackers wouldn’t necessarily need physical access to target devices to compromise them, provided they have knowledge of the required cryptographic keys.
Key Security Findings:
- Researchers successfully extracted private ECC keys from GSMA-certified eUICC cards, compromising the fundamental trust model of eSIM technology.
- A single compromised eUICC identity enabled downloading of eSIM profiles from over 100 mobile network operators across multiple countries in plaintext format.
- The attack demonstrated successful eSIM cloning capabilities, allowing hijacking of legitimate subscriber phone numbers and interception of SMS-based two-factor authentication codes.
- Remote exploitation was proven feasible through over-the-air SMS-PP protocol, eliminating the need for physical device access in many attack scenarios.
- The vulnerability affects EAL4+ certified hardware, raising questions about the effectiveness of current Common Criteria certification processes for complex software-hardware systems.
Industry Response: Patches and Specification Updates
Following responsible disclosure practices, Security Explorations provided detailed technical information to Kigen beginning in March 2025, receiving a $30,000 reward for their findings.
Kigen responded by developing comprehensive patches that address both the immediate vulnerability and implement broader security hardening measures.
The company classified the vulnerability with a CVSS score of 6.7 (Medium) for physical access scenarios, though researchers argue the score should be 9.1 (Critical) when considering network-based attack vectors.
Kigen’s mitigation strategy includes a two-layer approach: first, operating system security patches that prevent unauthorized remote applet loading when GSMA TS.48 Generic Test Profiles are activated, and second, the implementation of safer test profiles that exclude Remote Applet Management keys by default.
The company has distributed these patches to millions of eSIMs already deployed in the field through over-the-air updates, demonstrating the scalability of their response.
The GSMA organization has also taken significant action by updating the TS.48 Generic Test Profile specification to version 7.0, which addresses the chain-of-trust weakness that enabled unauthorized remote applet management.
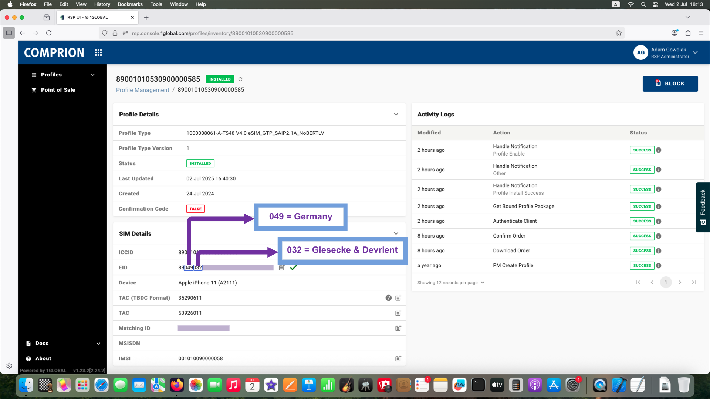
Additionally, GSMA published an Application Note providing industry guidance to prevent misuse of Remote Application Management keys for installing malicious Java Card applications in eUICC devices supporting Java Card technology.
Broader Implications: What This Means for Mobile Security
This security breach has far-reaching implications that extend beyond the immediate technical fix.
The research demonstrates that eSIM cloning is not just theoretically possible but practically achievable, with researchers successfully conducting tests that showed how cloned eSIMs could hijack legitimate users’ phone numbers and intercept SMS messages used for two-factor authentication.
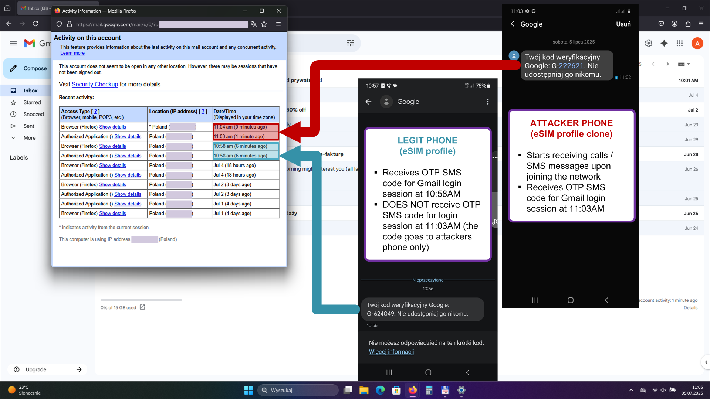
This capability could enable sophisticated social engineering attacks and account takeovers across multiple services that rely on SMS-based authentication.
The vulnerability also raises serious questions about the effectiveness of current certification schemes in the telecommunications industry.
Despite Kigen’s eUICC cards being certified to EAL4+ assurance levels through rigorous Common Criteria evaluations, the fundamental Java Card vulnerabilities that enabled this attack had been known since 2019.
This suggests that current certification processes may not adequately address software-level security issues in complex systems like eSIM implementations.
For mobile network operators and device manufacturers, this incident underscores the need for more robust security practices, including implementing bytecode verification at RSP servers, avoiding shared secret keys across eSIM profiles, and maintaining heightened awareness that eSIM content and applications may be accessible to determined attackers.
The research also highlights the critical importance of independent security research, as the vulnerabilities exploited in this attack had been previously reported to Oracle but were initially dismissed as minor security concerns rather than serious vulnerabilities requiring immediate attention.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates