Researchers from The DFIR Report, working in close partnership with Proofpoint, have identified a new, resilient variant of the Interlock ransomware group’s remote access trojan (RAT) that is being actively deployed in the wild.
Marking a significant departure from the previously documented Node.js-based “NodeSnake” variant, this latest Interlock RAT leverages PHP as its core scripting engine.
Since May 2025, the campaign leveraging this strain has grown increasingly prolific, commonly referred to as “FileFix” by investigators and closely tied to the LandUpdate808 (also known as KongTuke) web-inject threat clusters.
PHP-Based RAT Expands Interlock’s Reach
The attack chain originates from legitimate websites compromised through the injection of a single-line, heavily obfuscated script hidden within the page’s HTML.
Site owners and visitors are typically unaware of the covert compromise. The injected JavaScript is aggressive in its use of IP filtering, ensuring payload delivery only under specific circumstances.
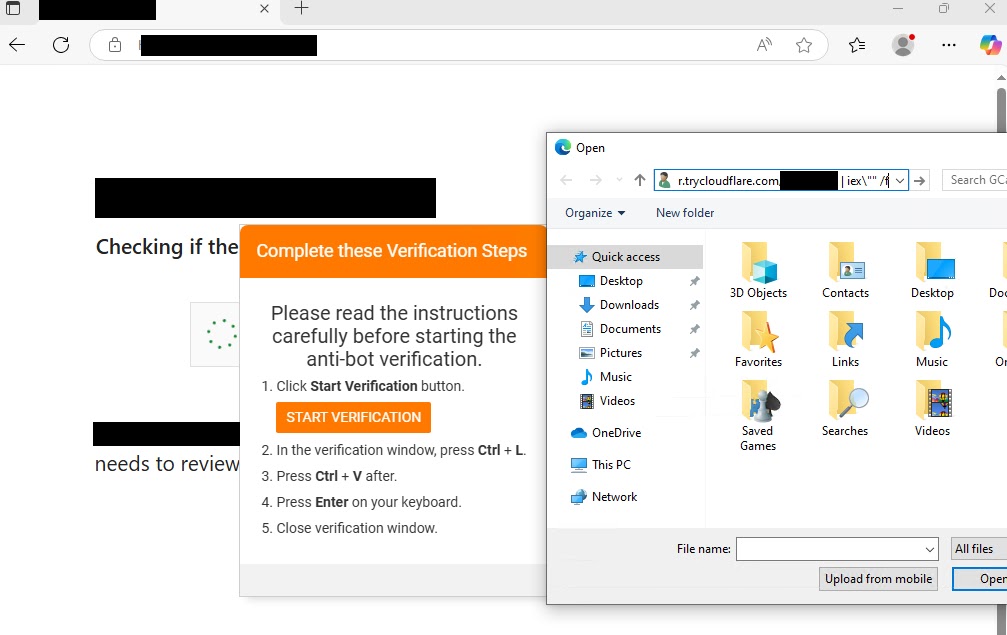
Victims are first prompted with a fraudulent CAPTCHA dialog to “Verify you are human,” followed by a series of “Verification steps,” ultimately instructing them to paste a string from their clipboard into the Windows run command.
If executed, this string triggers a PowerShell script, which then launches the Interlock RAT payload.
While Proofpoint analysts had previously tracked both JavaScript and Node.js variants, this PHP-based Interlock RAT first appeared in campaigns detected in June 2025, and is being distributed in tandem with evolving web-inject techniques.
The migration to a PHP-based payload marks a tactical evolution by Interlock operators, seeking to expand the malware’s compatibility and persistence on compromised Windows environments.
Sophisticated Execution
On execution, the malware employs PowerShell to delete obsolete scheduled tasks, then downloads and executes a command from a Cloudflare Tunnel URL, leveraging the legitimate trycloudflare.com service to conceal command and control (C2) infrastructure.
The RAT is installed as a copy of php.exe in the user’s AppData\Roaming directory, invoked with parameters to load ZIP extensions and a suspiciously located configuration file.
Notably, the malware achieves persistence by registering itself in the Windows Registry “Run” key, ensuring launch on user logon. Once embedded, the RAT conducts aggressive system reconnaissance.
Automated PowerShell commands are issued to collect an extensive system profile in JSON format pulling system specifications, process and service lists, mounted drives, and local network mapping via ARP tables, while also evaluating its own privilege level (USER, ADMIN, or SYSTEM).
Analysts also observed robust “hands-on-keyboard” activity through the PHP executable, including domain enumeration, user and computer object searches via ADSI, domain controller listings, and manual directory probing.
Lateral movement is facilitated primarily via RDP, often following the initial automated discovery phase. The campaign is opportunistic, targeting a wide range of industry verticals.
The C2 channel is made highly resilient by combining Cloudflare Tunnel with hardcoded fallback IP addresses, maintaining attacker access even if primary infrastructure is blocked.
Based on C2 instructions, the RAT can download and execute both executable files and DLLs, establish further persistence, execute arbitrary shell commands, or terminate itself.
The emergence of this FileFix delivery mechanism and the rapid adoption of PHP in the Interlock RAT’s core highlight the continued agility and technical sophistication of the Interlock group.
Security teams are advised to stay vigilant, as further developments and tactics may emerge as the threat actors iterate their tooling.
Organizations are urged to review these IOCs and enhance monitoring for the described behaviors and domains, as this campaign continues to gain momentum.
Indicators of Compromise
| Type | Value |
|---|---|
| SHA256 (Config) | 28a9982cf2b4fc53a1545b6ed0d0c1788ca9369a847750f5652ffa0ca7f7b7d3 |
| SHA256 (Config) | 8afd6c0636c5d70ac0622396268786190a428635e9cf28ab23add939377727b0 |
| Domain | existed-bunch-balance-councils[.]trycloudflare[.]com |
| Domain | ferrari-rolling-facilities-lounge[.]trycloudflare[.]com |
| Domain | galleries-physicians-psp-wv[.]trycloudflare[.]com |
| Domain | evidence-deleted-procedure-bringing[.]trycloudflare[.]com |
| Domain | nowhere-locked-manor-hs[.]trycloudflare[.]com |
| Domain | ranked-accordingly-ab-hired[.]trycloudflare[.]com |
| Fallback IP | 64[.]95[.]12[.]71 |
| Fallback IP | 184[.]95[.]51[.]165 |
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates